Contents:
Analysts from Checkmarx uncovered a number of attacks on the banking industry’s open-source software supply chain in the first half of 2023. According to the experts, these attacks targeted specific components of web assets used by banks and employed sophisticated techniques.
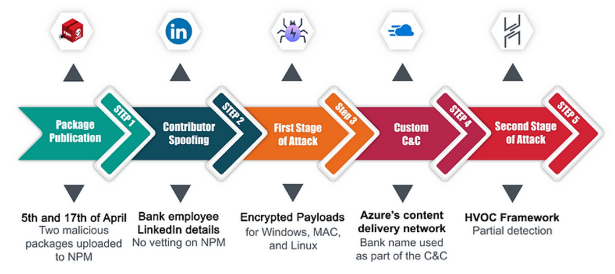
On the 5th and 7th of April, a threat actor leveraged the NPM platform to upload a couple of packages containing within them a preinstall script that executed its malicious objective upon installation.
How Did the Attacks Happen?
The hackers used phony LinkedIn profiles to contact the victims’ employees and a unique C2 for each target. The specialists found a connection between the perpetrator of the malicious packages and the LinkedIn profile of a person pretending to be an employee of the victim.
In order to initiate the multi-stage attack chain, the two malicious npm packages used in the April 2023 attacks came with a preinstall script. The script determined the host operating system (Windows, Linux, or macOS) and downloaded the second-stage malware from a remote server using Azure’s CDN subdomain that included the name of the bank in question in the first stage.
Using Azure’s CDN subdomains, attackers can avoid detection and traditional deny list solutions.
The second-stage payload, the Havoc Framework, includes post-exploitation capabilities similar to other popular hacking tools such as Cobalt Strike, Sliver, and Brute Ratel.
Analysts Predict More Targeted Attacks
In a second incident spotted by the company in February 2023, the cybercriminals went after another bank. The attackers deployed a malicious npm package containing a carefully crafted payload to blend into the victim bank’s website and stay dormant until activated.
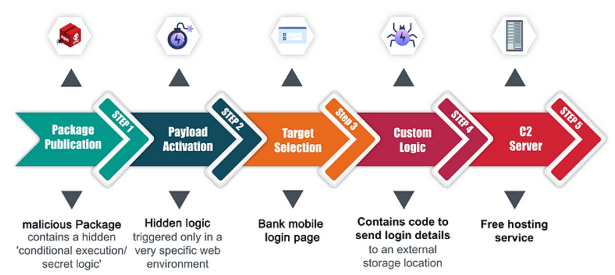
The payload revealed that the attacker had identified a unique element ID in the HTML of the login page and designed their code to latch onto a specific login form element, stealthily intercepting login data and then transmitting it to a remote location.
Experts have concluded that the two attacks are unrelated, and the affected npm packages have been removed. These packages’ names were not revealed, explains Security Affairs.
However, according to Checkmarx, the frequency of targeted attacks, including those on financial institutions, will continue to rise.
The Indicators of Compromise (IoCs) for these attacks are also included in the published report.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










