Contents:
Researchers attributed Cheerscrypt – a newly found ransomware strain that operates on Linux – to a Chinese cybercriminal group.
The group, that launches brief ransomware attacks, is known by the names Emperor Dragonfly or Bronze Starlight (Secureworks) and DEV-0401 (Microsoft).
Details About the Hacking Group
Sygnia report shows that “Emperor Dragonfly’ (A.K.A. DEV-0401 / BRONZE STARLIGHT) deployed open-source tools that were written by Chinese developers for Chinese users. This reinforces claims that the ‘Emperor Dragonfly’ ransomware operators are based in China.”
Cheerscrypt is adding to the list of ransomware families used by the group in this past year. They are known for deploying LockFile, Atom Silo, Rook, Night Sky, Pandora, and LockBit 2.0.
One theory is that the group conducts espionage missions.
“It is plausible that Bronze Starlight deploys ransomware as a smokescreen rather than for financial gain, with the underlying motivation of stealing intellectual property theft or conducting espionage”, says Secureworks.
Details About Cheerscrypt Ransomware
In May 2022, Cheerscrypt was spotted by Trend Micro who highlighted its capabilities like targeting VMware ESXi servers and then threatening victims to expose stolen data if they refuse to pay in a double extortion ransomware attack.
“The ransomware shares overlaps with the Linux version of the Babuk ransomware, which had its source code leaked in September 2021 and also forms the basis of Emperor Dragonfly’s Rook, Night Sky, and Pandora families”, according to The Hacker News.
What is remarkable is that a single actor seems to operate the entire attack, with no help from affiliates. From initial access to ransomware deployment, he handles all the stages.
Infection chains observed to date have made use of the critical Log4Shell vulnerability in Apache Log4j library to compromise VMware Horizon servers to drop a PowerShell payload capable of delivering an encrypted Cobalt Strike beacon.
In parallel with the beacon, three tools written in Go were deployed: a keylogger that uploads the recorded keystrokes to Alibaba Cloud, a customized version of iox, and a customized version of NPS tunneling software.
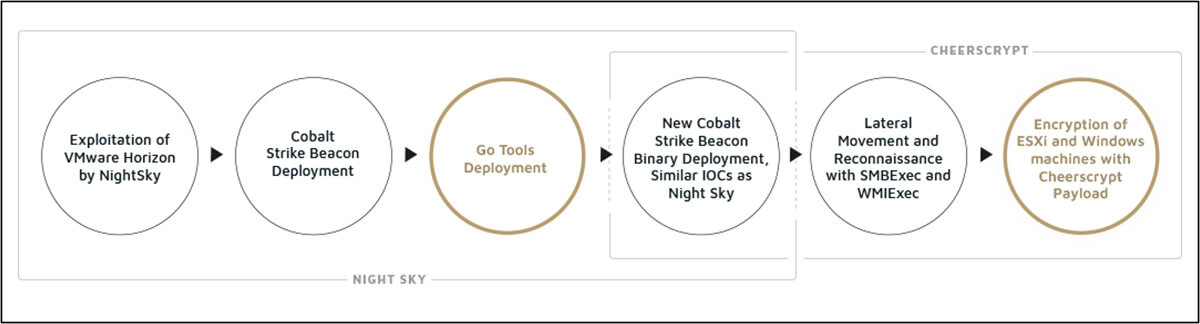
Cheerscrypt and Emperor Dragonfly share initial access vectors, lateral movement techniques, and the use of DLL side-loading to deploy the encrypted Cobalt Strike beacon.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









