Contents:
Installers for the cloud-based instant messaging app Telegram have been compromised to distribute the Purple Fox malware to install additional malicious payloads on impacted systems.
What Is Purple Fox?
Purple Fox, a Windows-based backdoor, first appeared in 2018 as a fileless downloader trojan distributed through an exploit kit that compromised more than 30,000 machines.
Because of its rootkit features, this malware is able to evade being detected and remain invisible to most anti-virus solutions. According to cybersecurity experts, the backdoor’s worm-like propagation capability allows it to spread more rapidly.
Back to Our Malicious Telegram Installers – How Does the Attack Work?
As per Minerva Labs’ new analysis, the attack chain starts with a Telegram installer file and ends with a malicious downloader known as “TextInputh.exe.” Using an AutoIt script called “Telegram Desktop.exe,” the malicious downloader installs additional malware from the C2 server.
When TextInputh.exe is executed, it will create a new folder (“1640618495”) under “C:\Users\Public\Videos\” and connect to the C2 to download a 7z utility and a RAR archive (1.rar).
The archive contains the payload and the configuration files, while the 7z program unpacks everything onto the ProgramData folder.
According to the report recently issued by Minerva Labs, TextInputh.exe runs the following actions onto the infected systems:
- Copies 360.tct with “360.dll” name, rundll3222.exe and svchost.txt to the ProgramData folder
- Executes ojbk.exe with the “ojbk.exe -a” command line
- Deletes 1.rar and 7zz.exe and exits the process
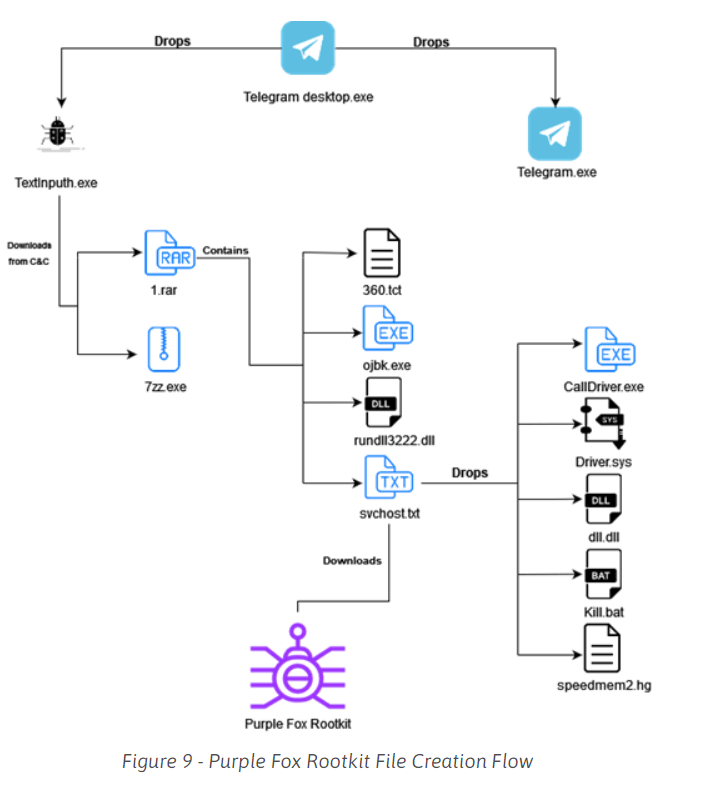
Following that, a registry key is generated for persistence, a DLL (rundll3222.dll) is used to disable UAC, the payload (scvhost.txt) is run, and the following five files are delivered onto the compromised machines:
- exe – this file is used to shut down and block initiation of 360 AV;
- sys – after this file is dropped, a new system driver service named “Driver” is created and started on the infected PC, and bmd.txt is created in the ProgramData folder;
- dll – executed after UAC bypass. The UAC bypass technique used by svchost.txt is a “UAC bypass using CMSTPLUA COM interface”. This technique is commonly used by the LockBit and BlackMatter ransomware authors. The dll.dll is executed with the “C:\ProgramData\dll.dll, luohua” command line;
- bat – a batch script that is executed after the file drop ends;
- hg – SQLite file.
All these files work together to shut down and stop the initiation of 360 AV processes from the kernel space, enabling the Purple Fox rootkit to run undetected on the affected systems.
The malware’s next action is to collect basic system data, verify if any security programs are installed, and then send everything to a hardcoded C2 address.
As explained by BleepingComputer, after the Purple Fox malware execution, the compromised device will be restarted for the new registry settings to start being applied, most importantly, the disabled User Account Control (UAC).
Disabling UAC bypass is important since it grants administrator rights to any application that runs on the affected computer, including viruses and malware. User Account Control (UAC) is a Windows security feature that helps to prevent unapproved changes to the operating system.
When disabled, it allows Purple Fox to execute malicious actions including:
- file search and exfiltration,
- process killing,
- data deletion,
- downloading and executing code.
According to BleepingComputer, it’s still unclear how the virus is being spread, but previous malware operations posing as genuine software have been delivered via YouTube videos, forum spam, and dubious software websites.
How Can Heimdal™ Help You?
Heimdal™ is always updated and keeps pace with the latest cybersecurity trends, a quality that perfectly illustrates its products too. Our awarded Threat Prevention Endpoint solution uses Machine Learning, cybercrime intelligence, and artificial intelligence capabilities to help you prevent future threats with 96 % accuracy on your endpoints, a very efficient threat hunting solution that makes malicious URLs, processes, and attacker’s origins no longer anonymous.
Alongside our Threat Prevention Endpoint solution, the Next-Gen Antivirus can help you supervise your mobile device fleet from anywhere in the world and from any Windows-compatible machine, as it allows you to remote-wipe or lock all stolen devices and accurately pinpoint the location of your misplaced smartphones. No more misplaced assets.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










