Contents:
A new SEO poisoning campaign is currently taking place with the goal of dropping the Batloader and Atera Agent malware into the targeted systems. It seems that it’s directed towards professionals who are on the lookout for downloading productivity tools like TeamViewer, Zoom, or Visual Studio.
What Is SEO Poisoning?
SEO poisoning is a technique used in cyberattacks by hackers to set up malicious websites filled with specific keywords that normally users look up in search engines. Then they employ different SEO (Search Engine Optimization) methods to make these appear notably in search results.
How Does This SEO Poisoning Campaign Work?
According to a report by researchers at Mandiant, in this malicious SEO campaign, threat actors compromise legitimate websites with the purpose of planting compromised files or URLs. This way, users are redirected to websites that accommodate malware posing as well-known applications.
After the software installers download and execution is complete, the malware will infect users.
Using SEO techniques to apply them to legitimate websites and targeting keywords related to famous apps like Microsoft Visual Studio 2015, Zoom, TeamViewer, and many more is a method employed by hackers in this massive campaign.
A user clicks on the link emerging in the search engine and what happens next is that they will be redirected to the malicious websites. This website includes a Traffic Direction System (TDS).
It’s interesting to mention that TDS has been used in past malicious campaigns, however, in those cases, users would have been redirected by these scripts if only their visit resulted from a search engine result. If this would have happened, they would still see the legitimate blog post.
Why do hackers use this technique? Well, it helps them hinder the security professionals’ analysis as only those visitors who came from search engines would see the malicious behavior.
When the redirect happens, users will be displayed with a false forum discussion. This conversation normally seems to serve the purpose of a user finding how to obtain a certain application. The counterfeit user that responds would share a download link.
When the user clicks on the download link, the website will produce packaged malware installed by means of the application that had been searched for. In the malware packaged legitimated websites can be found and the user will thus not figure out that the infection happened.
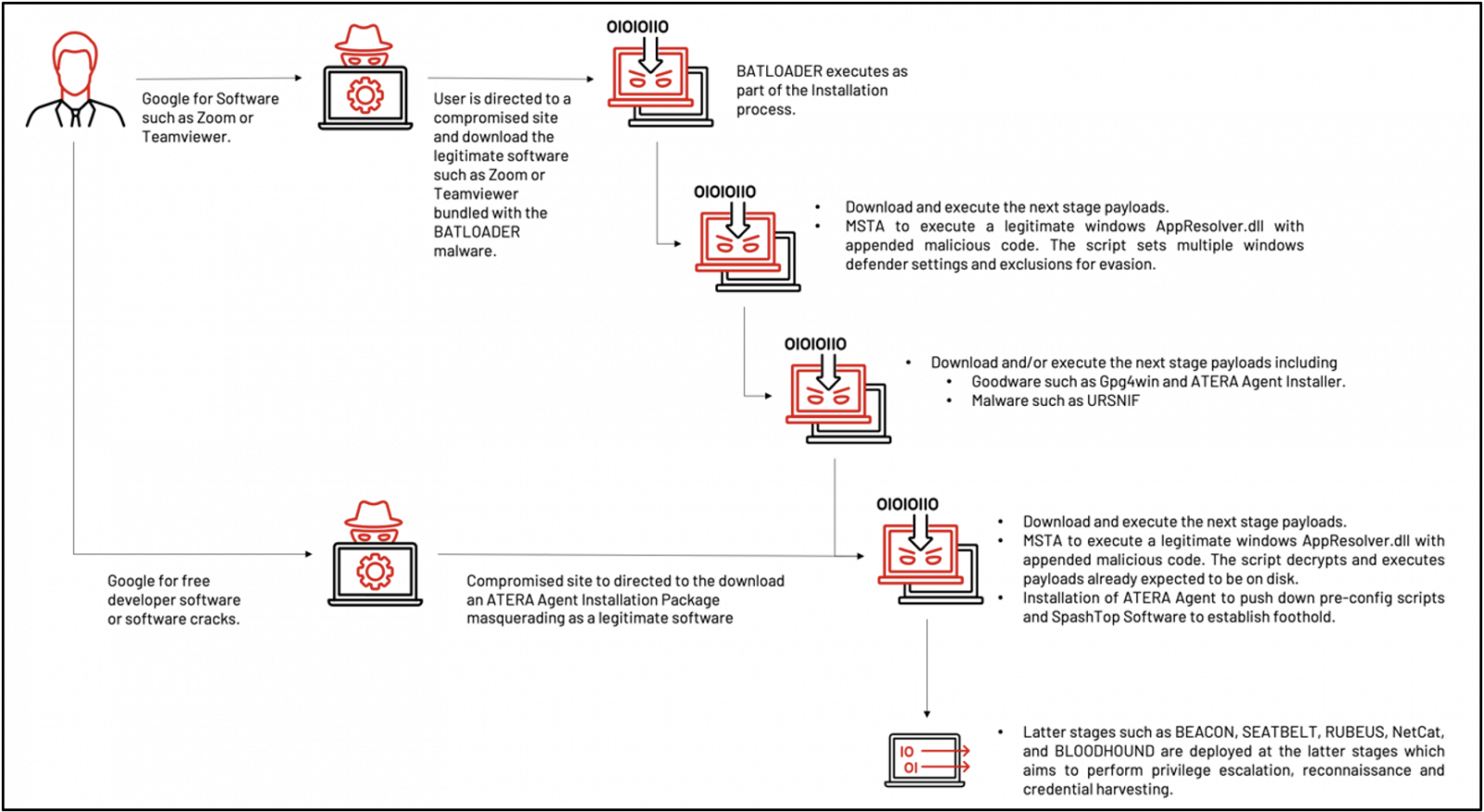
The threat actor used “free productivity apps installation” or “free software development tools installation” themes as SEO keywords to lure victims to a compromised website and to download a malicious installer. The installer contains legitimate software bundled with the BATLOADER malware. The BATLOADER malware is dropped and executed during the software installation process. (…) This initial BATLOADER compromise was the beginning of a multi-stage infection chain that provides the attackers with a foothold inside the target organization. Every stage was prepared for the next phase of the attack chain. And legitimate tools such as PowerShell, Msiexec.exe, and Mshta.exe allow proxy execution of malicious payloads to avoid detection.
Two Infection Chains Delivering Malware Payloads
After users execute the program they downloaded, two infection chains will be triggered. These will have the role to perform malware payload dropping on the targeted device.
In the first infection chain phase, a false software linked with BATLOADER malware will be installed, then payloads like Ursnif and Atera Agent will be executed.
The second infection chain handles the dropping of ATERA Agent, together with the fact that malware loading is bypassed.
The two mentioned infection chains were depicted by the researchers mentioned above in the following illustration.
What Malicious Domains Have been Employed in This SEO Poisoning Campaign?
As researchers have stated, the following compromised domains were leveraged in this hacking campaign:
- cmdadminu[.]com
- zoomvideo-s[.]com
- cloudfiletehnology[.]com
- commandaadmin[.]com
- clouds222[.]com
- websekir[.]com
- team-viewer[.]site
- zoomvideo[.]site
- sweepcakesoffers[.]com
- pornofilmspremium[.]com
- kdsjdsadas[.]online
- bartmaaz[.]com
- firsone1[.]online
How Can Heimdal™ Help?
Threats at the domain level represent the new normal nowadays. That is why an efficient cloud-based security solution is the answer to this problem. Try out our awarded Threat Prevention, an outstanding DNS traffic filtering that has found the perfect way to mix together ingredients like Machine Learning, cybercrime intelligence, and AI-based prevention into a perfect cybersec recipe that safeguards your business-critical assets from DNS threats with an accuracy of 96%. No time to get hacked as you are busy taking threat hunting to the next level!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










