Contents:
Intezer researchers have recently discovered a sophisticated spear-phishing campaign targeting large international companies in the oil and gas sector. The campaign has been underway for over a year, spreading common remote access trojans (RATs) for cyber-espionage purposes.
The Process
As reported by Threat Post, cybercriminals used spear-phishing emails with malicious attachments to drop RATs on infected machines, including Agent Tesla, AZORult, Formbook, Loki, and Snake Keylogger. These trojans can steal sensitive data, financial information, and browser information, and logging keyboard strokes.
According to the researchers,
The contents and sender of the emails are made to look like they are being sent from another company in the relevant industry offering a business partnership or opportunity. Each email has an attachment, usually an IMG, ISO or CAB file. These file formats are commonly used by attackers to evade detection from email-based Antivirus scanners. Once the victim opens the attachment and clicks on one of the contained files an information stealer is executed.
Although oil and gas companies are the main targets of this spear-phishing campaign, the threat actors have also gone after IT organizations, manufacturing, and media sectors around the world, including in Germany, United Arab Emirates (UAE), the United States, and South Korea.
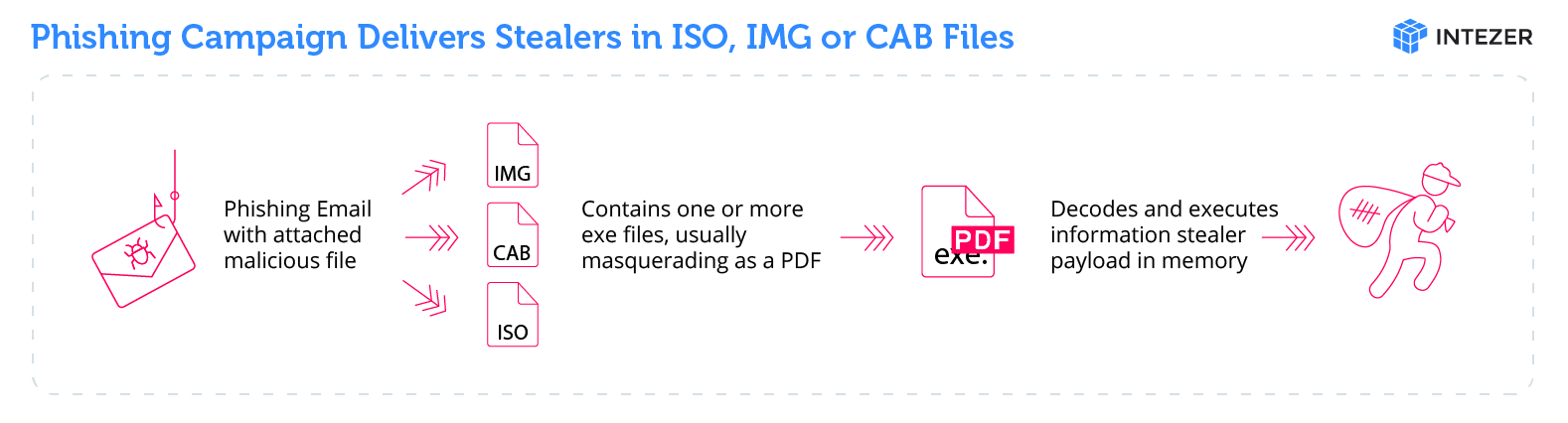
Image Source: Intezer
FEBC, a religious Korean Christian radio broadcaster is one of the targeted countries. The company’s case is different and may offer a clue as to the nature of the threat actors. FEBC reaches other countries outside of South Korea, many of which downplay or ban religion. One of the company’s goals is to subvert the religion ban in North Korea.
The Emails
As explained by the researchers, in this spear-phishing campaign the threat actors send emails tailored to employees at each targeted company. The recipient email addresses range from generic email handles (info@target_company[.]com, sales@target_company[.]com) to specific people within companies, suggesting varying levels of reconnaissance work on targets.
The emails use social engineering tactics like making references to executives, using physical addresses, logos, and emails of legitimate companies.
To make it seem even more legitimate and familiar to the targets, the email addresses used in the “From” field are typosquatted or spoofed, meant to look like emails from actual companies.
Typosquatting involves creating phishing websites with similar names to the target site, hoping that users who manually type in the address will make a mistake and end up on the cybercriminals’ page.
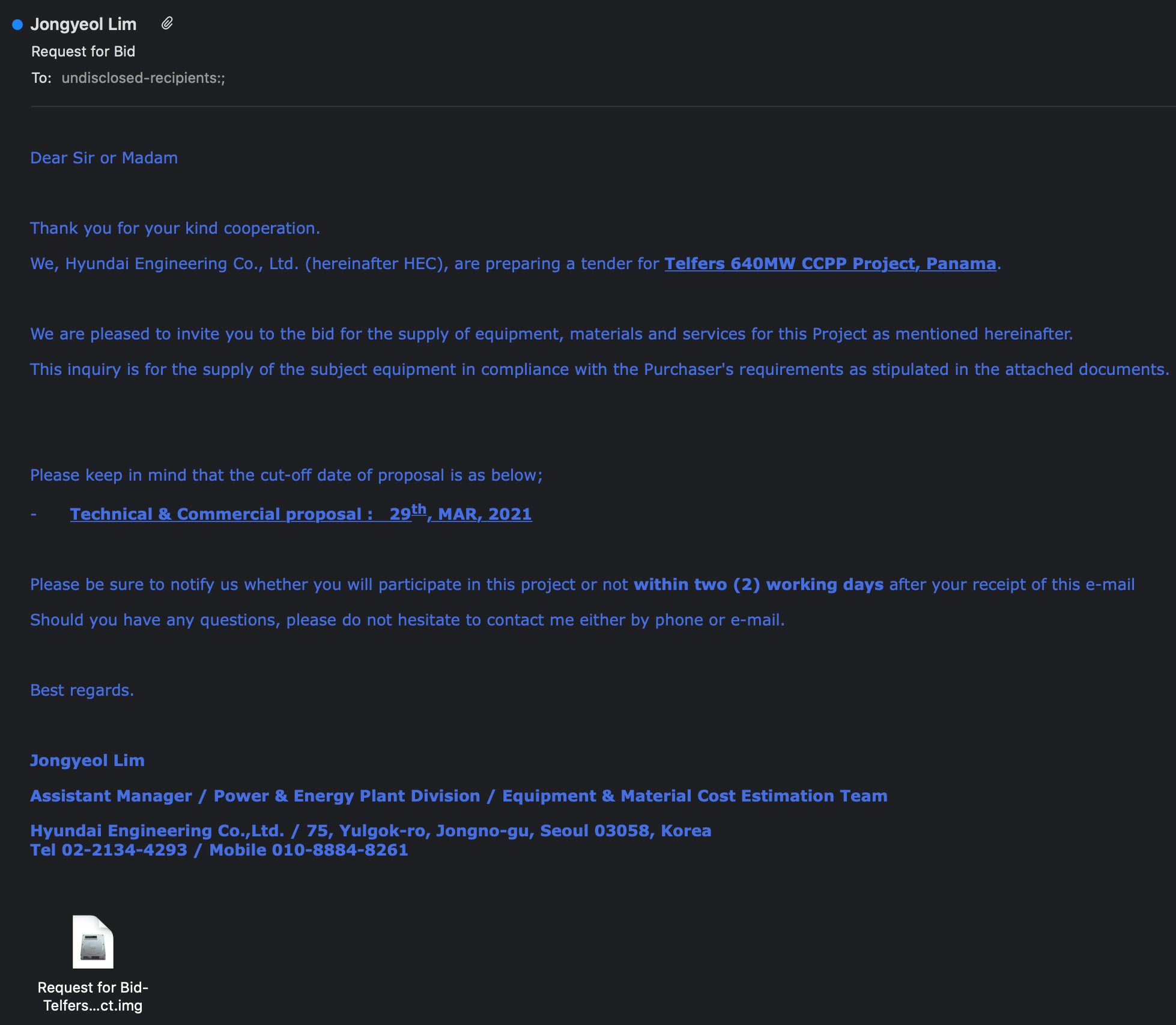
Image Source: Intezer
In this spear-phishing campaign, many of the typosquatted domains mimic South Korean companies with legitimate domains in the format of <company.co.kr>. Typosquatting is achieved by registering a domain without the second level “.co” and instead registering the domain as <company-co.kr>. One example of this is the domain <hec-co.kr>, registered by the attackers to typosquat the legitimate domain for the company Hyundai Engineering (hec.co.kr).
According to Intezer, the emails have a malicious attachment with a seemingly complementary name related to the contents of the email body. In reality, it contains .NET malware, usually an .IMG, .ISO or .CAB file, commonly used by attackers to evade detection from email-based antivirus scanners.
Nevertheless, in an effort to look less suspicious, the files are disguised as PDFs, using fake extensions and icons. Once the user double-clicks on the file, the content is mounted, and the user can click the file to be executed.
To bypass detection from standard Antiviruses, the execution of the malware is fileless, meaning that it is loaded into memory without creating a file on disk. In this case, it performs the same loading and execution process used to load Agent Tesla.
Countering Spear-Phishing Attempts
Below, you will find a list of actionable spear-phishing campaign countermeasures you can start implementing right away.
Continuous cybersecurity education
When it comes to preventing any type of cyberattack, education is key. When receiving emails that purportedly come from a legitimate source, you must ask yourself if the actions suggested in the mail’s body could compromise your company’s security.
The best approach is to analyze the attachments before opening them. If they are true documents, why should they have a .exe extension? Additionally, when receiving such requests, you should confirm them with your case manager or your CEO.
Upgrade your cyber-defenses
Agent Tesla and other RATs need C&C servers to operate. The best way to counter this is DNS traffic filtering. More specifically, you will need a solution that effectively blocks the malicious connection to the server before sanitizing your device.
Heimdal™ Threat Prevention, Heimdal™ Security’s response to second-generation malware can root out the malicious packets hidden within a transmission and sever the connection to the Command & Control servers the hackers use to steal data from compromised devices.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










