Contents:
In today’s data-driven world, it is essential for businesses to protect their systems from malicious attacks. Insider threat mitigation is a security measure that helps to identify and mitigate threats posed by malicious insiders, such as employees or contractors with access to sensitive information. Read on to find out what insider threat mitigation is, why it’s important and how you can implement it in your business.
What Is Insider Threat Mitigation?
First of all, let`s remember what exactly is an insider threat. According to CISA, “insider threat incidents are possible in any sector or organization”. An insider threat is typically a current or former employee, third-party contractor, or business partner. In their present or former role, the person has or had access to the organization’s network systems, data, or premises, and uses their access (sometimes unwittingly).
As the name suggests, insider threat mitigation is all about preventing damage from insiders. Insider risk mitigation is the process of prioritizing, evaluating, and implementing risk-reducing controls and countermeasures in order to prevent insider-related risks or reduce the damage they cause.
Insider threat detection is no easy task for security teams. The insider already has legitimate access to the organization’s information and assets and distinguishing between a user’s normal activity and potentially anomalous activity is a challenge. Insiders typically know where the sensitive data is found within the organization and often have elevated levels of access.

Types of Insider Threats
There are three primary types of insider threat: malicious, negligent, and accidental.
Malicious insiders are individuals who use their access to company information or systems for personal gain or to damage the organization. This type of insider threat is often difficult to detect because the individual may be skilled at hiding their activities.
Negligent insiders are employees who unintentionally expose company data through carelessness or lack of security awareness. For example, an employee may accidentally send an email containing sensitive information to the wrong person, or they may fail to properly secure their workstation when they leave it unattended.
Accidental insiders are individuals who inadvertently provide access to company systems or data to unauthorized people. For example, an employee may click on a phishing email link that gives attackers access to their workstation.
Insider threats can pose a serious risk to organizations, and it is important for businesses to have procedures in place to mitigate these risks. Some common mitigation strategies include employee training on security awareness, proper handling of sensitive information, and regular monitoring of system activity for unusual behavior, but more on that later.
Benefits of Implementing Insider Threat Mitigation
There are many benefits of implementing insider threat mitigation in your business. By doing so, you can protect your confidential information and intellectual property from theft or misuse. Additionally, you can safeguard your company’s reputation by preventing leaks of sensitive information.
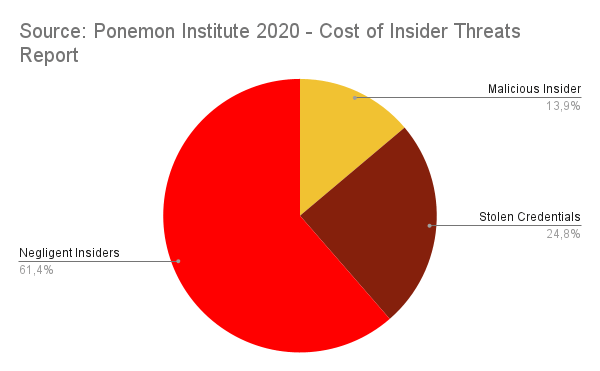
Moreover, insider threat mitigation can help you save money by deterring potential criminals from targeting your business. A study back in 2020 revealed that a data breach caused by an insider is significantly more costly for organizations than one caused by an external attacker. In the Ponemon Institute’s 2020 Cost of Insider Threats study, researchers observed that the global average cost of an insider threat was $11.45 million, while the average cost of a data breach over the same period was $3.86 million.
Finally, implementing these measures can give you peace of mind knowing that you have taken steps to protect your company. Find out below some of the best practices for mitigating insider threats.
Best Practices for Insider Threat Mitigation
Mitigating risks helps organizations detect and prevent insider threats that can lead to the realization of insider-related risks. The most common risks are loss of customers, reputational damage, as well as fines and penalties for non-compliance with cybersecurity laws, regulations, and standards.
There are different ways to go about mitigating insider threats.
- One would be to increase security awareness and train your employees on proper security protocols. This way, they’ll be less likely to accidentally make mistakes that could put your data at risk.
- You should also consider implementing technical controls to limit what insiders can do on your systems. For example, you could give them access to only the specific data and applications they need for their job, and nothing more.
Going further into determining the best practices when it comes to an effective insider threat mitigation strategy, we can summarize them as:
Employee Awareness and Training
Your employees need to be aware of the risks posed by insiders and how to identify suspicious activity. Additionally, they need to know what to do if they suspect that someone is attempting to commit an insider threat. Training can be delivered through a variety of methods, including online courses, in-person seminars, and printed materials. Establishing clear security policies and procedures that all employees must adhere to, is crucial to any organization.
Access Control
You need to thoroughly control who has access to your company’s information and resources. This includes both physical and electronic access. Only grant access to those who absolutely need it and keep track of who has accessed what. Monitor for unusual activity and investigate any potential red flags.
Data Protection
Make sure your company’s data is secure by encrypting it and storing it in a secure location. Implement strict controls on who can access this data and monitor for any unauthorized attempts to access it. Implementing technical controls such as data loss prevention (DLP) solutions to help prevent sensitive data from being leaked or stolen.
Furthermore, protect your most important assets. These assets can be physical, like facilities or people, or logical, like systems or technologies and, of course, customer data. You can achieve this by adopting a good defense in-depth strategy
Incident Response Plan
In the event that an insider threat does occur, you need to have a plan in place for how to respond. This plan should include steps for containment, investigation, and recovery. Responding quickly and appropriately to any incidents can mean revoking access privileges, suspending or terminating employment, and/or contacting law enforcement if necessary.
Several notable factors that guarantee a successful insider threat mitigation program of all organizations, regardless of size and maturity level, are:
Know Your People
An organization must know and engage its people; this awareness enables an organization to achieve an effective level of personnel assurance.
Identify the Organization’s Assets and Prioritize Risks
Determine where the organization’s assets reside and who can access them. This knowledge allows a broader classification of each asset’s vulnerability and enables the development of risk-based mitigation strategies.
Establish the Approach of Detect – Identify – Assess – Manage
By gathering and investigating incident and threat information, assess and categorize those risks; then implement management strategies to mitigate the threats.
How Can Heimdal® Help?
Heimdal`s Privileged Access Management enables you to quickly and easily elevate user rights or file executions, as well as revoke escalations and support zero-trust executions. Privileged Access Management has a simple and effective user interface that gives you complete control over a user’s elevated session. IT admins can use it to approve or deny requests from the Dashboard or from their mobile device, maintain track of sessions, restrict system file elevation, live-cancel user admin access, and create escalation periods.
Additionally, the Application Control module was carefully designed to limit which processes (or apps) can be run on client workstations, as well as how they are run. Using data such as Software Name, Paths, Publisher, MD5, Signature, or Wildcard Path, IT admins can construct a series of rules that explain what processes are allowed or denied on endpoints in an environment.
Heimdal’s Zero Trust component saves a significant amount of time for system administrators and, most importantly, it ensures limited access, increased compliance, simplification of addressing risks, helping customers to always be one step ahead of any cybercriminal – or insider threat.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Conclusion
Insider threats can be a major concern for any business, and it is important to have a plan in place to protect your organization from these threats. Regardless of how well-protected you think you are; a malicious insider might be hiding in the midst of your enterprise.
Insider threat mitigation strategies are essential in ensuring that the safety of your data and processes remains intact, while also providing employees with the tools they need to stay safe. With proper implementation of insider threat mitigation measures, organizations can successfully prevent malicious activities from occurring within their very own networks.
To protect your business from unsavory individuals, you should focus on two main aspects: technical controls and the human factor. With the right cybersecurity tools and procedures, as well as a strong company culture based around honesty, you will be able to successfully prevent this from happening to you.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







