Contents:
As you might know, Microsoft Defender Antivirus is the anti-malware solution that usually comes pre-installed on systems that are running Windows 10.
The attackers have modified the malware distribution mechanism from spam or phishing emails to TeamViewer Google adverts, which link users to fraudulent download sites through Google AdWords.
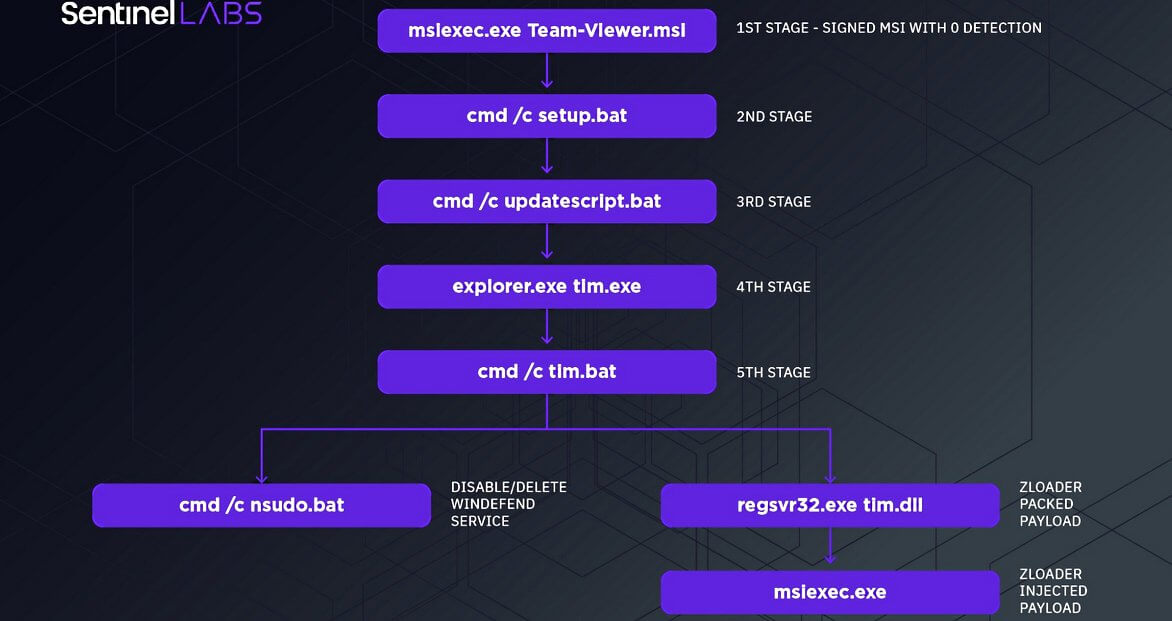
Victims are then misled into downloading Zloader malware payloads on their systems by installing signed and malicious MSI installers.
The attack chain analyzed in this research shows how the complexity of the attack has grown in order to reach a higher level of stealthiness. The first stage dropper has been changed from the classic malicious document to a stealthy, signed MSI payload. It uses backdoored binaries and a series of LOLBAS to impair defenses and proxy the execution of their payloads.
This is the first time we have observed this attack chain in a ZLoader campaign. At the time of writing, we have no evidence that the delivery chain has been implemented by a specific affiliate or if it was provided by the main operator. SentinelLabs continues to monitor this threat in order to track further activity.
Australian and German Banking Customers Under Attack
Zloader is a banking trojan. It was first discovered in August 2015 when it was used to attack clients of several British financial institutions.
This malware, like Zeus Panda and Floki Bot, is almost entirely based on the source code of the Zeus v2 Trojan, which was released online more than a decade ago.
According to the news publication BleepingComputer, the banking Trojan targeted institutions all across the world, from Australia to Brazil and North America, in the pursuit of collecting financial information using web injections. The Trojan used social engineering techniques in order to get infected customers to hand over authentication codes and credentials.
It has also been used to deliver ransomware payloads like Ryuk and Egregor in recent years. Zloader also comes equipped with backdoor and remote access features, as these capabilities may be used as a malware loader to deliver additional payloads to compromised computers.
This current effort seems to be aimed at clients of German and Australian banking institutions.
This is the first time we have observed this attack chain in a ZLoader campaign.
At the time of writing, we have no evidence that the delivery chain has been implemented by a specific affiliate or if it was provided by the main operator.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










