Contents:
Microsoft Security Threat Intelligence research team warn about a threat actor identified as DEV-0569, which has been observed using Google Ads to distribute various payloads, including the recently discovered Royal ransomware.
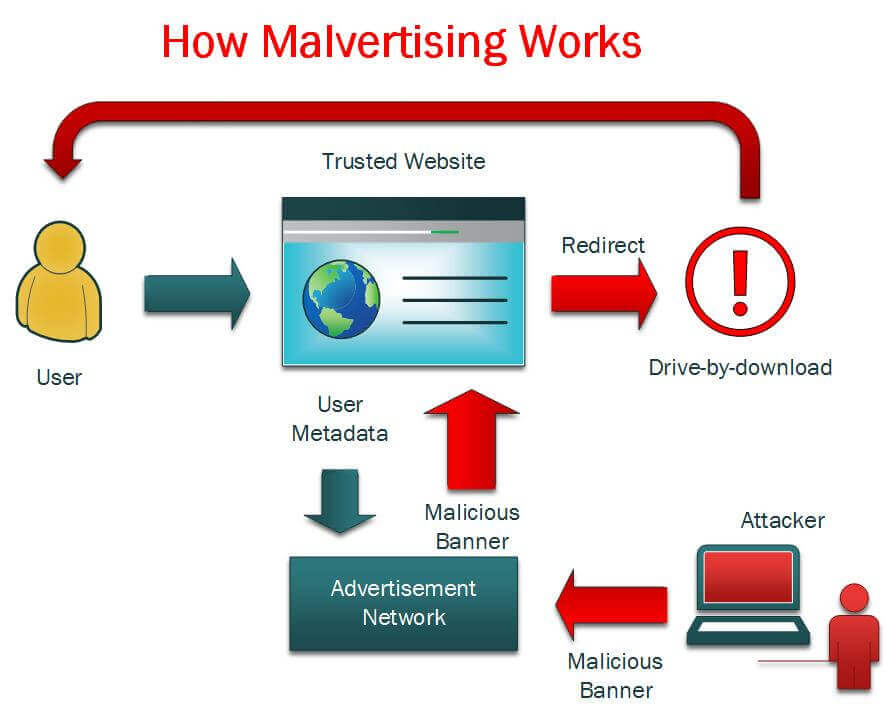
The DEV-0569 group allegedly carries out malvertising campaigns to spread links to a signed malware downloader posing as software installers or fake updates embedded in spam messages, fake forum pages, and blog comments.
Upon Further Analysis
In the report published by Microsoft, the cybersecurity researchers state that, in the recent months, they observed some adjustments in the group’s delivery methods, such as:
- Use of contact forms on targeted organizations’ websites to deliver phishing links
- Hosting fake installer files on legitimate-looking software download sites and legitimate repositories to make malicious downloads look authentic to targets, and
- Expansion of their malvertising technique by using Google Ads in one of their campaigns, effectively blending in with usual ads traffic
These methods would potentially allow the group to reach more targets and ultimately deploy various post-compromise payloads. DEV-0569 relies heavily on defense evasion techniques and employs the open-source tool Nsudo to disable antivirus solutions, as noticed in recent campaigns.
The malicious files, which are malware downloaders known as BATLOADER, pose as installers or updates for legitimate applications like Microsoft Teams or Zoom. When launched, BATLOADER uses MSI Custom Actions to launch malicious PowerShell activity or run batch scripts to aid in disabling security solutions and lead to the delivery of various encrypted malware payloads that is decrypted and launched with PowerShell commands.
The report further explains that BATLOADER, which shares similar characteristics with another malware known as ZLoader, has been spread over the course of a few months via malicious links in phishing emails, posing as legitimate installers for multiple popular applications, including TeamViewer, Adobe Flash Player, Zoom, and AnyDesk.
The malicious downloader was hosted on domains created precisely to appear as legitimate software download sites (for example anydeskos[.]com) and even on legitimate repositories like GitHub and OneDrive.
Furthermore, the attackers used file formats like Virtual Hard Disk (VHD) that also contained malicious scripts used to download DEV-0569’s payloads.
DEV-0569 has used varied infection chains using PowerShell and batch scripts that ultimately led to the download of malware payloads like information stealers or a legitimate remote management tool used for persistence on the network,” continues the report. “The management tool can also be an access point for the staging and spread of ransomware.
It wasn`t until late October that Microsoft observed a malvertising campaign leveraging Google Ads that point to the legitimate traffic distribution system (TDS) Keitaro. The TDS was used to redirect the user to the site hosting the BATLOADER. The DEV-0569 group used Keitaro to deliver the payloads to specified IP ranges and targets while avoiding IP ranges known to be associated with sandboxing solutions.
Taking all this into account lead experts to believe the group could potentially serve as an initial access agent for other ransomware operations, aligning itself with other malware such as Emotet, IcedID, Qakbot.
According to Microsoft, this issue has been reported further to Google for further analysis.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







