Contents:
The U.S. Department of Justice (DoJ) announced on December 19th that the Federal Bureau of Investigations had disrupted the BlackCat ransomware threat group’s activity.
The FBI offered a decryption tool to more than 500 affected victims. They also encourage potentially unknown BlackCat/ ALPHV victims to speak up.
While the event is largely discussed across the cybersecurity world, I’ll resume the essential facts about what happened.
Did the FBI take BlackCat out of business?
- BlackCat’s dark web leak portal went offline on December 7th but went back on five days later.
- The Federal Bureau of Investigation (FBI) announced on December 19th that they’ve seized BlackCat’s Tor leak site.

- Few hours later, BlackCat unseized the domain and threatened to attack US’ critical infrastructure.
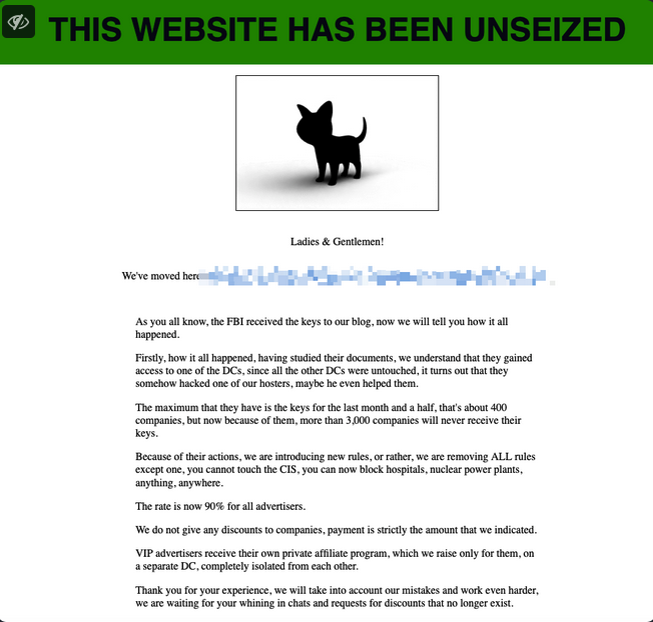
- BlackCat also claimed they’ve moved their servers and blogs and said that the FBI only got “stupid old key” for an old site. They posted 5 new victims on their new site, to prove they are still operational.
- For the moment both the hackers and the law enforcers have the private keys associated to the threat group’s data leak site. The website now displays the FBI message.
- The FBI collected 946 public/private key pairs that the threat actors used to host the TOR sites. The Federal Bureau took down several BlackCat websites.
- The authorities made no arrests in this case.
More about the FBI decryption tool
- Dozens of victims in the U.S. were involved in implementing the decryptor.
- The decryption tool helped avoid payment of ransom demands totaling $68 million.
- According to BlackCat the FBI decryptor only solves the encryption for 400 companies. Hackers claim additional 3,000 companies will never regain access to their keys.
Context Details
BlackCat, aka ALPHV, and Noberus appeared in December 2021 and became the second most productive ransomware-as-a-service. It has developers that create ransomware and a spreading infrastructure, while affiliates target and attack victims.
The group uses a double-extortion tactic. They steal sensitive data before encryption, then demand ransom for decryption. If victims refuse to pay, BlackCat publishes the stolen data on a dark web leak site.
According to FBI, during the last three months alone ALPHV Blackcat affiliates have compromised over 1000 entities. The attackers asked for more than $500 million total ransom. They received about $300 million.
With a decryption tool provided by the FBI to hundreds of ransomware victims worldwide, businesses and schools were able to reopen, and health care and emergency services were able to come back online. We will continue to prioritize disruptions and place victims at the center of our strategy to dismantle the ecosystem fueling cybercrime., said Deputy Attorney General Lisa O. Monaco
Source – US Department of Justice press release
What next?
BlackCat is still operating, so they’ll probably keep launching ransomware attacks.
On December 19th, CISA and FBI issued a joint advisory announcing they have updated the FBI FLASH BlackCat/ALPHV Ransomware Indicators of Compromise. The document was initially released on April 19th, 2022.
The advisory also contains safety recommendations against ransomware.
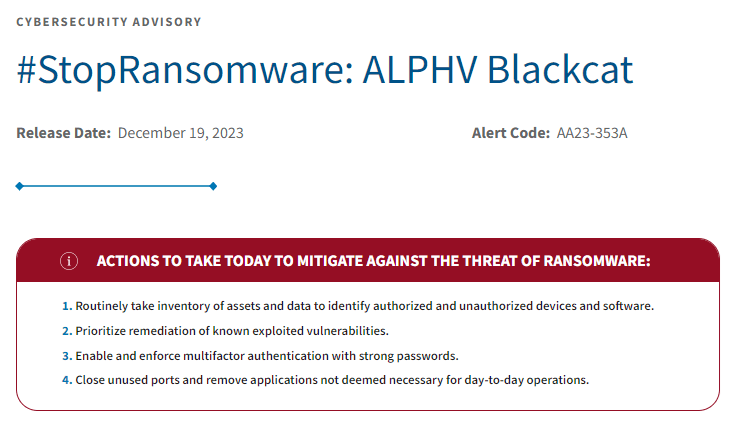
Source – The Cybersecurity and Infrastructure Security Agency (CISA) advisory
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







