Contents:
To outwit cybersecurity measures, malicious actors are continually enhancing their attack techniques. This sometimes entails developing brand-new malware; other times, it entails iteratively modifying malware that has already been proven effective in order to make use of fresh vulnerabilities or new attack strategies to avoid and infiltrate unprepared network infrastructures.
This type of evolution in ransomware has been witnessed before, most notably with Petya and NotPetya. One of the biggest threats to organizations is ransomware, which has left its imprint on the global corporate environment thanks to programs like DarkSide and several others.
In this article, we analyze the case of LockFile, a ransomware strain that has recently emerged from Lockbit 2.0 and has managed to get past security measures by employing innovative attack methods, more precisely intermittent encryption (a.k.a. partial encryption).
LockFile Origins
In June 2021, the LockBit ransomware gang announced a new major version for their tool claiming they significantly improved it for the encryption speed. In an attempt to support the claim they’ve made the threat actor apparently tested versions of multiple ransomware pieces and published their measurements for file encryption speed, thus launching LockBit 2.0. LockBit claimed it offered the fastest encryption and file-stealing (StealBit) tools in the world.
As we know, the majority of ransomware behaves similarly. The overall code of a file is encrypted using the generated encryption key, damaging all data in the process.
However, different mechanisms govern LockFile. It occasionally encrypts 16 bytes at once rather than the whole file. This suggests that a portion of the text-based data file will still be viewable. It will ruin the content and render it useless for files whose format is crucial (like a pdf).
Furthermore, unlike other ransomware, LockFile doesn’t really encrypt specific file types (such as .exe or .dll). The whole purpose of this encryption method is to keep the target’s OS operational, but with malicious data so that the affected company will eventually have no choice but to pay the ransom. What’s more, LockFile differs from previous ransomware in part because it does not target image files (jpeg, jpg, png, giff, bmp).
What Is Intermittent Encryption?
Intermittent encryption, or partial encryption, is a new technique that makes it easier for threat actors to avoid discovery and corrupt victims’ files more quickly. Lately, intermittent encryption has been used more frequently by ransomware operators, who also heavily promote the functionality to entice clients or partners.
Cyberattackers value partial encryption for two main reasons:
- Efficiency: Malicious actors need to encrypt files quickly because doing so reduces the likelihood that they will be discovered and halted in their tracks. Encryption can be a time-consuming procedure. However, within a very short period of time, intermittent encryption causes irreversible damage.
- Obfuscation: Data analysis may be used by ransomware detection solutions to identify malware activity. Quite an investigation might assess the volume of file Input/Output operations or the level of resemblance between a documented, ransomware-free variant of a file and a potentially altered, encrypted one. By having a substantially lower frequency of file IO operations than complete encryption and a considerably bigger resemblance between the encrypted and unencrypted copies of a file, partial encryption aids attackers in avoiding such investigations.
How Does Intermittent Encryption Work?
Imagine a file as a huge puzzle to better see the reasoning for encrypting only a portion of the file as opposed to the complete piece. The puzzle visual is so thoroughly altered during file encryption that it is impossible to distinguish it from the original. At that moment, it was impossible for anyone to be duped into believing this was a real puzzle.
What if, though, a sizable chunk of the riddle continued to persist? You might miss it if you don’t look closely. Therefore, it’s possible that only a portion of this data is encrypted on purpose in order to mask the danger. Once an entire file is encrypted, it is quite simple to spot changes made to the file. Yet, employing intermittent encryption is a whole new strategy.
The ransomware removes itself with the following command after it has encrypted all the files on the computer:
cmd /c ping 127.0.0.1 -n 5 && del “C:\Users\Mark\Desktop\LockFile.exe” && exit
In order to give the ransomware program five seconds to shut down before running the DEL command to remove the ransomware binary, the PING command sends five ICMP messages to the localhost (namely, itself).
This indicates that there won’t be any ransomware binary left over for antivirus software or incident responders to discover and remove following the ransomware operation.
Partial Encryption Operators
Although it was first used by LockFile, cybersecurity specialists have recently identified that intermittent encryption is now employed by several ransomware operators.
On a dark web forum, a member dubbed ‘lucrostm’ is now listing a ransomware strain called Qyick. Interested parties can buy Qyick for around 0.2 – 1.5 Bitcoins, depending on the level of intricacy the consumer wants. Interestingly, Qyick has intermittent encryption, which is described as the latest trend in the market, and its speed is unsurpassed when combined with the fact that it is programmed in go, according to the product description.
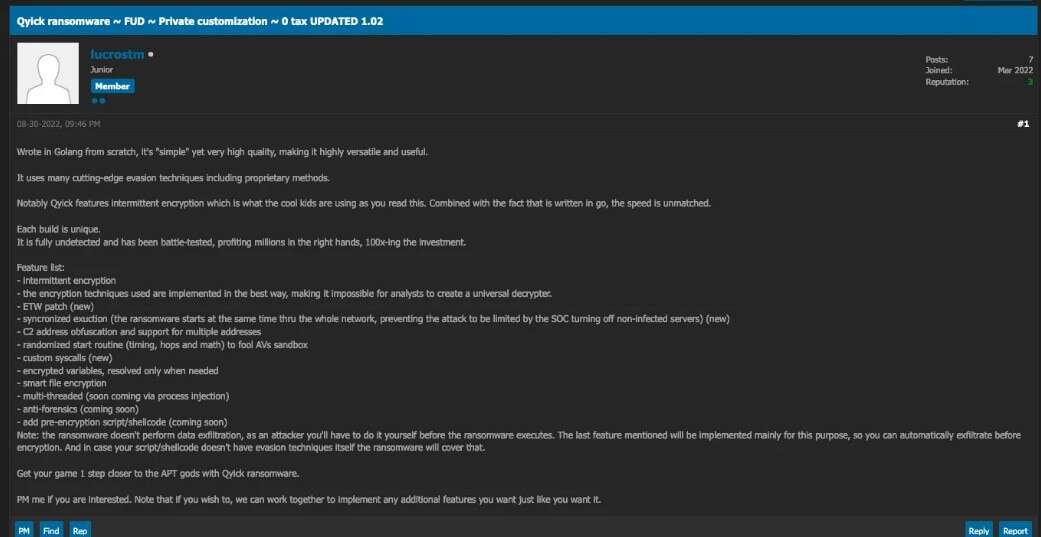
According to Sentinel Labs security researchers, BlackCat operators have access to a variety of encryption options, including intermittent encryption:
- “Full,” which encrypts every file on a system;
- “DotPattern [N,Y],” which encrypts N bytes of the affected files with a Y-byte delay;
- Auto,” which allows BlackCat to select a mode based on the size and extension of each file.
The same analysts discovered that in a controlled setting, the ‘Auto’ mode encrypted 50GB of files 1.95 minutes faster than the ‘Full’ mode, illustrating the faster encryption rates cybercriminals have attained through the use of this new technique.
Other ransomware gangs, including LockBit 2.0, DarkSide, and BlackMatter, have employed partial encryption to accelerate the process by merely encrypting the beginning of files.
Intermittent encryption is an extremely dangerous attack method. It keeps CPU usage low and hence process behavior, in line with “system normal behavior”, thus making it much harder to detect for conventional and behavior-based ransomware tools.
By just changing small portions of the file, the attack is very similar to previous disk-based corruption attacks, where the time-to-objective is greatly reduced and likelihood of detection is also much lower.
The evolution into this form of attack is very in line with our previous predictions of ransomware operators getting much more creative and we have not seen the last of this type of evolution. As previously eluded to, ransomware makers are market professionals, but you can also compare this to military tactics. This technique can easily be compared to a fire-and-maneuver tactic; in this particular case, the enemy is a moving target and very hard to hit.
We remain very confident that our approach with Ransomware Encryption Protection, which is agnostic of the enemy itself, but focuses on protecting the asset, will still prevail against these new tactics.– Morten Kjaersgaard, Heimdal CEO

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping Up…
Insufficient encryption is problematic from a security standpoint since it exposes data, yet ransomware doesn’t focus on data security. The only instrument used is encryption, and the data damage is regulated and recoverable. Therefore, ransomware only needs to encrypt a small fraction of a file’s contents to render it useless to the user, as is the case with LockBit 2.0, DarkSide, and BlackMatter when they only encrypt the file’s introduction.
Since there are no drawbacks to this new method, experts predict that more gangs will use it in the future. However, for data recovery to be at least difficult, the implementation must be done properly. As of right now, analysts believe BlackCat’s implementation to be the most advanced; but, because samples of the ransomware have not yet been examined, they are unable to assess the efficacy of Qyick’s strategy.
Extra vigilance is required on the part of the defender. Start by avoiding downloading files from sketchy web pages, opening email attachments from senders who are not on your mailing list, and clicking any links that may be included in these emails. Additionally, make sure that your antivirus is up to date, and consider deploying a ransomware encryption protection solution.
Heimdal is offering its customers an integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








