Contents:
Microsoft noticed a wave of cyberattacks that use SEO poisoning, also known as search poisoning, to deliver a remote access trojan (RAT) employed by cybercriminals to steal private information from the infected systems.
SEO poisoning is an old-school attack technique in which threat actors create malicious websites and utilize search engine optimization (SEO) strategies to make them appear prominently in search results.
These websites are usually associated with words that large numbers of individuals are likely to be using in searches at any given point in time, including holiday phrases, news items, and popular videos.
In this situation, the attackers behind the SolarMarker malware use thousands of PDF documents packed with SEO keywords and links that lead potential victims to malware on a malicious website that pretends to be Google Drive.
As stated by Microsoft, the attack works by using PDF documents created to rank on search results. To accomplish this, threat actors stuffed these documents with more than 10 pages of keywords on a wide range of topics, from “insurance form” and “acceptance of contract” to “how to join in SQL” and “math answers”.
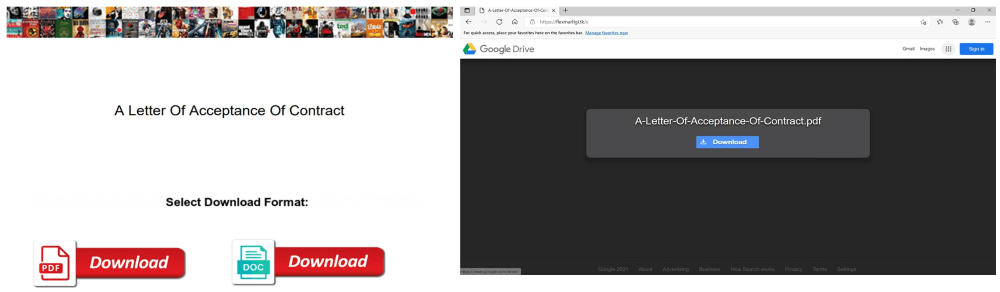
SolarMarker Operation Mode
According to the Microsoft Security Intelligence team, SolarMarker, also known as Jupyter, Polazert, and Yellow Cockatoo, is a backdoor malware that steals data and credentials from browsers. It exfiltrates stolen data to a C2 server and persists by creating shortcuts in the Startup folder as well as modifying shortcuts on the desktop.
In April, security specialists from eSentire noticed cybercriminals behind SolarMaker deluging search results with over 100,000 web pages announcing to provide free office documents such as templates, invoices, receipts, questionnaires, and resumes.
This way, business professionals looking for document templates would be tricked into infecting themselves with SolarMaker remote access trojan (RAT) employing drive-by downloads and search redirection via Shopify and Google Sites.
In more recent attacks seen by the Microsoft Security Intelligence team, the threat actors have switched to keyword-filled documents held on AWS and Strikingly, and are now also attacking financial and educational areas.
eSentire’s Threat Response Unit (TRU) stated:
The TRU has not yet observed actions-on-objectives following a SolarMarker infection, but suspect any number of possibilities, including ransomware, credential theft, fraud, or as a foothold into the victim networks for espionage or exfiltration operations.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










