Contents:
Network detection and response (NDR) is a cybersecurity tool that monitors a company’s network traffic to detect anomalies and alert or automatically respond to potential cyberthreats.
NDR is the newer and enhanced version of NTA (network traffic analysis) technology which was initially developed only to analyse the raw network data. As the technology evolved and threat response capabilities were added, the Gartner specialists decided to rename it into NDR sometime in 2020.
How network detection and response solutions work?
At a conceptual level, NDR solutions monitor and analyses network telemetry to create a baseline for the normal network data flow. NDR usually employs a combination of non-signature-based techniques like machine learning, behavioural analytics, and artificial intelligence to detect anomalies and unusual patterns compared to the baseline. Irregular traffic patterns might be related to malware, lateral movement, data exfiltration or communication with command-and-control servers.
Once a detection happens, it can send alerts to security teams or automatically take action by using its internal capabilities or through integrations with other various cybersecurity tools.
Advanced NDR platforms can also gather network logs from already-in-use network security tools, such as network firewalls, removing the need for dedicated network sensors. With minimal interaction, NDR systems provide comprehensive visibility and threat detection.
Why network detection and response is important?
As companies of all sizes expand their IT infrastructures to foster innovation, expand into new markets and regions, they are coming to the realization that the endpoint security solutions are unable to keep up with the challenges of today’s business environment.
Even while log analysis tools (SIEM) and endpoint detection and response (EDR) have already been widely adopted, and with good cause, a lot of companies still have a blind spot somewhere in their network.
NDR’s contribution to enhancing a company’s cybersecurity posture is significant, especially when combining them with other essential security solutions, to cover an ever-growing attack surface.
Benefits of using network detection and response solutions
- It enhances your overall cybersecurity.
- NDR is complementary to solutions that work at the endpoint level.
- It is efficient and easily scalable once your network grows.
- NDR can monitor all traffic flows, either incoming, outgoing, or within your network perimeter.
- It analyses the network data flows almost in real-time, enhancing threat hunting and incident response efforts.
- It has little network footprint when using analytics delivered by the cloud.
- Attackers are unable to manipulate network data, and they have no means of knowing whether they are being watched.
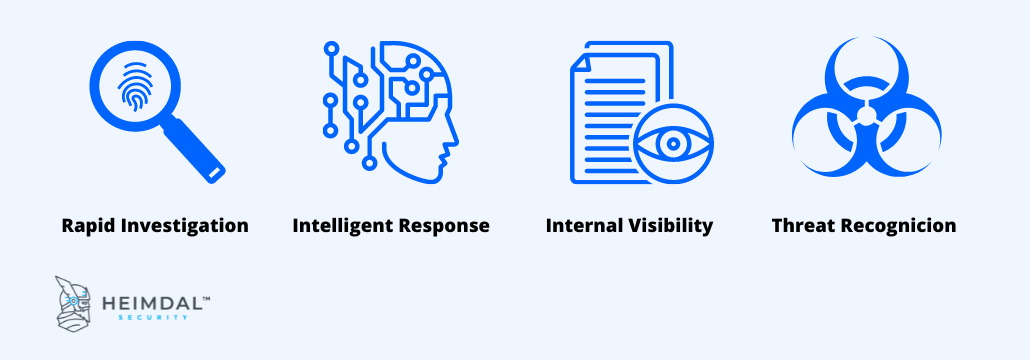
On-premises, cloud, and hybrid environments may all benefit from NDR systems’ support for the quick investigation, internal visibility, intelligent response, and increased threat detection. It is quite difficult for threat actors to conceal their behaviour while it is being detected at the network layer, which is why network-level attack detection is so effective.
Enhance Network Detection and Response with Heimdal®
By providing unique threat hunting and complete visibility across your entire network, Heimdal®’s Threat Prevention Network DNS-based solution can assist you in enhancing your company’s network perimeter security.
More than this, the entire Heimdal cybersecurity suite is unified under a single dashboard and working in unison to cover a wide range of attack vectors.
Heimdal® Network DNS Security
Feel free to leave your comments, recommendations, or questions in the comments section below, and don’t forget to follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security