Contents:
It has been discovered that a hacking group dubbed ‘ModifiedElephant’, described as an APT (advanced persistent threat) actor has been engaging in its malicious activities in secret for a decade, avoiding detection and correlation between attacks due to the employed methods.
Bringing ‘ModifiedElephant’ Out of the Shadows
Researchers from SentinelLabs have recently published a report where they went into details over the methods used by ‘ModifiedElephant’ APT.
The threat actors normally leverage handy trojans by means of spear-phishing emails including compromised attachments pushing RATs (remote access trojans) such as NetWire and DarkComet as well as keyloggers.
Various times, the attached files leveraged exploits such as CVE-2012-0158, CVE-2013-3906, CVE-2014-1761, and CVE-2015-1641 for malware execution purposes.
Reportedly, the campaigns’ lures have been identified to be politically linked and frequently customized depending on the target.
The legitimacy aspect of emails has been also approached in different manners.
This includes fake body content with a forwarding history containing long lists of recipients, original email recipient lists with many seemingly fake accounts, or simply resending their malware multiple times using new emails or lure documents.
Researchers also shared in their report a sample email linked to this threat actor:
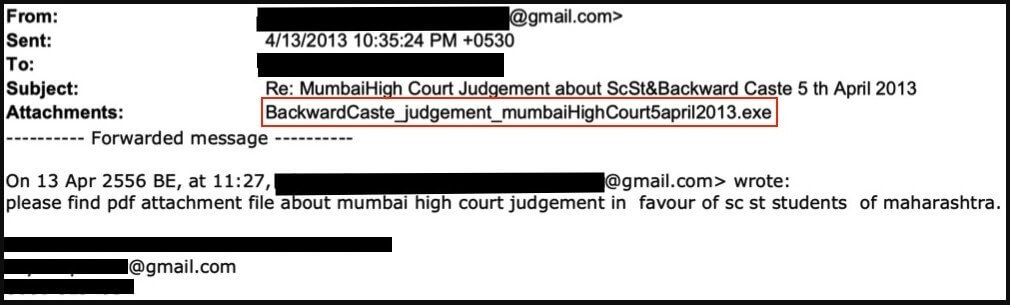
What’s interesting to mention is that the experts did not notice the APT group leveraging any custom backdoor which triggers the conclusion that they don’t show a sophisticated nature.
The malicious actor has been keeping its Visual Basic keylogger the same since 2012, being also available free of charge on hacking forums. However, the experts under discussion are of the opinion that this tool doesn’t function on modern OS versions anymore.
Timeline of ModifiedElephant Campaigns
The main methods of this actor were based on spear-phishing attacks. However, as the years have passed, its methods have evolved. Researchers have also shared in their report a timeline linked to the activity on this actor to emphasize the improvement in attack methods.
Thus, in 2013, ModifiedElephant leveraged email attachments containing false double extensions (file.pdf.exe) for malware dropping purposes.
Then, in 2015 the APT group used password-protected RAR archives. In these attachments, there were included legitimate lure files overlaying malware execution signs.
In 2019 the threat actor group hosted sites that dropped malware and also engaged in abusing cloud hosting services. Then the shift from false documents to malicious URLs happened.
Eventually, in the year 2020, ModifiedElephant made use of RAR files 300 MB in size for bypassing detection purposes.
What’s more, their targets, according to the same report, included free speech defenders, lawyers, academics, and activists of human rights from India.
How Can Heimdal™ Help?
Email Security is a must nowadays to keep your business-critical assets well protected because prevention is always better than mitigation. You can check out our Heimdal Suite to take a look at two stunning products: Email Security and Email Fraud Prevention. The first combines Office 365 support with proprietary e-mail threat prevention to safeguard against email-delivered malware and malicious URLs, the second works rather on preventing BEC (Business Email Compromise) and CEO fraud through its 125 analysis vectors. Curious? Contact us at sales.inquiries@heimdalsecurity.com!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








