Contents:
Cybercriminals only want one thing these days, and that thing is substantial payouts. This is why most hackers focus on big game hunting, directing the vast majority of their efforts towards company networks rather than individual home users. MegaCortex ransomware is one digital threat with this particular MO, and a rather dangerous one at that. In the following lines, I will go into what MegaCortex ransomware is and what separates its two known versions from one another. A technical analysis will ensue afterward, followed by actionable advice on how to prevent an attack. So, without further ado, let’s get down to business.
What is MegaCortex Ransomware?
MegaCortex ransomware is a malware strain that initially appeared in January 2019 and was reportedly first announced by ransomware hunter Michael Gillespie on Twitter in May of the same year. Operators employ an assortment of manual and automated components to infect as many devices as possible. Corporations are MegaCortex ransomware’s primary target, not individual home users. File encryption, information theft, and disabling user access rights are among this ransomware’s main capabilities. Two variants have been identified and analyzed thus far.
MegaCortex Ransomware Version 1
A few thought-provoking characteristics set MegaCortex ransomware version 1 apart from other cyber-threats. For one, its payload contains a signed executable file. What is more, hackers offer their victims security consulting services as part of the attack. As per findings cited by a Bleeping Computer article in July 2019, MegaCortex ransomware targets networks that have already been infected with infamous Trojans such as Emotet and Qakbot. The first MegaCortex ransomware version was designed to protect itself, requiring a password in the command-line arguments to function properly. This made it difficult for cybersecurity researchers and vendors to analyze and reverse engineer the strain unless the credentials were captured during the infection’s deployment.
MegaCortex Ransomware Version 2
In another Bleeping Computer article from November 2019, cybersecurity author Lawrence Abrams stated that prior corruption by malware is what allows the ransomware operators to easily access a company’s systems. In the same post, the discovery of MegaCortex ransomware version 2 was publicized. Accenture Security analyzed a sample of MegaCortex ransomware version 2, highlighting the difference between it and version 1. While the password protection discussed in the previous section made the initial variant harder to pin down, it also prevented operators from succeeding in large-scale infections. Its genetic makeup made it mandatory for the ransomware to be deployed manually, or else risk that the password is leaked. This was corrected in version 2 with a redesign that restructured MegaCortex ransomware and allowed it to self-execute. Moreover, Lawrence Abrams has underlined that the updated variant changes the victims’ Windows passwords and steals copies of their data, threatening to make them public if the ransom is not paid.
MegaCortex Ransomware Analysis
There are a few technical telltale signs that can reveal whether or not your network has fallen victim to a MegaCortex infection. In the following subsections, I will present the ransom note for each variant, as well as further indicators of compromise (IoCs) to help you identify an attack promptly if the worst-case scenario occurs.
MegaCortex Ransomware Note
Upon encryption, MegaCortex ransomware creates a ransom note on the infected device titled !!!_READ_ME_!!!.txt. Michael Gillespie reproduced the version 1 text of the note in a Pastebin.com link included in his tweet revealing the then-new strain:
Your companies cyber defense systems have been weighed, measured and have been found wanting. The breach is a result of grave neglect of security protocols. All of your computers have been corrupted with MegaCortex malware that has encrypted your files. We ensure that the only way to retrieve your data swiftly and securely is with our software. Restoration of your data requires a private key which only we possess. Don’t waste your time and money purchasing third party software, without the private key they are useless. It is critical that you don’t restart or shutdown your computer. This may lead to irreversible damage to your data and you may not be able to turn your computer back on. To confirm that our software works email to us 2 files from random computers and C:\fracxidg.tsv file(‘s) and you will get them decrypted. C:\fracxidg.tsv contain encrypted session keys we need in order to be able to decrypt your files. The softwares price will include a guarantee that your company will never be inconvenienced by us. You will also receive a consultation on how to improve your companies cyber security. If you want to purchase our software to restore your data contact us at: shawhart1542925@mail.com anderssperry6654818@mail.com We can only show you the door. You’re the one who has to walk through it.
With version 2 of MegaCortex ransomware, the ransom note changes slightly to accommodate the updates brought to the strain. You can see the reimagined text in the image below of the document now titled !-!_README_!-!.rtf, courtesy of Bleeping Computer: 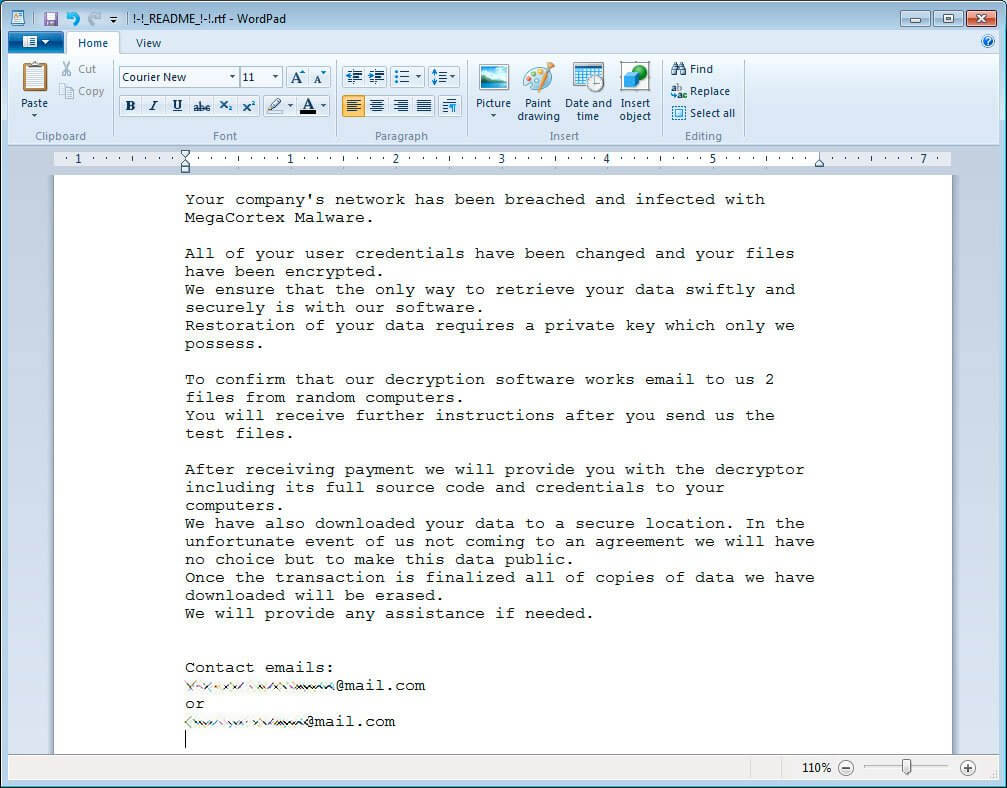
Image Source: Bleeping Computer
MegaCortex Ransomware IoCs
MegaCortex ransomware targets the following file extensions, avoiding files found in the %Windows% folder only:
.dll.exe.sys.tmp.lnk.config.manifest.old.mui.tib
Researchers identified the following encrypted file extensions:
.aes128ctrfor version 1.m3g4c0rtxfor version 2
Bleeping Computer lists the following cryptographic algorithm hashes for version 1:
77ee63e36a52b5810d3a31e619ec2b8f5794450b563e95e4b446d5d3db4453b2
As for version 2, Bleeping Computer has identified the following hashes in the sample they analyzed:
ca0d1e770ca8b36f6945a707be7ff1588c3df2fd47031aa471792a1480b8dd53 [Launcher]5ff14746232a1d17e44c7d095e2ec15ede4bd01f35ae72cc36c2596274327af9 [DLL]e362d6217aff55572dc79158fae0ac729f52c1fc5356af4612890b9bd84fbcde [DLL]
Further indicators of compromise for MegaCortex ransomware version 2 were listed in the aforementioned technical analysis report published by Accenture Security in 2019:
MD5:65939a4515a59da3697e4a454d6e8378SHA-1:470a8189915b01bc4012d7e0bdccba8e97a6a2d6SHA-256:86aeea7b383e35d4eec0219f031935648ddcf0b257196d3b60e44091ac4e99c2File Type:PE32 executable Intel 80386, for Microsoft WindowsFile Size:956,416 bytes
Please note that the hashes laid out by Bleeping Computer for version 2 differ from those recorded in the Accenture Security report. That is because the former provided three SHA-256 hashes for the elements dropped by the malware, while the latter logged the MD5, SHA-1, and SHA-250 hashes from a file encrypted by MegaCortex ransomware.
MegaCortex Ransomware Decryptor
A quick search in the No More Ransom Project’s decryption tools database will reveal that a MegaCortex ransomware Decryptor has not been made available at this moment. However, you can check back to their extensive list, as well as Heimdal Security’s own blog article on ransomware decryption tools, and see if one will have been released in the future. In the meantime, there are a few things you can do in the eventuality of a MegaCortex ransomware attack:
- Contain the infection by disconnecting the compromised device(s) from the Internet.
- Unplug external storage devices and log out of any linked cloud accounts.
- Put the compromised device(s) in Recovery Mode, if possible.
However, it is essential to keep in mind that these basic operations might not be feasible. MegaCortex ransomware is a rather aggressive strain that corrupts entire networks in an instant, changing user passwords and limiting access to elementary functions on the way. Therefore, prevention will always remain the best course of action.
Preventing a MegaCortex Ransomware Attack
#1 Implement a Strong Access Governance Policy
MegaCortex ransomware infiltrates and corrupts entire networks by cunningly manipulating user access rights. A strong access governance policy is thus indispensable to the prevention of such occurrences. Efficient identity management within your company network begins with credentials, which are often stolen, sold, and bought by cybercriminals to be used in ransomware operations. Ensuring that all accounts are protected by strong passwords is the first step you should take. A strong password should contain both uppercase and lowercase letters, as well as alphanumeric characters. It should be changed often and be unique to each account. Two-factor authentication can also aid greatly in this respect. Another essential element to a strong access governance policy is represented by the principle of least privilege or POLP for short. The principle of least privilege is a concept in information security that refers to limiting access rights for each user to the minimum necessary for their respective positions. Here’s what you should do:
- Audit privileges within your corporate network.
- Determine the level of access privileges that each account needs.
- Apply privilege bracketing to escalate rights for a limited time only.
- Prevent the accumulation of privileges over time on certain accounts.
- Implement a privileged access management (PAM) solution.
Heimdal® Privileged Access
Management
#2 Patch Your Software to Close Vulnerabilities
By exploiting vulnerabilities in your company’s network, MegaCortex ransomware gains unlawful access to your critical business infrastructure and confidential data. Unpatched software and applications are one of the main ways through which these security gaps appear. Unfortunately, constantly requesting permissions to install updates as soon as they are deployed by developers can become quite disruptive to your employees’ daily activity. For this reason, many choose to delay these operations as much as possible, which extends your network’s vulnerability in the face of cyberattacks. Heimdal™ Patch & Asset Management deploys Windows updates, as well as patches for third-party and custom software immediately after their release to your endpoints, regardless of their location. It allows users to install them at their own convenience, saving precious time and resources in the process. Updates can either be scheduled or pushed out automatically depending on schedules, all with zero interference.
#3 Provide Cybersecurity Education to Employees
Human assets can become network vulnerabilities as well. According to Verizon’s Data Breach Investigations Report, 30% of malicious emails are opened by the users they target, and 12% even click on the infected macro attachments. While MegaCortex ransomware might not employ social engineering techniques, the Trojans and malware it uses to enter corporate networks do. For this reason, your employees need to be well educated on the topic. The most common types of attacks that involve social engineering are:
- Phishing, a malspam campaign consisting of emails that mimic respected third parties.
- Spear phishing, a pointed phishing attack on a particular field or organization.
- Vishing, which stands for voice phishing and consists of fraudulent phone calls.
- CEO fraud, where attackers impersonate a figure of authority within a company.
- Macro attachments, or malicious attachments that are infected with the payload.
What is more, your employees must be trained in cybersecurity as a whole. There are many other types of attacks that can befall a company besides ransomware or phishing. Denial-of-service, man-in-the-middle, account takeovers or data breaches are just a few examples. Make sure your staff is up to date on these practices.
#4 Protect Your Network and Endpoints Alike
In an ever-evolving cyber-landscape, it comes as no surprise that ransomware is designed to evade traditional signature-based cybersecurity solutions. What is more, with the highly dynamic nature of today’s workplace, your digital defenses should focus on the company’s perimeter, as well as its endpoints regardless of their global positioning. Heimdal™ Threat Prevention consists of the Network Protection and Endpoint Protection modules, which are available as a bundle or as standalone solutions. My recommendation is to get both and have all your bases covered. By their powers combined, they create a holistic DNS filtering tool that detects and blocks ransomware, as well as data breaches, exploits, and other advanced threats.
#5 Back Up Crucial Data Online and Offline
MegaCortex ransomware makes it nearly impossible for you to recover your data through traditional methods. Operators limit your access to devices and disable Recovery Mode in an attempt to coerce you even further to pay the ransom and purchase their decryption keys. However, you shouldn’t give in to their demands. Not only do you have no guarantee whatsoever that you will get your files back, but you will also be financially supporting cybercriminal activity. My suggestion, in this case, is to always maintain both online and offline data backups. External storage devices and the cloud are your allies in data recovery. Of course, you must also keep in mind that these solutions are not impenetrable either. In case of a cyberattack, linked copies need to be disconnected immediately.
In Conclusion…
MegaCortex ransomware is a wicked strain that relies on surreptitious tactics and piggybacks on the damage done by other malware. However, a successful prevention strategy against it is a feasible goal, and it isn’t all too different from the approach you should take for other ransomware strains either. With proper access governance, software patching, cybersecurity education, data backups, and robust solutions, your corporate networks will be protected against infection.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











