Contents:
Since the two prominent Russian-speaking cybercrime forums (XSS and Exploit) banned ransomware-related topics, most criminal operations have been forced to promote their service using alternative methods, therefore a new way of recruiting affiliates came to life.
Recently the LockBit gang announced a new major version for their tool claiming they significantly improved it for the encryption speed.
In an attempt to support the claim they’ve made the threat actor apparently tested versions of multiple ransomware pieces and published their measurements for file encryption speed, thus launching LockBit 2.0.
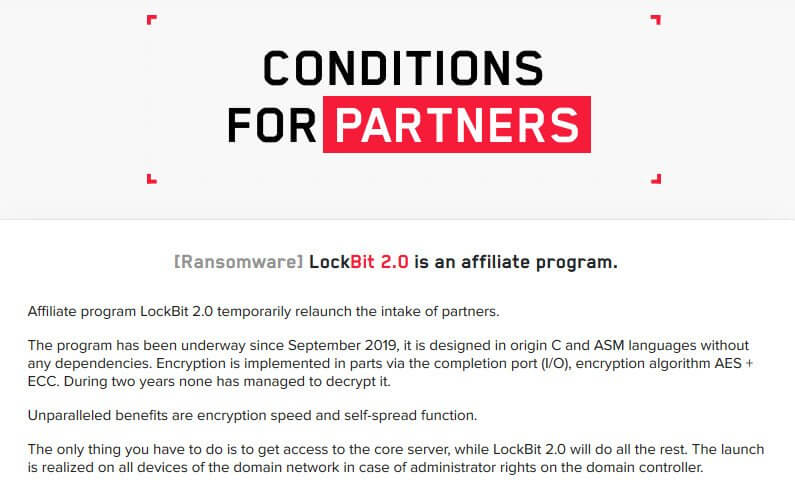
In this version of Lockbit the developers also disclosed that they will have a new affiliate recruitment session, highlighting that the encryption they use has not faltered since the operation started in September 2019.
The only thing you have to do is to get access to the core server, while LockBit 2.0 will do all the rest. The launch is realized on all devices of the domain network in case of administrator rights on the domain controller.
What Does Lockbit Promise?
LockBit is claiming to offer the fastest encryption and file-stealing (StealBit) tools “all over the world.”
In May LockBit tried to get ransomware talks back on a popular Russian-speaking forum by proposing a private section only for “authoritative users, in whom there is no doubt.
But users thought at the time that the ransomware topic “is now better known than ISIS terrorists,” meaning that the forum would get unwanted attention.
More Ransomware as a Service Operation Are Surfacing
Himalaya is a treat actor that appeared in the ransomware landscape this year and is now one of the gangs promoting ransomware-as-a-service (RaaS) operations on their website.
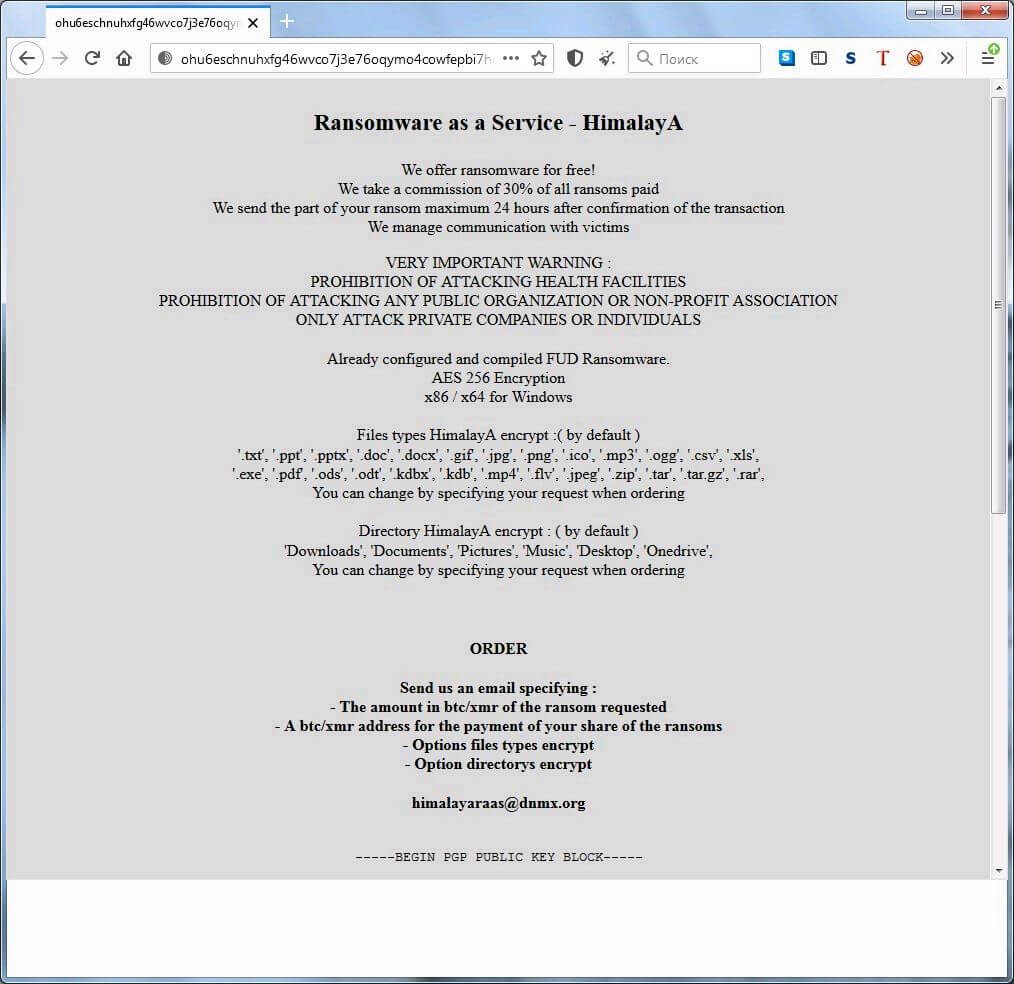
Himalaya is using its website to create awareness by advertising a 70% commission for affiliates and an “already configured and compiled FUD [Fully UnDetectable]” file-encrypting malware.
It’s interesting to note that Himalaya has a strict rule about the targets that can be attacked and does not allow the attack on healthcare, public, and non-profit organizations.
Even if we’re witnessing a rise in regards to the nefarious groups that are willing to advertise the RaaS operations they are conducting on their website, not all ransomware groups are willing to start using this target.
Let’s take the REvil gang as an example, as they are preferring to operate discretely whilst relying on a network of affiliates and connections to get new partners when they need them.
It shouldn’t be a surprise that most prominent ransomware groups will likely keep their head low considering the fact that the active hunt for ransomware actors has intensified after DarkSide encrypted Colonial Pipeline systems.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










