Contents:
Secure email gateways and security software are becoming more and more advanced in an attempt to adapt to the ever-changing phishing campaigns and for this reason, the threat actors are resorting to more unusual file formats when trying to bypass detection, therefore phishing scams made the switch to more unusual attachments like ISO or TAR files.
The researchers at Trustwave explain in a recent report the way in which threat actors are starting to utilize WIM (Windows Imaging Format) attachments in order to distribute the Agent Tesla remote access trojan.
All the WIM files we gathered from our samples contain Agent Tesla malware. This threat is a Remote Access Trojan (RAT) written in .Net which can take full control over a compromised system and can exfiltrate data via HTTP, SMTP, FTP, and Telegram,” explains Trustwave security researcher Diana Lopera in the report.
The phishing campaigns are launched with emails that are pretending to be shipping information from DHL or Alpha Trans and include WIM attachments that are designed to bypass security software.
The Windows Imaging Format (WIM) represents a file-based disk image format that contains a set of files and associated filesystem metadata.
What Are WIM Files?
WIM files are able to contain multiple disk images, and due to the use of single-instance storage, the more each successive disk image has in common with previous images added to the WIM file, the less new data is to be added.
An interesting fact about WIM images is the fact that they can be made bootable (WIMBoot), as the Windows boot loader supports booting Windows from within a WIM file.
It’s worth noting that while the WIM files could be less likely to be detected, phishing campaigns that use them are facing a bigger problem as Windows has no built-in mechanism to open a WIM file, and therefore when the users will try to open them will just be greeted with a message asking them to select a program to open the file.
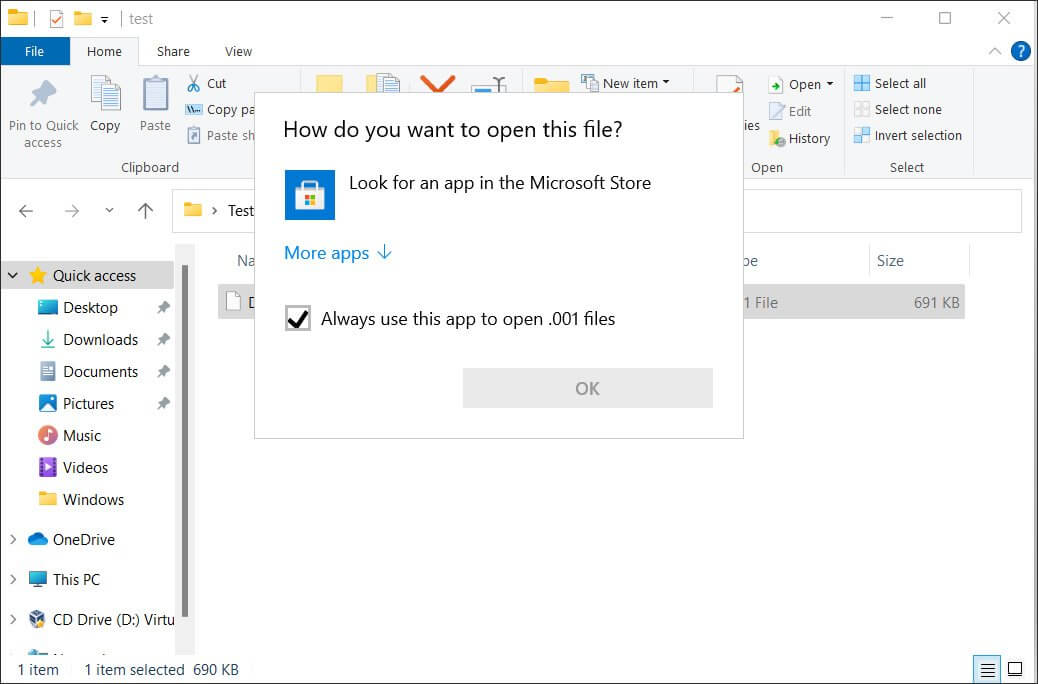
This means that in order for the WIM files to be opened a user would need to go out of their way and extract the file using a program like 7-zip and then double-click on the file within it.
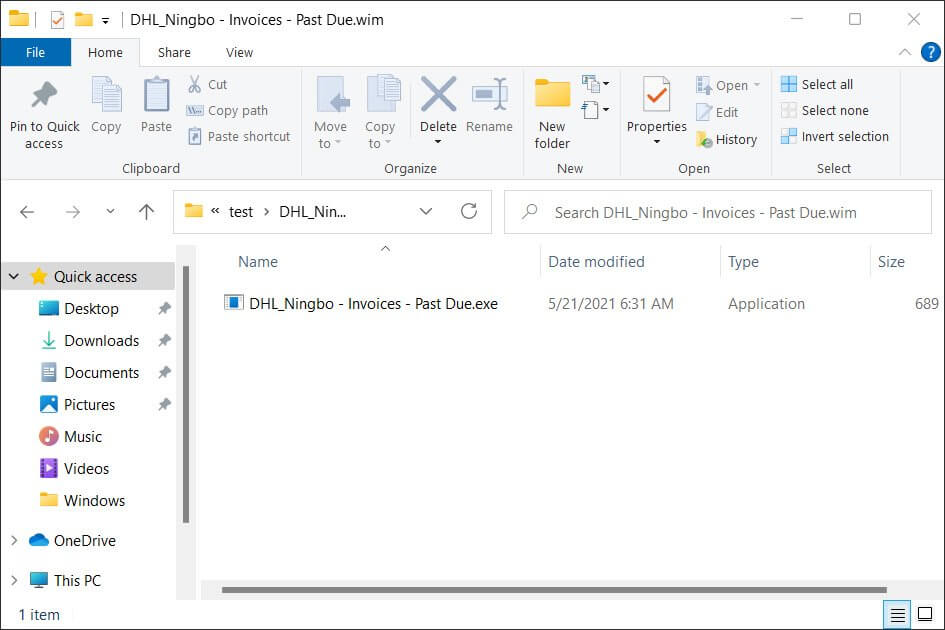
Not the Best Attack Strategy
This strategy can indeed bypass some security filters but is a double-edged sword for the threat actor, as the files will not be opened by most devices that do not have specialized programs.
Encapsulating malware in an unusual archive file format is one of the common ways to bypass gateways and scanners. However, this strategy also poses a hurdle – the target system must recognize the file type or at least have a tool which can unpack and process the file.
In contrast to the more popular .IMG and .ISO disk image files, WIM files are not supported by Windows built-in ability to mount disk image files. Moreover, the other popular archive utilities WinRAR and WinZip do not recognize the WIM disk image. WIM files can be processed with the widely used 7Zip.
We can assume that soon these attachments will be blocked by the secure email gateways, but until then users should remain cautious.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










