Contents:
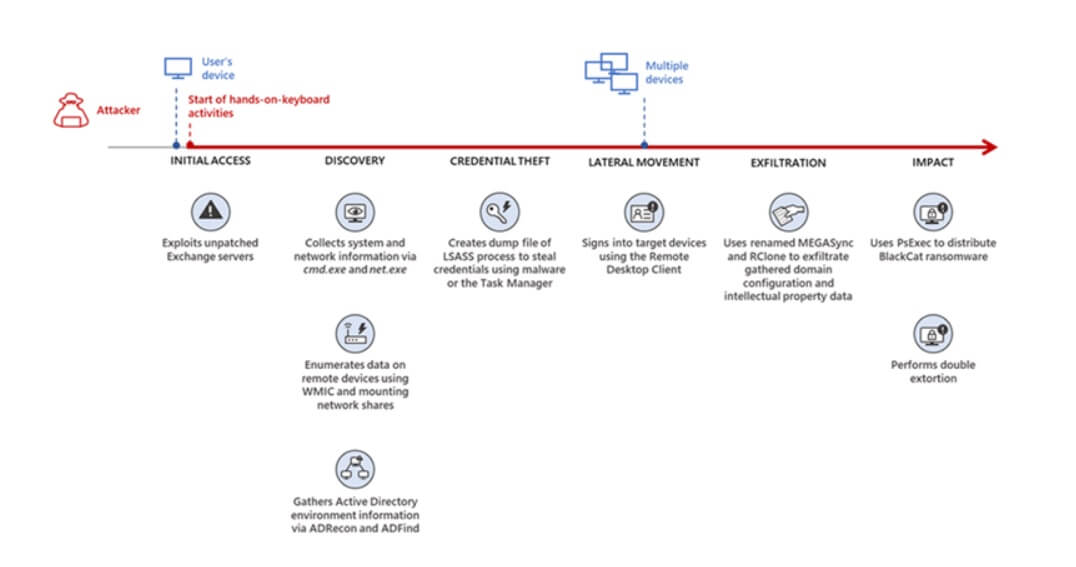
According to Microsoft, the BlackCat ransomware group is gaining access to targeted networks by exploiting unpatched Exchange server security flaws.
After gaining access, the threat actors quickly began collecting data about the infected systems, followed by credential theft and lateral movement activities, intellectual property gathering, and delivering the ransomware payload.
As stated by the Microsoft 365 Defender Threat Intelligence Team, the cybercriminals took two weeks after the initial compromise before deploying ransomware.
In another incident we observed, we found that a ransomware affiliate gained initial access to the environment via an internet-facing Remote Desktop server using compromised credentials to sign in.
The Anatomy of BlackCat Ransomware
BlackCat, also known as ALPHV and Noberus, is one of the first ransomware written in the Rust programming language. Its use of a modern language exemplifies a recent trend in which cybercriminals are transitioning to modern languages like Rust or Go for their payloads.
They do this not only to remain undetected by the traditional security software but also to challenge security specialists who might try to reverse engineer or compare the payloads to other threats that are similar.
BlackCat is capable of targeting and encrypting Windows, Linux, and VMWare instances. It has a wide range of capabilities, including self-propagation that can be configured by an affiliate for their use and to the environment encountered.
Regardless of the initial access vectors used, the Ransomware-as-a-Service (RaaS) scheme results in the exfiltration and encryption of target data, which is then held for ransom as part of what’s known as double extortion.
According to a report published by the FBI, since its debut in November 2021, BlackCat ransomware-as-a-service (RaaS) is said to have affected at least 60 organizations worldwide as of March 2022.
Moreover, Microsoft stated that BlackCat is being distributed by “two of the most prolific” affiliate cybercrime organizations, which have been linked to several ransomware families, including Hive, Conti, REvil, and LockBit 2.0.
This includes DEV-0237 (aka FIN12), a financially motivated hacker that was last noticed attacking the healthcare industry in October 2021, and DEV-0504, which has been operative since 2020 and has the habit of changing payloads when a RaaS program stops functioning.
DEV-0504 was responsible for deploying BlackCat ransomware in companies in the energy sector in January 2022. Around the same time, DEV-0504 also deployed BlackCat in attacks against companies in the fashion, tobacco, IT, and manufacturing industries, among others.
These results show how affiliate threat actors are progressively using RaaS to monetize their cyberattacks while utilizing significantly different pre-ransom steps to drop the ransomware payload within a target organization’s network, posing considerable challenges to traditional defense strategies.
Detecting threats like BlackCat, while good, is no longer enough as human-operated ransomware continues to grow, evolve, and adapt to the networks they’re deployed or the attackers they work for. These types of attacks continue to take advantage of an organization’s poor credential hygiene and legacy configurations or misconfigurations to succeed.
If Ransomware Concerns You…
Join us on Tuesday, June 21st, 1pm BST/2pm CEST for our next webinar, when Cyber-Security & Heimdal Product Expert Andrei Hinodache and Pre-Sales Engineering Manager Robertino Matausch will explain why ransomware is on the rise, and how should executives evaluate their company’s ability to prevent and recover from ransomware attacks.
What’s more, we will be showing you how to do this LIVE! Our experts will walk you through ransomware incident preparedness, technical testing through live simulations, detection, and suggestions for thwarting attackers by hardening systems and infrastructure.
Make sure you register here!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










