Contents:
Open XDR vs native XDR is a recurring question in cybersecurity. Your guide through the decision process should be the company’s specific needs.
Lack of information often makes choosing an XDR solution a slow process. Neglecting XDR because of indecisiveness will end up increasing the attack surface.
An Extended Detection and Response solution (XDR) empowers IT managers in many ways. You don’t want to postpone integrating one in your defense strategy.
Here’s my guide to making the best choice between open XDR and native XDR.
Key takeaways
- assess your company’s needs and profile before deciding between open XDR vs native XDR
- open XDR is vendor-agnostic and helps avoid vendor lock-in
- native XDR offers seamless integration of all security tools
- native XDR is easier to manage and cost-effective
- Heimdal’s XDR platform is a top XDR security choice for MSPs and MSSPs
- XDR software is a crucial component of defending against advanced threats
What is open XDR?
Open XDR, or hybrid XDR, collects and uses data that third-party tools gain from sources like devices, networks, cloud, and emails. Third-party tools are security solutions created and supported by various vendors.
All the threat data, regardless of the tool’s vendor, are correlated and used for detecting vulnerabilities timely
Open XDR is vendor-agnostic. So, it allows organizations to integrate with tools from multiple vendors.
Key benefits of open XDR
Open XDR is beneficial to organizations through:
Flexibility
Open XDR allows organizations to use the best-in-class tools regardless of their vendor. It enables you to cherry-pick from all the available antiviruses, firewalls, access control, and vulnerability management tools on the market.
Thus, open XDR gives access to a wide range of functionalities. It also lets you switch or add to existing tools without service disruption.
Open architecture
With open XDR, your security team can view all IT infrastructures without restrictions. Every cybersecurity team member can access, view, and act on threat data.
Effective for large-size companies
An open XDR platform works for large organizations with multiple tools. Security teams can easily manage all the security tools and complexities involved.
What is native XDR?
Native XDR, or closed XDR, integrates security tools from the same vendor.
For example, an organization will buy and use their AV, DNS security, privileged access management, etc. from one vendor.
Key native XDR benefits
Native XDR benefits organizations through:
Seamless integration
Since there is a single vendor, native XDR tools connect without manual configurations. The tools exchange data without disruptions.
Tools from a single vendor are often designed to communicate automatically. This speeds-up incident response in case of a cyberattack.
Optimized performance
Each tool that a native XDR solution includes covers a different security layer. Each has its configuration and goal, but are designed to work together seamlessly. This enhances the company’s security posture by providing effective layered security.
Use of limited resources
Native XDR solutions are best suited for an organization with a small security team. Streamlining and having all the tools in the same dashboard makes handling security operations easier even for a 2-person security team.
Open XDR vs. native XDR: A detailed comparison
Both open XDR and native XDR offer extended detection and response capabilities. Yet, their approaches are distinct in terms of:
Integration
Open XDR
This XDR approach integrates with third-party security tools from multiple vendors. Organizations can achieve this by using APIs (application programming interfaces).
Companies can use this kind of XDR platform to create custom workflows and automate responses from all vendor tools.
Open XDR platforms collect data in unstandardized formats from multiple sources. Thus, for an accurate analysis, they must normalize the data afterward.
The open XDR solution can be problematic as tools might not interoperate, making the platform harder to use.
Native XDR
Native XDR works within a single, seamless ecosystem. Vendors design all security tools to interoperate for fast threat detection.
Unlike open XDR solutions, it is not complex to configure. The tools within the solution are part of a unified platform and have pre-built integrations.
Native XDR generates data in a standardized format, although it uses homogenous data sources. This feature eases data correlation and analysis.
Deploying and managing native XDR is easier because its components work well together by design. This interoperability makes setup and maintenance a simple task.
Performance and Optimization
Open XDR
This solution is not optimized and might raise performance concerns for companies. Thus, data-related processes like normalizing and correlation across multiple tools are more time-consuming.
This can further lead to performance bottlenecks or high latency. The existence of multiple vendor tools means that data quality will differ.
Inconsistent security data quality can complicate platform performance optimization. So, you might need to adjust initial integrations to achieve optimal performance.
Native XDR
Vendors optimize from the beginning this type of XDR solution to handle all data-related processes. Threat data handling occurs within a single vendor’s ecosystem.
Thus, the platform needs fewer manual adjustments to perform at a high-quality level. It’s an advantage that its pre-optimized security data pipelines and processing algorithms offer.
Also, native XDR eliminates the weaknesses of siloed security tools.
Cost considerations
Open XDR
Organizations pay for licensing and infrastructure before deploying open XDR. Paying these upfront costs cannot be postponed.
Open XDR licensing fees vary because there are many third-party security tools. Licensing costs for AP development, tool connectors, and custom integrations add up.
Infrastructure costs cover hardware and software, as well as consulting and setup.
Users pay upfront for the open XDR solution’s design, setup, and configuration.
Long-term financing focuses on the maintenance and support of each security tool. It extends to the management and optimization of existing security tools.
Native XDR
The upfront cost of the native XDR solution covers subscriptions and deployment. It also covers integration and infrastructure.
For example, an organization’s subscription can be per-user or per-GB-based.
Once you buy the XDR tools, expect future costs for monitoring, upgrades, and maintenance.
Scalability and futureproofing
Open XDR
Organizations can scale with open XDR by:
- Integrating other security tools into their open XDR platforms. This can help them keep up with detecting emerging, more complex, new advanced threats.
- Adopting cloud resources to grow their security infrastructure.
- Creating custom workflows. This customization feature allows efficiency, which leads to growth.
- Avoid vendor lock-in.
- Accessing better prices for financial sustainability.
- Making better decisions through threat data from different sources.
Native XDR
Organizations can scale with native XDR through:
- Using a unified and streamlined solution like Heimdal’s. Heimdal’s native XDR is a good example of how unification helps bolster a company’s security posture.
Speaking of why cybersecurity centralization is important, Morten Kjaersgaard, Heimdal’s founder, says
unification simplifies management and enhances security by offering a broad range of integrated services within a single platform, making it easier for customers to manage their security infrastructure
- Built-in scaling capacities within a vendor’s ecosystem. Organizations can use more tools without compatibility issues.
- Support for cloud and hybrid environments. Native XDR allows organizations to scale their security operations into the cloud.
- Continuous vendor updates and platform optimization. This helps companies learn the latest security features and threat intelligence requirements.
- Predictable updates that minimize disruptions and maximize performance.
- Insights from a single vendor that serves as an organization’s roadmap for growth.
- Pre-configured and optimized workflows that fit an organization’s needs. It also automates threat detection and response.
- Smooth integration with new features without third-party intervention.
- Easy learning, management, and operation for security teams. A sole platform for management helps security teams stay focused and efficient.
- Dedicated support from a security vendor. This involves training and technical guides on the platform.
- When to choose open XDR or native XDR – The use cases
Let’s see how all the information I shared above fits in real-life situations. Why and when should you choose using open XDR instead of native or the other way around?
Open XDR Use Case – Global Manufacturing Company with a Diverse Security Stack
Imagine a large manufacturing company that operates across several continents. It manages various plants, offices, and R&D centers. Each location uses different security tools tailored to local regulations and specific risks. The IT security team oversees more than 20 security solutions. That includes endpoint protection, network monitoring, and cloud security tools from various vendors.
Why choose Open XDR?
- Best-in-class dedicated solution – The company wants the best tool on the market for each specific function. Open XDR allows them to integrate tools like firewalls, threat intelligence, and EDR from different providers, to get the strongest protection in each area.
- Avoiding vendor lock-in – Being able to swap or upgrade individual tools regardless of vendor helps the company scale and pivot in case they need new technology to prevent new threats.
A key difference from native XDR
Flexibility – Open XDR enables the IT team to combine tools from different vendors. Native XDR must stick to a single vendor for all security needs.
Native XDR Use Case – Mid-Sized SaaS Provider Centralizing Security
A mid-sized software-as-a-service (SaaS) provider offers cloud-based services to clients worldwide. As the company grows, managing separate security tools for cloud monitoring, endpoint protection, and threat detection becomes a challenge for its limited IT security team.
Why choose native XDR?
- Single vendor means seamless integration – The SaaS provider opts for native XDR, which integrates endpoint detection, network security, cloud protection, and threat intelligence. Having it all under the same vendor’s umbrella eliminates the need to manage multiple separate solutions.
- Unified threat management – The IT team can monitor and respond to all security events from one platform. Native XDR automates incident response and correlates threat data without manual integration between tools.
- Cost efficiency and vendor support – With Native XDR, the company consolidates security spending. This choice cuts the cost of multiple tool licenses. The unified system also means easier vendor support and more streamlined troubleshooting.
Key Difference from Open XDR
Simplicity – Native XDR provides an all-in-one solution. This makes it easier for the IT team to install, use, and maintain the security software. In contrast, Open XDR needs the team to manage various vendors and tools by hand.
Common challenges of open XDR and native XDR
Some open XDR challenges include:
Integration complexity
Integrating multiple security tools into a single open XDR platform might be difficult for security teams. The complexity might result from each tool’s peculiarity.
Multiple security solutions can also complicate the integration process in terms of:
- compatibility
- costs
- deployment
Solution: To fix this, organizations should choose vendors with integration support. Security teams can also integrate tools in phases if they have enough resources.
Vendor relationship management
Managing relationships with existing security stack vendors can be draining. The same applies to managing their updates and licensing.
Solution: Organizations can minimize the burden of vendor relationship management by reducing vendors. Only vendors that offer core security products should remain.
Organizations can also set up centralized platforms for vendor management. The platform will track all current interactions with security tools.
Cost issues
The cost of buying, implementing, and maintaining the XDR software is high.
Solution: Cut costs by avoiding paying for duplicates of your existing solutions. Also, conduct a cost-benefit analysis to ensure each tool’s benefit matches its cost.
Some native XDR challenges include:
Vendor lock in
Organizations’ XDR tools are tightly integrated within a vendor’s ecosystem. This can cause organizations to experience vendor lock-in.
It is impossible to switch vendors abruptly. This could be due to pricing, or the number of tools involved.
Solution: Research a vendor’s roadmap before onboarding. Agree to flexible contract terms for future vendor changes in the process.
Third-party integration issues
This XDR solution does not support third-party integrations. An organization is thus limited to using only the tools in its vendor’s ecosystem.
Solution: Ask a vendor to support integration with essential third-party tools. Use middleware solutions that connect native XDR with non-vendor tools.
Vendor’s insights
The updates or new features that the vendor brings might not match an organization’s needs.
Solution: Collaborate with your vendor and ask for updates that match your needs.
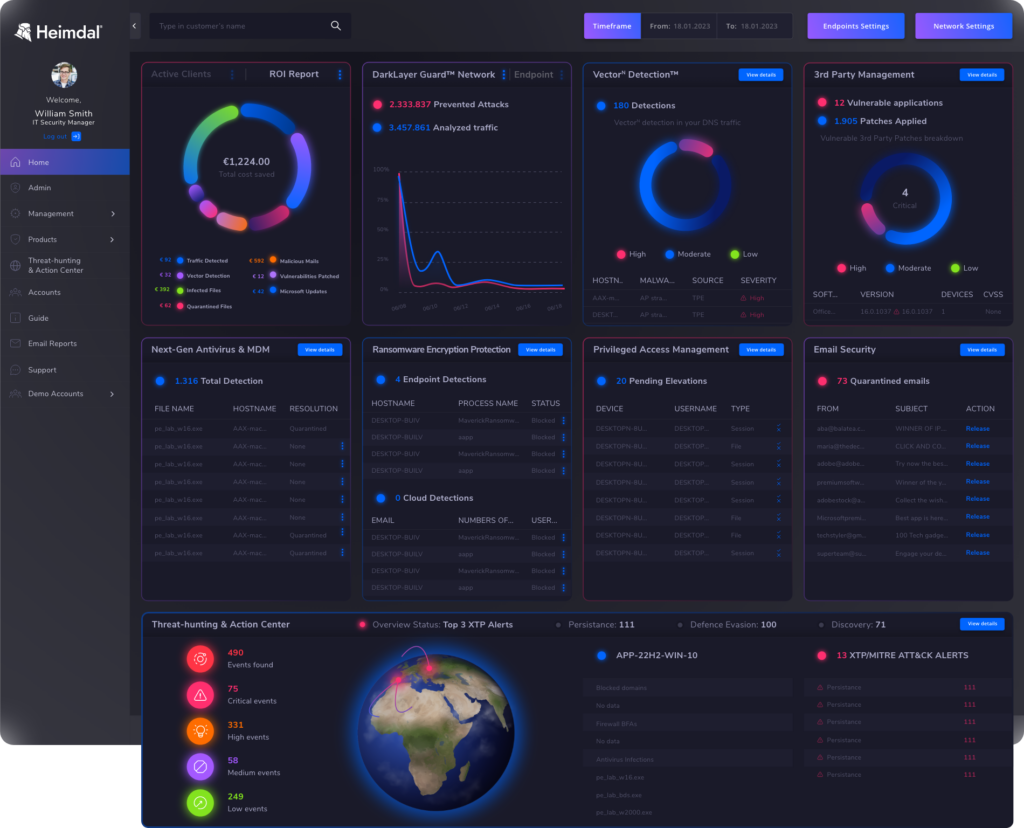
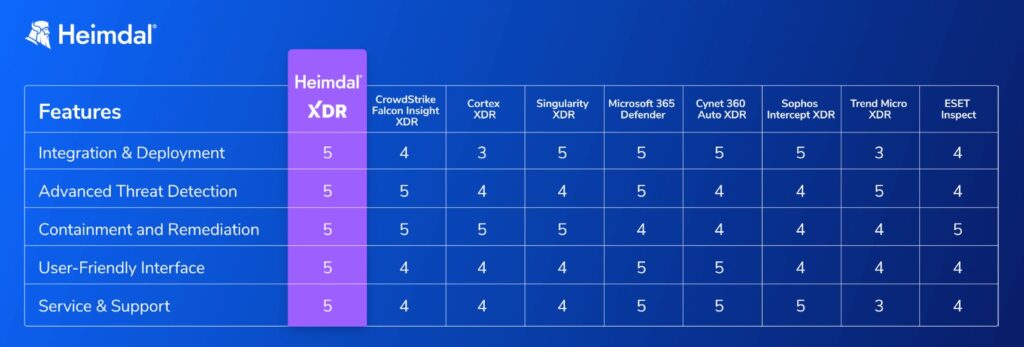
Why use Heimdal® XDR for security operations?
Combining advanced threat detection with seamless integration, Heimdal® XDR empowers organizations to stay ahead of evolving cyber threats. By unifying security tools and offering intuitive management capabilities, it makes it easier to protect your infrastructure. This platform is also the best XDR security choice for MSSPs.
Here’s why Heimdal® XDR stands out:
AI-powered threat detection
Use the power of artificial intelligence and machine learning to identify and neutralize threats with precision.
Integrated threat hunting
This capability enables your security team with pre-computed risk scores, indicators, and detailed attack analysis. It’s a valuable heads-up in case a threat arises and empowers the team to provide faster incident response.
Centralized management
Access and manage all Heimdal security tools from a single, user-friendly platform.
Cost-effective security
Get tailored security solutions that meet your needs without overpaying.
Easy-to-use interface
Simplify daily security tasks with an intuitive platform built for efficiency and ease of operation.
24/7 Support
Rely on expert support for any questions, updates, or system adjustments.
XDR FAQs
Why should an organization use XDR?
Use XDR for threat detection and response in all security environments. Also, XDR is great for yielding increased ROI on security products.
What is the difference between XDR and EDR?
XDR is a multilayered platform for threat detection and response. It collects data from different environments: endpoints, networks, email, and cloud. EDR detects and responds to endpoint threats only. It only collects data from endpoints.
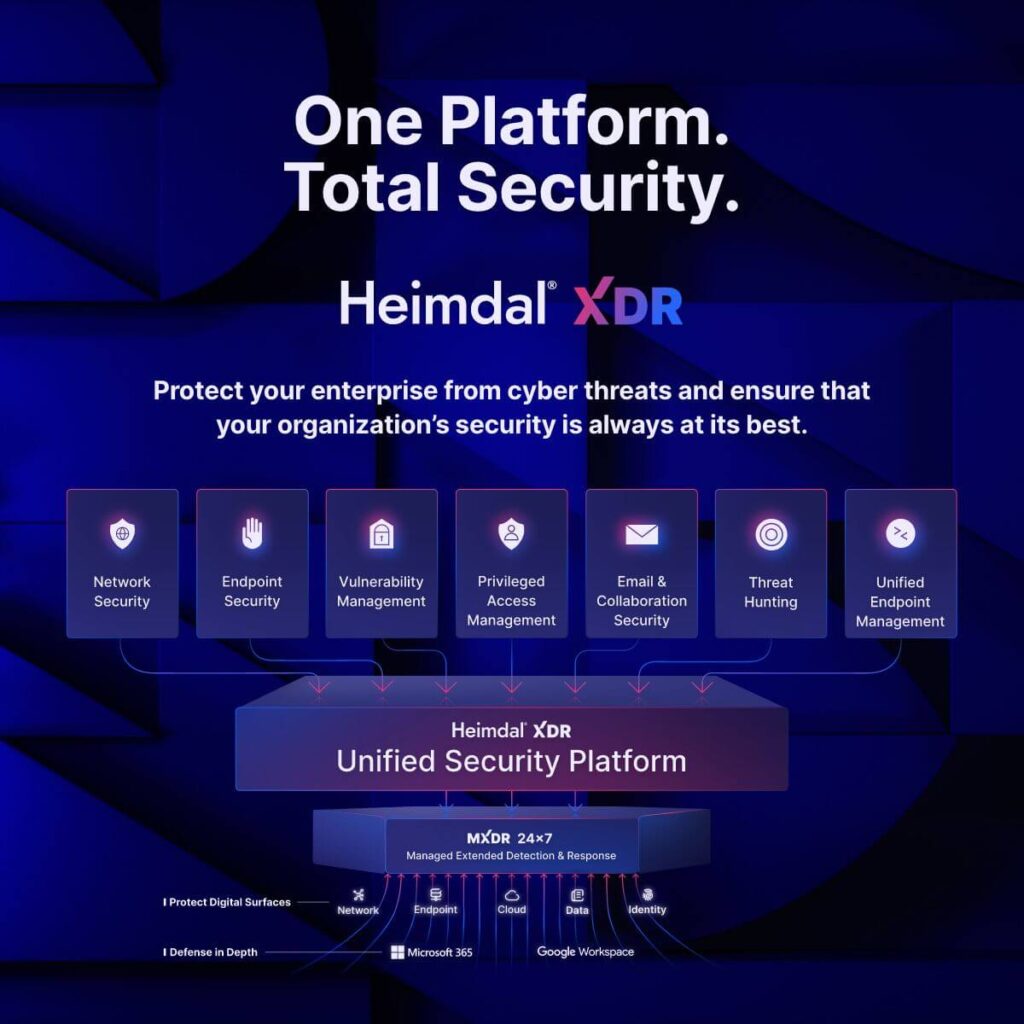
How does Heimdal® XDR work for security teams?
The Heimdal XDR platform has 10 integrated security solutions. Organizations can use them to prevent ransomware, lateral movement, DNS poisoning, malware deployment, and data exfiltration.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security