Contents:
Most people today have at least some experience with patching. If you own a smartphone, you will be familiar with Android or iOS updates. Same goes with the apps on your phone.
Whether you use banking, travel or social media apps, you’ll occasionally get notifications pushing you to update these tools.
While patching is common, not everyone understands exactly what it is – or why it’s necessary.
And in the workplace, patching can sometimes lead to friction between end users and IT departments. System administrators (sysadmins) may force people to update software and tools, causing disruption and confusion.
Understandably, many people wonder why they have to do this.
Key Takeaways
- Patching helps address known vulnerabilities and secure technology systems.
- Patching can cause disruption and confusion, leading to friction between IT teams and end users.
- Hackers quickly target software vulnerabilities, making it critical to apply patches promptly.
- Effective patch management requires inventory tracking, testing, prioritization, and continuous monitoring.
- Automated solutions can streamline patching, reducing manual efforts and minimizing conflicts with users.
What Everyone Should Know About Patching
Patching is described by the UK government’s cybersecurity center as: “the single most important thing you can do to secure your technology”.
Clearly, patching is important. But to fully understand why, let’s first take a step back and think about the kinds of software and devices you use at work.
As you likely know, all kinds of digital technology runs on code that ‘tells’ the device how to behave. Whether you’re using your company-issued smartphone, a laptop, a printer, a piece of design software, or your company’s fileshare, these technologies are all programmed with code.
Sometimes, the companies who create devices (laptops, printers…), operating systems (Windows, MacOS), or software (project management tools, web browser, email system…) will release new code to update that technology. This new code is often referred to as a ‘patch’.
Patches can do several things:
- Improve the look and feel of the technology;
- Add new features and functionality;
- Improve the technology’s performance;
- Fix bugs, glitches and usability issues;
- Address known vulnerabilities.
It’s the last point in the above list which is arguably the most important. After initially releasing technology, vendors may become aware of weaknesses that malicious actors can use as a ‘backdoor’ into their tools.
As soon as they learn about these vulnerabilities, software vendors will develop a patch which aims to fix this problem.
Once the patch is released, your company’s IT department should – at least in theory – hear about the patch and deploy it.
When software vendors announce they are releasing a vulnerability patch, it creates a kind of arms race.
Malicious actors will now be aware that there is a weakness in a popular piece of software, and they will begin trying to figure out how to exploit that vulnerability.
Now, if you update the software by installing the patch, hackers won’t be able to use that weakness to enter your systems. But, if you fail to install the patch, you could become a target.
Patching Friction: SysAdmins vs. the Business
Patching can cause a lot of friction between IT departments and business users. Common issues include:
- Disruption: Installing patches may require people to turn off devices, close down software, or stop what they’re doing.
- Damage: Some patches may unexpectedly ‘damage’ others apps or systems your company uses or delete files people were working on.
- Misunderstanding: Many people simply don’t understand why they’re being asked to install a patch, so simply ignore emails or intranet pop ups.
- Change: Patches can change the look and feel of software you use every day, which can be confusing. Many people feel resistant to change when they don’t understand its purpose.
- Unsocial hours: Sysadmins sometimes resent having to work nights or weekends to roll out essential patches – just because some of their colleagues don’t want to wait for the update to be installed during the working day.
Patching is actually tough because it is political just as it is technical. I tend to see two patterns. The first is where an admin takes a heavy handed approach and forces patches on people no matter what, and literally causes business impact [with] reboots at the worst possible times. The other end of the spectrum is the admin who is afraid to touch anything.
Why Is Patching so Important?
A vulnerability is an open door, inviting attackers in.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal®
In a recent Inside Out webinar, Heimdal’s Andrei Hinodache listed several major international cyber attacks that disrupted the global economy.
You can check the full webinar below!
Critically, all of these breaches happened when hackers exploited known vulnerabilities in software. This means that the software vendors knew about the weaknesses, and they’d made patches available to fix them.
Nevertheless, many companies failed to install the patches – with disastrous consequences:
- WannaCry: 200k+ machines in 150 countries, resulting in +$4 billion in losses;
- US Voter Registry: 198 million voter records compromised;
- Target Data Breach: 110 million records compromised;
- Equifax Data Breach: 605 million records compromised;
- Marriott Data Breach: 500 million records compromised.
The bottom line is that consistent, effective patching would have helped the organizations who were the victims of these breaches avoid embarrassment, fines and reputational damage.

Now we know why patching is important, let’s go into more detail about what patches are, and how they’re deployed.
What Is a Patch?
A patch is a set of changes to a computer program or its supporting data designed to update, fix, or improve it.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal®
Patches are created by the companies who sell software programmes, operating systems or hardware. Vendors aren’t legally obliged to release patches.
But failing to provide patches could quickly make tech unusable, unpopular and risky – so most providers release patches regularly.
In the past, patches were released physically (for instance, on floppy disks or CDs). But today, they are almost exclusively released online. Your company’s IT department will then download them directly from the software company’s website.
While customers expect vendors to keep releasing patches, vendors may eventually decide to stop offering support for older systems. For example, support for the popular Windows 7 operating system ended in 2020.
Microsoft no longer offers patches, so organizations that still use Windows 7 won’t be protected from new vulnerabilities that get discovered.
What Is Patch Management?
Patch management is the process of maintaining computer networks by performing regular patch deployments.
Andrei Hinodache, Cybersecurity Community Leader, Heimdal®
While technology vendors are responsible for releasing patches, it is down to their customers to actually download and install them. This is part of a process called ‘patch management’.
Proper patch management is complex, with many interrelated activities. In the webinar, Andrei summarized the seven key elements of patch management:
- Inventory: IT departments need to know about all apps and devices being used at the company.
- Vulnerability assessment: IT teams need to know about new vulnerabilities and stay up to date with news about patches for the software the company uses.
- Patch prioritization: Dozens of patches for your software may be released every month. Sysadmins need to work out which are the most important, and which can wait.
- Patch testing: Patches can cause damage to your environment. It’s vital to test patches in a ‘sandbox’ environment (kind of like a ‘clone’ of your company’s actual IT), where you can see if the patch will disrupt other existing systems.
- Scheduling: IT needs to choose the best times to deploy patches without disrupting people’s day to day work (this is often a big cause of friction). Ideally, patches should be deployed at weekends or overnight, but it’s not always possible – especially if the patch is urgent.
- Deployment: This is the rollout of the patch to devices. It’s essential to ensure the patch is deployed everywhere – including on devices that aren’t currently connected to the network (e.g. if someone is working from home).
- Monitoring and reporting: The IT department needs to watch out for patch failures, issues and general operation.
Deep dive: Understand the patch management process
Better Patching with Heimdal®
Heimdal’s patch management software is used by thousands/hundreds of IT departments and sysadmins around the world to deploy patches safely and seamlessly.
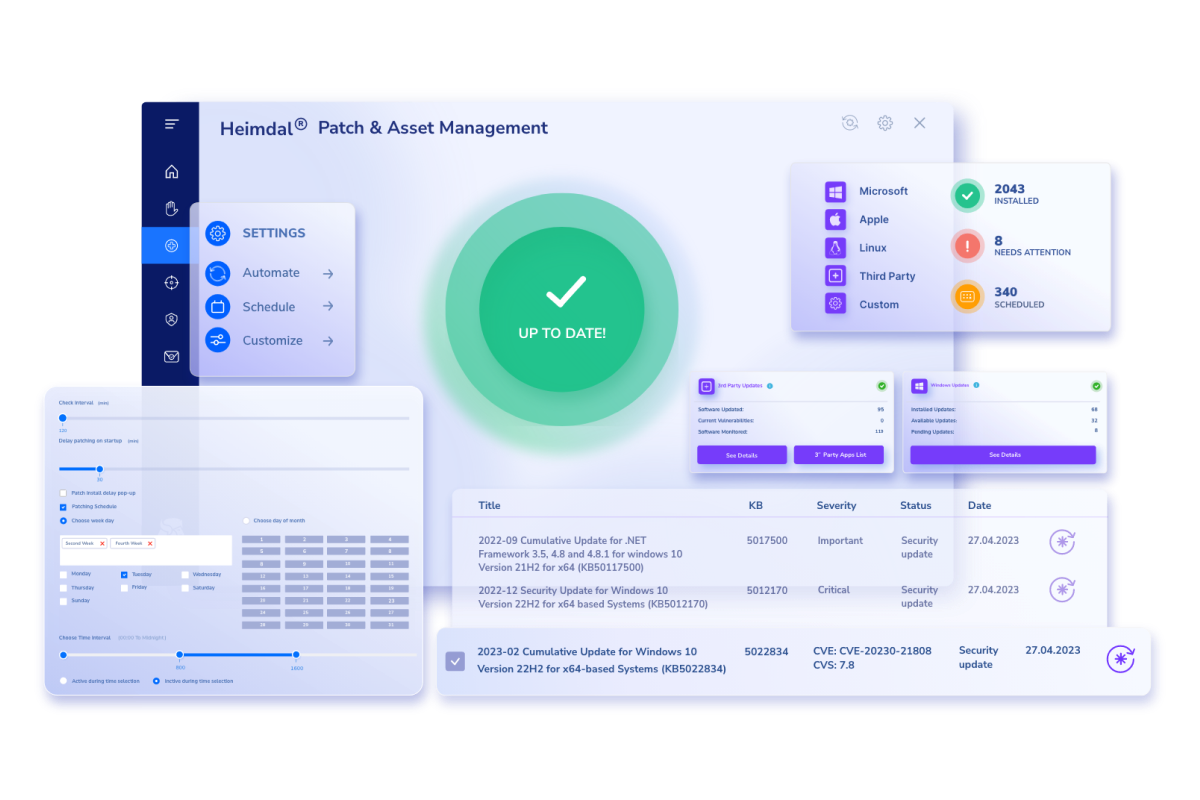
Our solution scans your company’s IT environment to understand which tech you use. It then monitors vendors’ websites, and alerts your sysadmins as soon as new patches are released.
It will then test patches to ensure they’re safe, before rolling them out to all your devices over the internet.
By making patch management automatic, fast and secure, Heimdal reduces the risk of friction with the business, while keeping your data and people safe and secure.
Frequently Asked Questions About Patch Management
Unsure about patching IT systems at work? We answer your FAQs.
Do I need to accept a patch when IT tells me to?
Yes, generally speaking you should. Your company may have its own policy about when and how quickly employees need to accept patches. But it’s generally a good idea to install them as soon as possible. There are many good reasons for installing patches, not least that it reduces your risk of being hacked.
How can IT avoid conflict with the business about patching?
It’s common for end users and IT to clash over deploying patches. One of the best approaches to avoid conflict in this area is through education (feel free to share this blog!). Once end users understand the purpose of patching, most will accept that it needs to be done.
How long does it take to install a patch?
It really depends on the size of the patch, the number of devices it’s being installed on, its complexity, and the complexity of your systems. Individual patches can take anywhere from a few minutes to several hours to install.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security












