Contents:
A new ransomware strain emerged: Big Head uses fake Windows updates and Microsoft Word installers to spread.
Researchers analyzed three samples to establish the infection vector and how the malware executes. Although the variants may differ, they originate from the same threat actor, and this ransomware is still a work in progress, aiming to optimize attacks.
How Big Head Ransomware Works
The ransomware is a .NET binary that, once in, installs three AES-encrypted files: first to propagate the malware, the second for Telegram bot communication, and the third to encrypt files and to show the fake Windows update.
On execution, the ransomware also performs actions such as creating a registry autorun key, overwriting existing files if needed, setting system file attributes, and disabling the Task Manager.
Each victim is assigned a unique ID that’s either retrieved from the %appdata%\ID directory or it is generated using a random 40-character string.
To prevent system restoration, the malware deletes shadow copies before encryption. The targeted files get a “.poop” extension to their filenames.
Also, Big Head will terminate the following processes: “taskmgr”, “sqlagent”, “winword”, “sqlbrowser”, “sqlservr”, “sqlwriter”, “oracle”, “ocssd”, “dbsnmp”, “synctime”, “mydesktopqos”, “agntsvc.exeisqlplussvc”, “xfssvccon”, “mydesktopservice”, “ocautoupds”, “agntsvc.exeagntsvc”, “agntsvc.exeencsvc”, “firefoxconfig”, “tbirdconfig”, “ocomm”, “mysqld”, “sql”, “mysqld-nt”, “mysqld-opt”, “dbeng50”, “sqbcoreservice”.
It will skip from encryption Windows, Recycle Bin, Program Files, Temp, Program Data, Microsoft, and App Data directories so the system will not become unusable.
The ransomware verifies if it runs in a virtual box, as well as the system language and it doesn’t act if it is set on that of a country member of the Commonwealth of Independent States (former Soviet states).
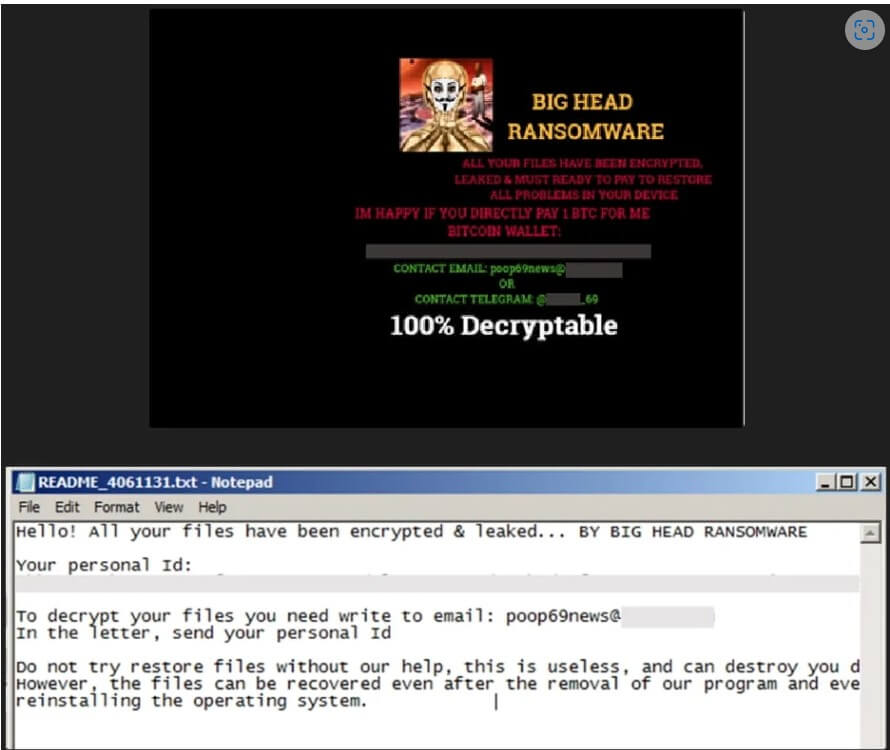
The ransomware shows a screen that pretends to be a genuine Windows update while encrypting data. A ransomware notice is dumped on numerous directories after the encryption procedure is finished, and the victim’s wallpaper is also modified to warn of the infection.
Other Variations of Big Head Ransomware
Researchers were able to compare multiple variants of the malware and noticed some key differences. The second variant shows ransomware futures and also stealer futures, so it exfiltrates important data from the victim’s system. The exfiltrate data can include: browsing history, list of directories, installed drivers, running processes, product key, active networks, and screenshots.
The third variant of the Big Head ransomware incorporates a file infector named “Neshta,” which can insert malicious code into executables. Researchers speculate that its function is to evade signature-based detection. Furthermore, this variant displays a different ransomware note and wallpaper. Yet, all three of them are tied to the same threat actor.
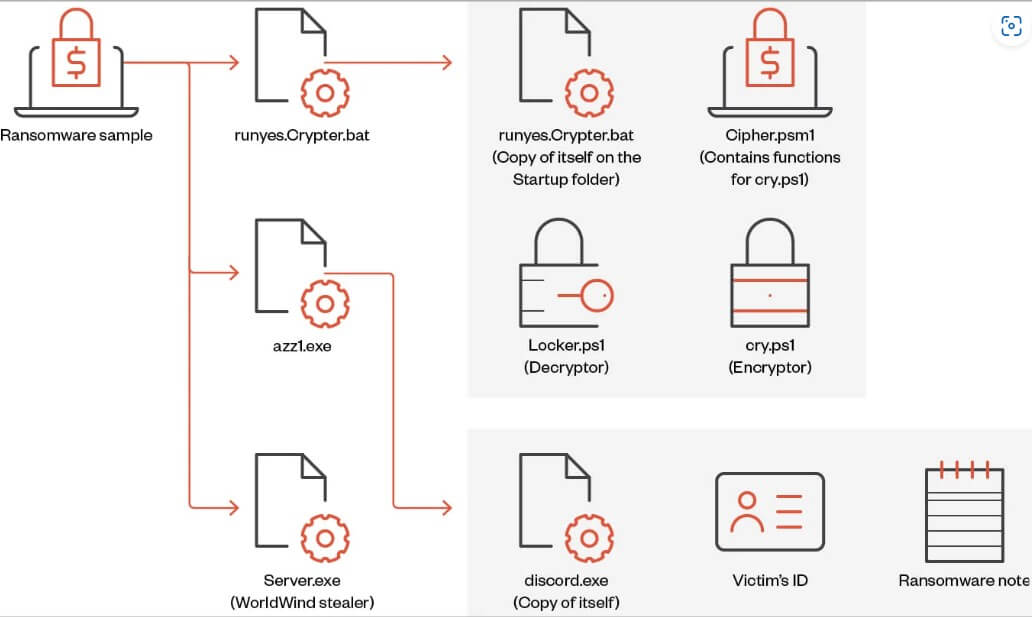
Big Head is not a particularly clever ransomware strain; its encryption algorithms are quite conventional, and its evasion strategies are simple to spot. Nevertheless, the numerous varieties in use imply that its developers always enhance and improve the malware, testing different strategies to determine what works best.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security