
- Larisa Mihai, Cyber Compliance Expert
In October 2024, European Union member states had a deadline to transpose the NIS2 Directive into national law.
Although not all countries have begun enforcing the rules, it will eventually become the norm across the bloc – and will likely affect firms outside the EU too.
One of the key ways that NIS2 will be enforced is via audits. If a company gets audited but fails to show how it meets the Directive’s cybersecurity and compliance standards, it will likely face steep fines.
Audits are very likely to happen if your company ever reports a security breach, but they may also happen randomly to companies that haven’t reported any issues.
In a recent webinar, Heimdal sat down with Larisa Mihai, a security and compliance expert at SALP Inc. Larisa provided plenty of insights and ideas about how to comply with NIS2 and DORA (a related regulation).
You can watch the full on-demand webinar here.
In this article, you’ll learn:
- Who will be conducting NIS2 audits
- What’s likely to happen during a NIS2 audit
- How to prepare for a NIS2 audit
Who will audit you for NIS2 compliance?
If you are reading this article, we’re going to assume your organization is subject to NIS2.
Unsure if the Directive applies to you? Check out our overview blog.
If your business is affected, it is reasonably likely that you will be audited for compliance at some point.
It is estimated that there are at least 100,000 companies across the EU that come under the scope of NIS2.
Depending on the size of your country, there could be anywhere between a few hundred to tens of thousands of firms that might be audited.
Some companies – particularly larger businesses deemed “essential” – can therefore expect to find themselves in the crosshairs for an investigation at some point. So, who will be auditing you?
Competent authorities will do most of the investigations
The main people responsible for NIS2 audits will be the “competent authorities“ in each country.
This will typically be a government body. Its main task will be to identify companies to audit and, if necessary, dish out penalties.
Your customers
The NIS2 Directive is quite heavily focused on supply chain security – particularly IT supply chains. If you provide IT services to businesses that come under the NIS2 Directive, they may require you, as a supplier, to give them evidence of your security posture.
Auditing firms
Various auditing firms will likely emerge to support companies or even competent authorities with conducting NIS2 audits.
What should you expect from a NIS2 audit?
In the coming years, many organizations are likely to face a NIS2 audit. What can you expect from the experience?
Audits will be (somewhat) random
Different countries will apply NIS2 in different ways and with varying levels of strictness.
But it is likely that competent authorities will carry out inspections of “essential” entities randomly – whether or not you’ve recently reported a breach. These audits may be regular or ad hoc.
If you are classified as an “important” entity, you will probably only be audited after a cyber security incident has occurred.
You’ll get two weeks to prepare
The competent authority will give you two weeks’ written notice before the inspection. You’ll need to spend this time preparing evidence in line with the auditor’s requests.
Keep reading:
NIS2 Compliance - How to Do It Sustainably by Continuous Compliance
Create a folder of documents and evidence
You’ll need to put together evidence of how you assess risks, monitor for threats, maintain cybersecurity standards and how you plan to respond to incidents.
On the day of the NIS2 audit
On the day of the inspection, you will need to prepare a short presentation of your business and the services/products you supply.
You’ll then need to demonstrate the measures you take to protect your data. The auditors will want to look around your security systems.
They may potentially interview ‘regular’ employees or senior staff to find out how aware they are of the organisation’s security practices and policies.
Get ready if you’re a supplier
If you are a supplier to ‘essential’ or ‘important’ entities under NIS2, there’s a high likelihood your customers will request evidence of your current security policies too (particularly if you provide any kind of IT services).
What evidence do you need to provide to show you’re NIS2 compliant?
Let’s imagine you’ve been contacted by your country’s competent authority, or a business customer.
They tell you that you’ll be subject to an audit in a couple of weeks – what will you need to show evidence of?
Here are the key things you’ll need to provide the auditors:
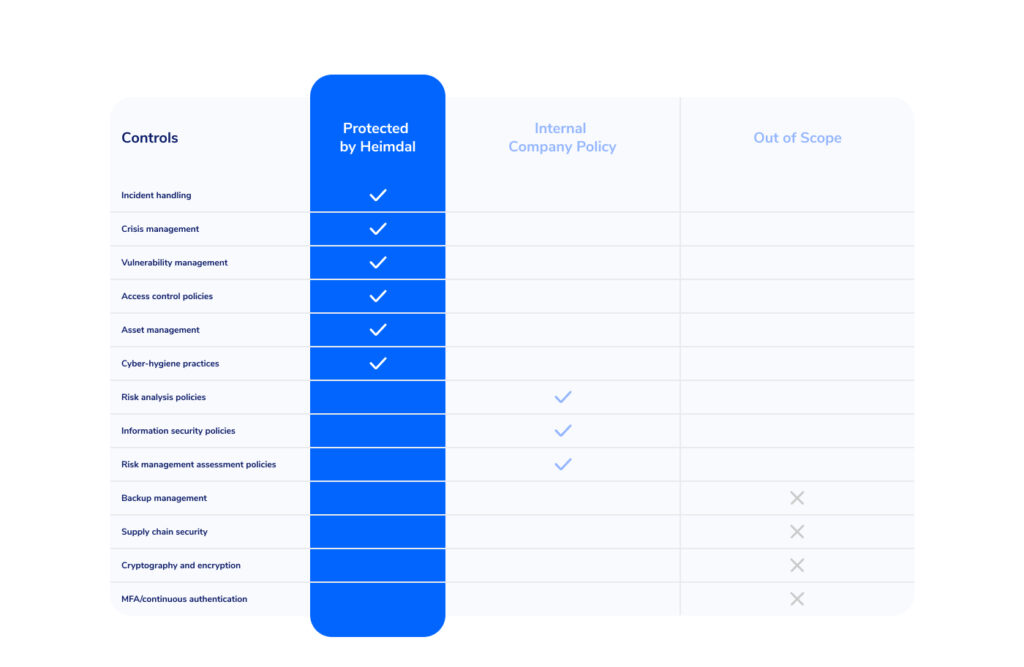
Incident handling process
Document your plan for incident response.
Crisis management plan
Spell out your processes for dealing with breaches, name responsible people and their duties.
Vulnerability management process
Show how you identify vulnerabilities, scan for patches and keep your environment up to date.
Access control policies
Provide evidence of your access control policies, how often passwords must be updated, what forms of identity authentication you use.
Learn How Heimdal Helps You Comply With
EU'S NIST2 DIRECTIVE
Asset management policies
Explain how you deploy patches and updates across operating systems and third party software.
Cyber-hygiene practices
Provide information about password strength rules, firewalls, antivirus, software updates etc.
Risk analysis policies
Document how you identify and assess risks, monitor for them and identify gaps.
Information security policies
This is all about documenting policies around access control, encryption, data backup, data archiving etc.
Risk management assessment policies
Spell out how you identify risks, what the possible harms may be, and show how you monitor them.
Backup management
Provide information about where you backup data, how, and for how long.
Discover our
TOP 5 NIS2 COMPLIANCE SOFTWARE LIST
Supply chain security
Show how you are monitoring your suppliers’ cybersecurity policies. Request reports and regular updates, especially from any IT suppliers.
Cryptography and encryption
Explain which encryption tools you are using.
MFA/continuous authentication
Provide information about your multi factor authentication methods and zero trust policy.
If you are already following good cyber security practices, complying with NIS2 is actually fairly straightforward. Ultimately, it’s just about compiling the evidence.
That being said, it’s a good idea to collect this information sooner rather than later. It means you won’t be in such a rush if you get randomly audited.
It can also help identify any weaknesses and blind spots you hadn’t thought about.
Automating NIS2 audit compliance

- Andrei Hinodache, Cybersecurity Expert
At Heimdal, we have developed a NIS2 Directive compliance framework which monitors your IT environment and produces a report about your security levels.
To be very clear, this report won’t make you compliant. Rather, it gives you a picture of your current security status.
Essentially, the solution scans your IT network, policies and settings and creates a clear picture of what you’re doing to comply with NIS2.
For all key elements that auditors will look for – from crisis plans to access control policies to vulnerability management – it will generate a score and evidence about your activities.
This means responding to an audit request will be far more efficient.
Our report means your NIS2 compliance activities can be continuous.
As Larisa explained in the webinar, this means that “whenever somebody wants something from us, we can just pull it out and send it to them”.
NIS2 compliance made easier
Complying with NIS2 isn’t going to be super simple for every organization.
The idea behind the Directive is to push European businesses to meet the highest standards of security.
There is no quick fix here – for some organizations it will require hard work and significant changes.
Getting a NIS2 Compliance Checklist – with free templates – that guides you through all the needed steps of the compliance process will likely make things easier for you.
That being said, when you do fully comply, you’ll also be much better prepared for potential attacks and are potentially less likely to become a victim of cybercrime.
And with Heimdal’s NIS2 Directive report, you’ll get access to super valuable guidance on what your current security posture is, and how compliant you are.
Should you receive a visit by an auditor – or a supply chain request from a customer – then you can quickly demonstrate what you’re doing to follow the rules.
This will keep away both hackers and NIS2 fines.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








