Contents:
Decryptors for three popular ransomware families have been recently released by their supposed operator on the BleepingComputer forums. The ransomware operations under discussion are Maze ransomware, Egregor ransomware as well as Sekhmet ransomware.
Maze, Egregor and Sekhmet Master Decryption Keys Out Now
According to the BleepingComputer publication, a user dubbed “Topleak” was the one who leaked the decryption keys linked to the above-mentioned ransomware families on its forum, asserting to be the developer of the ransomware operations.
From the posted poster it comes out that the leak of the decryption keys was actually planned and the reason that triggered this action seems to not be associated with recent law enforcement operations.
Here is the forum post where “Topleak” announced the decryptors’ release.
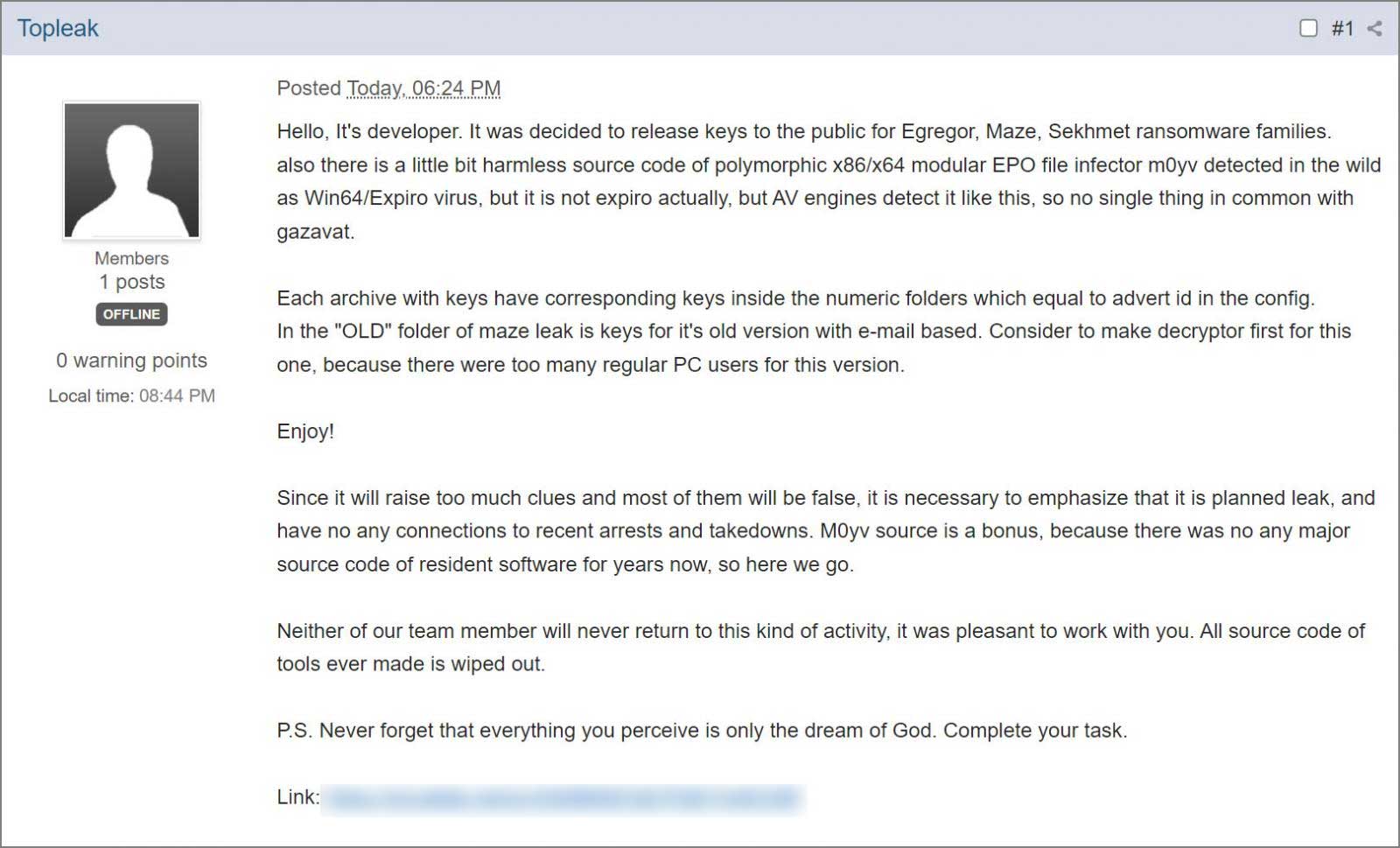
As the text reads, the developer said that the team gives up ransomware activities and they do not consider turning back ever. The user also mentioned that all of their ransomware source code had been destroyed.
At the end of the post, one can also find a download link. By accessing it, people can obtain a 7zip file that includes 3 archives, each corresponding to a ransomware family. Besides the three already mentioned, the fourth file includes the source code for an M0yv malware employed by the threat actors.
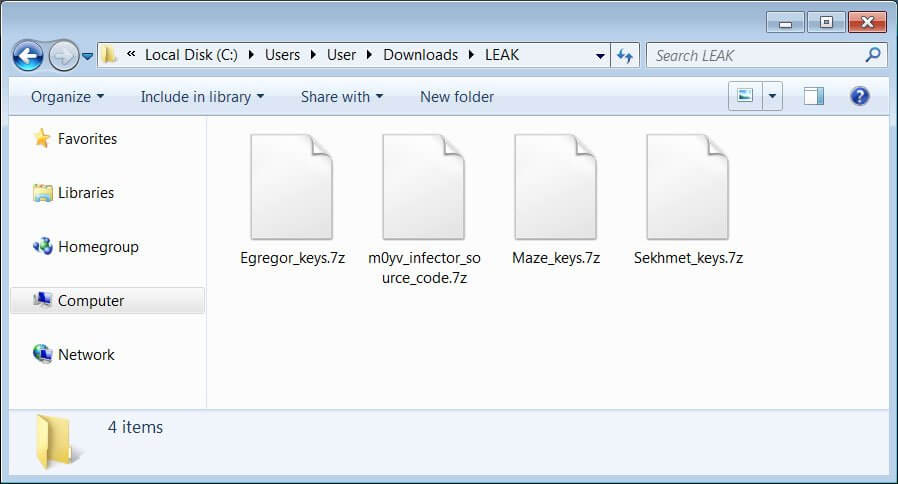
As BleepingComputer further mentions, every archive contains two types of keys: the public master encryption key and the private master decryption key linked with a certain affiliate. Thus, for Maze ransomware 30 master decryption keys were released and 9 for non-corporate users targeted by the original malware, for Egregor 19 master decryption keys were provided, and last, for Sekhmet 1 master decryption key was provided.
Fabian Wosar and Michael Gillespie from Emsisoft confirmed to the publication mentioned above the legitimacy of the provided decryption keys.
There is also a free Emisoft decryptor for Maze, Egregor, and Sekhmet available.
What Are Maze, Egregor, and Sekhmet Ransomware?
Maze ransomware represents a ransomware family that employs double extortion techniques: besides encrypting data, its opeators also publish the stolen information on a public website if the corresponding ransom is not paid, thus the particular nature of the ransomware strain lives in the fact that it can make your business both experience a ransomware attack and a data breach. It was discovered in 2019 and was initially distributed via spam e-mails and exploit kits.
Egregor ransomware is linked to Maze and Sekhmet, being active since September 2020 with initial access on the victims’ network obtained through stolen credentials, remote access, and also spear phishing techniques.
Sekhmet ransomware performs also file encryption and its operators request a ransom in exchange. It has extensions like .HrUSsw,.WNgh, and .NdWfEr.
What About the Archive File Containing the M0yv Malware Source Code?
As mentioned above, the archive released by threat actors contains also the M0yv malware source code leveraged by Maze in past cyberattacks.
Also, there is a little bit harmless source code of polymorphic x86/x64 modular EPO file infector m0yv detected in the wild as Win64/Expiro virus, but it is not expiro actually, but AV engines detect it like this, so no single thing in common with gazavat. (…) M0yv source is a bonus, because there was no any major source code of resident software for years now, so here we go.
How Can Heimdal™ Help?
Prevention is always the best approach when implementing a cybersecurity strategy for a business. That’s why a powerful suite of cybersecurity solutions is actually what you need. From Ransomware Encryption Protection, Email Security, Threat Prevention that keeps DNS threats away, to Privileged Access Management to better control and monitor privileged access, and more, in order to create a unified cybersecurity strategy which is actually what Heimdal promotes and what will make you well-safeguarded in the long run.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










