Contents:
PurpleFox botnet, the well-known Dirty Moe, goes on and develops more vulnerability exploits and payloads. The fresh news on this botnet shows how this time it establishes C2 communication via WebSockets.
PurpleFox Botnet: New Version Out There
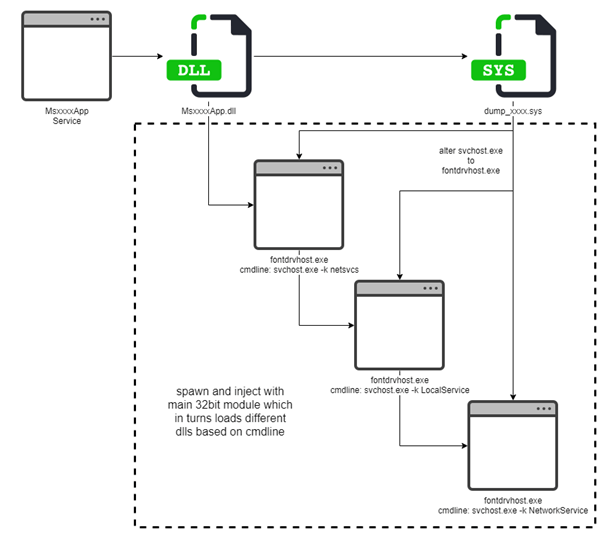
TrendMicro researchers tracked in their report the payload PurpleFox botnet seem to use in its freshest campaign. This payload is characterized by a long script with 3 components that allow for privilege escalation.
These are directed towards Windows systems (from 7 to 10), but they stop to those 64-bit based.
The following vulnerabilities are the ones exploited by the PurpleFox botnet, as the researchers stated:
CVE-2020-1054, CVE-2019-0808
These are associated with Windows 7/Windows Server 2008.
CVE-2019-1458
This is associated with Windows 8/Windows Server 2012.
CVE-2021-1732
This is associated with Windows 10/Windows Server 2019.
The host system is detected by the backdoor under discussion, then the correct exploit is picked out and after this, it will be loaded by the means of the PowerSploit module.
Using an admin-level process, an MSI package is triggered. This action does not need user interaction and what it does is to verify if there are old versions of PurpleFox and use new ones to replace them.
A DLL file, obfuscated via the file compressing utility named VMProtect is basically the backdoor deployed on the host system.
To hide its files, the backdoor will make use of a rootkit driver. And not only its files, but also processes and registry keys. This intends to lower the detection rates.
How the WebSocket Channel Works
As BleepingComputer mentions, after some days pass since the first intrusion was initialized, the dropping of a new .NET backdoor happens. This wants to establish C2 communications and does this using WebSockets. WebSocket is basically a component that not only takes care of the communication configuration set-up but also makes sure that cryptographic functions are initialized.
However, normally WebSockets do not make the object of malware communications, but PurpleFox seems to have found its workability suitable in this field too.
The C2 server will communicate with the compromised machine via messages, which are basically RSA encryption key negotiations. The TCP connection is persistent through “ keepalive” messages.
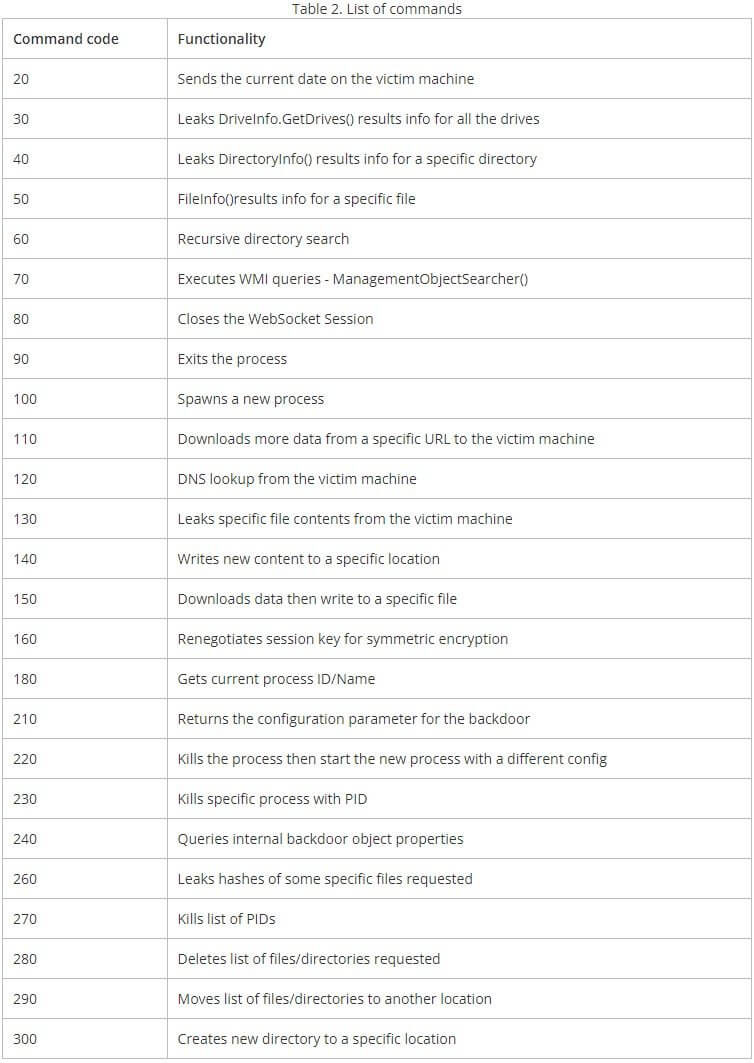
Here is also an overview of the WebSocket commands the researchers pulled out:
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










