Contents:
According to security researchers who gathered data from Hive’s administrator panel, affiliates of the well-known ransomware group managed to breach in more than 4 months over 350 organizations. This means that the number of the average attacks raises to 3 companies attacked per day, this happening starting June when the gang’s operation was widely revealed.
About Hive Ransomware
It is known that Hive ransomware emerged in June with its first publicly known cyberattack happening on the 23rd of June. The gang attacked at that time the Canadian IT company Altus Group. In the beginning, it was not clear if the Hive ransomware gang worked as a ransomware as a service (RaaS) business model, according to an analysis by Group IBM researchers on this cybercrime group.
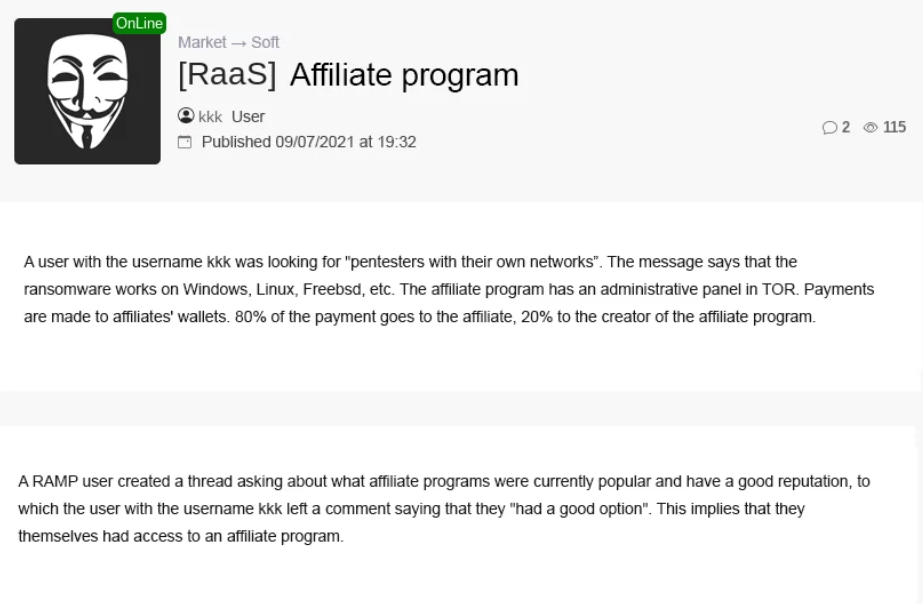
In early September, however, a user under the nickname “kkk” gave a reply on a thread from “reputable” ransomware programs saying that they are in search of partners to join them, partners who already own access to corporate networks. The message under discussion also gave details about how the ransom would be split, as 80% would have been for affiliates and the rest of 20% for developers.
The Group-IB researchers managed to capture a self-destructing note where technical data was provided in relation to the file-encrypting malware. This way they managed to identify that the RaaS operation the user aka “kkk” was advertising for was indeed related to Hive ransomware.
Hive Ransomware Attack Methods
According to researchers the initial compromise methods of the Hive ransomware group include phishing e-mails and compromised VPN credentials.
Hive affiliates resort to various initial compromise methods: vulnerable RDP servers, compromised VPN credentials, as well as phishing emails with malicious attachments. The data encryption is often carried out during non working hours or at the weekend. Taking into account that Hive targets organizations from various economic sectors from all around the world and their attacks are manually controlled by the affiliates, it’s crucial to closely monitor the changes in TTPs of these ransomware operators.
Deep Diving into Hive Ransomware Research
The Group-IB researchers dived deep into their investigation related to the Hive ransomware group and managed to get access to the ransomware admin panel. This way they began to gather data about its modus operandi.
It came out that ransomware deployment and negotiations with victims were made transparent and easy, as affiliates could produce a version of the malware in a period of 15 minutes. The negotiation then would be made via admins of Hive ransomware who made sure to use a chat window to send them the message. Besides, affiliates could have access to this chat window.
Some enterprises complained about the fact that the decryption tool given to them after paying the ransom lacked proper functionality, and made the virtual machines’ Master Boot Record non-bootable.
The researchers also underline the fact that the Hive admin panel shows affiliates how much money they obtained and also data about the paid companies and the disclosed ones.
The investigation showed all affiliates are granted access to the IDs of the company by means of the database of Hive ransomware.
Both the admin panel and the site where the data is leaked run through an Application Programming Interface (API). Due to an API error, the experts managed to gather data about the Hive attacks and they came to the conclusion that by October 16, 355 organizations were hit by this ransomware gang.
Based on the analysis of company data obtained through API, the number of victims grew by 72% in less than one month. On September 16, the total number of records related to victim companies was 181. Just one month later, on October 16, the number increased to 312. Notably, 43 companies listed as victims in September disappeared from API in October, most likely after paying the ransom.
How Can Heimdal™ Help?
Ransomware has been and continues to be an emergent threat on the cybercrime scene. Fight against it with a proper tool and choose a Ransomware Encryption Protection Product that keeps devices well-safeguarded against malicious encryption attempts and counters data exfiltration and data loss. Besides, it shows compatibility with any antivirus and it is also a 100% signature-free solution.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security