This post is authored by Heimdal’s Cybersecurity Architect and Technical Product Marketing Manager Andrei Hinodache.
You may know him as the face of our popular series of webinars. If you want to watch the full webinar this EDR strategy guide is based on, check out the recording here.
If you want to understand why effective threat detection is so important, take a look at this image:

That’s right: In 2023, there were almost 15 billion breached accounts across the world. That’s more breached accounts than there are humans on the earth to access them.
That headline figure is cause enough for concern, but it gets more urgent when we see where the major attacks are taking place: Europe, Russia, Australia, and the US.
In fact, there’s a pretty good chance that you’re reading this blog from one of these locations.
So here is the million-dollar question: How do we ensure our accounts aren’t among the 15 billion?
As a cybersecurity expert at Heimdal, I know just how complex this question can be to answer.
In reality, no single solution is going to guarantee your safety. Instead, you need a comprehensive, layered approach to detecting and responding to threats and vulnerabilities.
Over the years, I’ve developed a matrix to try and sum up the vast web of different tactics, technologies, processes, and methodologies that this layered approach should include. In this blog, I explain my approach across five main sections:
- Mitigate the entry points
- Deploy fierce reactive security
- Ensure reliable visibility
- Ensure effective actionability
- Mitigate the human factor
Defend your entry points
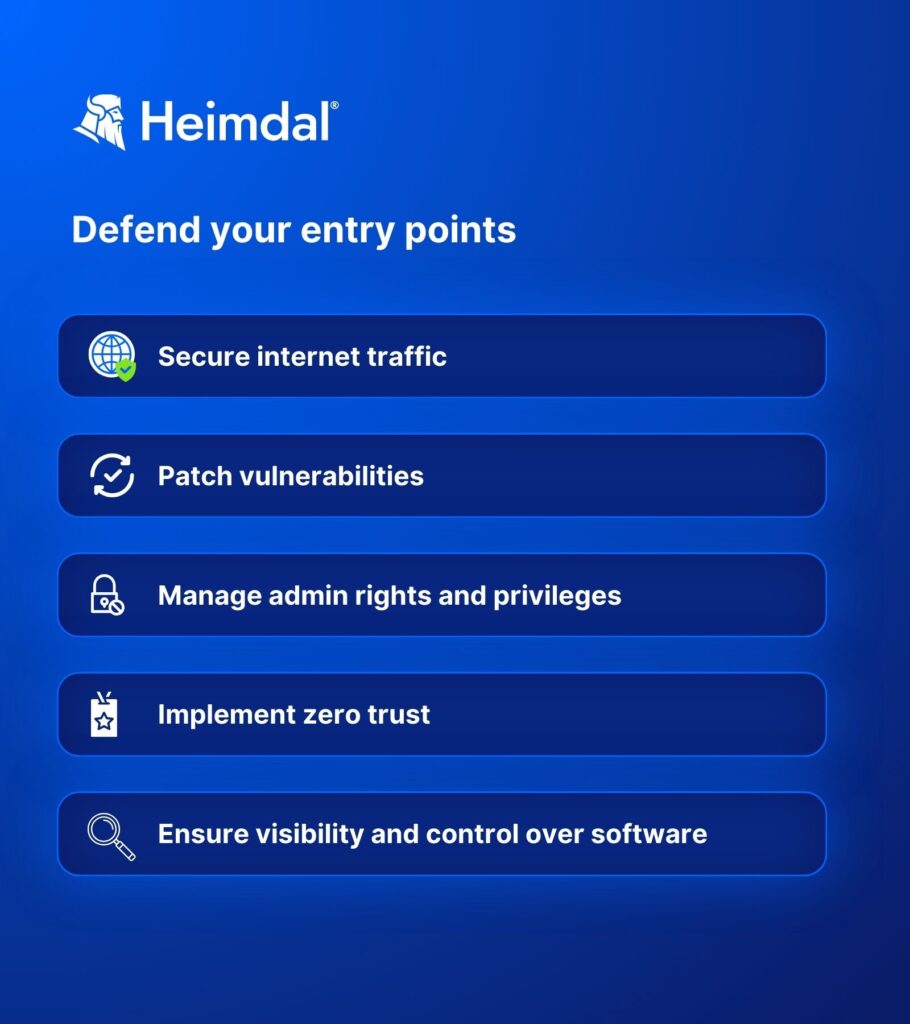
Whatever a hacker is trying to achieve, they’ll need to either gain access to your IT environment or find some way of intercepting data in transit. There are several different approaches available to them at this stage.
They might, for instance, directly target an admin account, which would give them many of the rights they need to pull off a successful attack.
More likely, they’ll aim to evade detection by infiltrating a non-admin account and moving ‘laterally’ to gain extra privileges.
Needless to say, the best way to stop a hacker is to prevent them from gaining initial access. There are a few ways to do this:
Secure internet traffic
Hackers often try to intercept or alter internet and other connections in order to steal data in transit, insert malicious code, or redirect the user to a phishing page.
DNS and endpoint monitoring tools can avoid this by filtering out common malware deployment attempts and using anomaly analysis to identify advanced threats.
Read more: What Is DNS Security and How Does It Work [A Comprehensive Guide]
Patch vulnerabilities

- Thomas Engli Baasnes, Cybersecurity Director, Verdane
Unpatched vulnerabilities are a common way for hackers to both gain entry to the environment and elevate their privileges.
To avoid this, you should implement a process to identify and remediate the most critical vulnerabilities in a timely manner
Platforms like EDRs and XDRs can help identify and prioritize unpatched vulnerabilities in your environment.
When deciding which patches to apply first, you should also consider how the risk relates to your specific IT assets and the data they store.
Read more: How To Break The Metrics Mirage in Vulnerability Management
Manage admin rights and privileges
Most of the actions a hacker is looking to complete will require elevated rights. This can include stealing sensitive data, reconfiguring IT assets, installing ransomware, and more.
To protect against this risk, it’s important to reduce the amount of privileged accounts and credentials to an absolute minimum.
The logic is simple: fewer super-user accounts means less chances for the hackers to gain high-level permissions if they breach one of them.
Read more: Admin Rights in Action: How Hackers Target Privileged Accounts
Apply the principle of least privilege
The principle of least privilege (PoLP) doesn’t just apply to privileged accounts. In fact, you should also ensure that non-privileged users only have access to the files, applications, and assets that are absolutely essential for their roles.
This is another crucial way to reduce your overall attack surface.
A good way to do this is to implement role-based access controls (RBAC) that delegate access based on job titles.
Alternatively, just-in-time access takes least privilege a step further by only giving admin rights for specific reasons and time-limited periods.
Implement Least Privilege with Ease!
See How It Works.
Ensure visibility and control over software
Accounts, credentials, and privileges now increasingly exist at the application level as well as on the operating system.
This can make it particularly difficult for IT to audit and manage these accounts, which is essential if you want to effectively implement least privilege.
This is where the phenomenon of ‘shadow IT’ becomes such an issue – when employees use software or apps that aren’t sanctioned or monitored by IT.
If this happens, you’ll have no visibility and control over that software. It will limit your ability to monitor malicious activities and remediate vulnerabilities before hackers find and exploit them.
Therefore, you need a range of tools to inventory, monitor, and control the apps that people use across the organization.
XDR solutions are generally best placed to help with this challenge. To do this, they offer several features to monitor user behavior and either blacklist or whitelist specific applications. This gives you visibility and control over what apps are in use, by whom, and how they’re being used.
Read more: Application Allowlisting: Definition, Challenges & Best Practices
Deploy fierce reactive security

The points in the last section are an effective first layer of defense, but they can’t guarantee safety.
After all, fewer admin accounts isn’t the same as no admin accounts. So what’s the next stage?
You also need a range of tools that can identify risky behavior within the IT environment.
The goal is to detect and lock down accounts and endpoints that the hacker has already infiltrated, creating an effective second layer of defense.
Failing that, these tools and processes should make it more difficult for them to move laterally, perform reconnaissance, and escalate privileges:
Brute force protection
Brute force attacks include repetitive attempts to guess passwords or other credentials.
Often, hackers will try common passwords (e.g. Password123) on all accounts in the hope of striking gold. Alternatively, they might deploy bots to generate random passwords until they get the right one.
These techniques are unsophisticated, but they’re surprisingly effective.
Nonetheless, a set of fairly simple password policies can help to avoid most of these issues.
This includes locking accounts after three unsuccessful login attempts, as well as enforcing strict controls about how strong and unique passwords can be and how regularly they should be changed.
Read more: What Is a Brute Force Attack?
Powerful and adaptive NextGenAV/XDR
Tools like XDR, SIEM, and next-gen antivirus are specifically designed to identify real time threats:
- vulnerability exploits
- malware injection
- man-in-the-middle attacks, etc.
Try Heimdal's Next-Gen Anti-Virus: Schedule a Live Demo Now!
Get a Demo
First these tools scan and filter out specific known issues like malware. This is very similar to how traditional antivirus and anti-malware tools work.
But the process doesn’t stop here. These tools can also identify certain emerging and unknown threats.
Generally, they do this by monitoring and analyzing all user behavior and external connections across the IT environment to identify suspicious activity.
Often, hackers are trying to move laterally through the IT environment, research security vulnerabilities or systems, and remove evidence of their activity.
Since behavior like this is generally pretty strange, it can often be detected using anomaly analysis algorithms.
When suspicious behavior is detected, you can lock down the user accounts.
You should also implement multi-factor authentication, as an additional layer of protection. Thus, you can ensure the user is who they say they are.
Read more: What Is Next-Generation Antivirus (NGAV) and How Does It Work?
Encryption protection
A successful ransomware attack is one of the worst security issues that can happen to a company. These tools work by encrypting your company files and demanding a ransom to release them.
If you don’t pay the ransom, there’s a good chance you’ll lose access to critical files and data, which could force the business into bankruptcy.
Luckily, if you’ve implemented the rest of the advice on this list, it will be very difficult for hackers to pull off a successful ransomware attempt.
Nonetheless, ransomware encryption protection can act as a vital last line of defense, defending your IT environment from attempts to encrypt your data.
They do this using anomaly analysis algorithms that can detect file encryption through behavioral analysis.
When suspicious activity is discovered, the system can lock down any immediate risk and inform the IT team immediately.
Find out more: Heimdal’s ransomware encryption protection helps ensure hackers can’t encrypt your data with malicious ransomware.
Read the full product page.
Aggressive email security
Hackers regularly use phishing techniques to gain access to accounts and elevate their privileges. They’ll do this by redirecting users to fake websites that prompt employees to provide their login details.
Email security and XDR tools can help avoid this by proactively identifying suspicious emails and removing them from the user’s inbox.
Then, IT teams can securely open these to investigate any potential attacks.
Read more: Why Do Organizations Need an Email Security Policy?
Enable reliable visibility
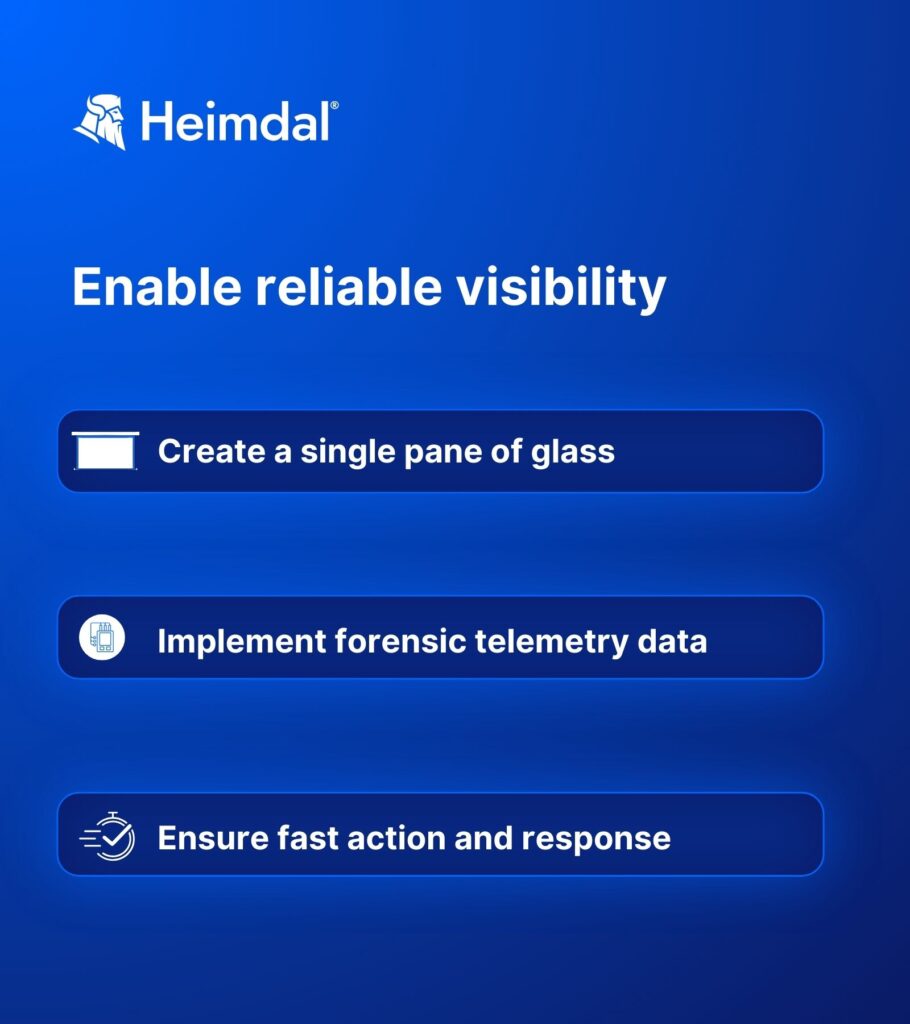
A bird’s eye view over all the accounts, privileges, processes, and apps in the IT environment helps spot real time attacks.
Gaining full visibility has always been a challenge for IT teams.
It’s even more difficult to achieve now, in a world where employees sign up for cloud apps through their browsers and download work files onto personal devices.
To mitigate these issues, businesses now use an increasingly complex range of tools to track how employees are interacting with the IT environment and understand what tools they’re using. But this creates an additional risk. Often, the vast range of point solutions simply causes additional risks.
So how do you get it right? Here are some important points to consider:
Creating a single pane of glass

- Thomas Engli Baasnes, Cybersecurity Director, Verdane
The most up-to-date security products are increasingly beginning to consolidate functionality from disparate cybersecurity tools. This includes:
- XDRs, combining EDR, EMM, SIEM, and SOAR products
- UEMs, combining MDM, MAM, and EDM, and others
Taking advantage of tools like this is one of the best ways to reduce licenses and improve your security posture.
Ideally, these tools should combine a variety of risk signals into a single dashboard, so you can gain an effective bird’s eye view over everything that’s happening in the IT environment.
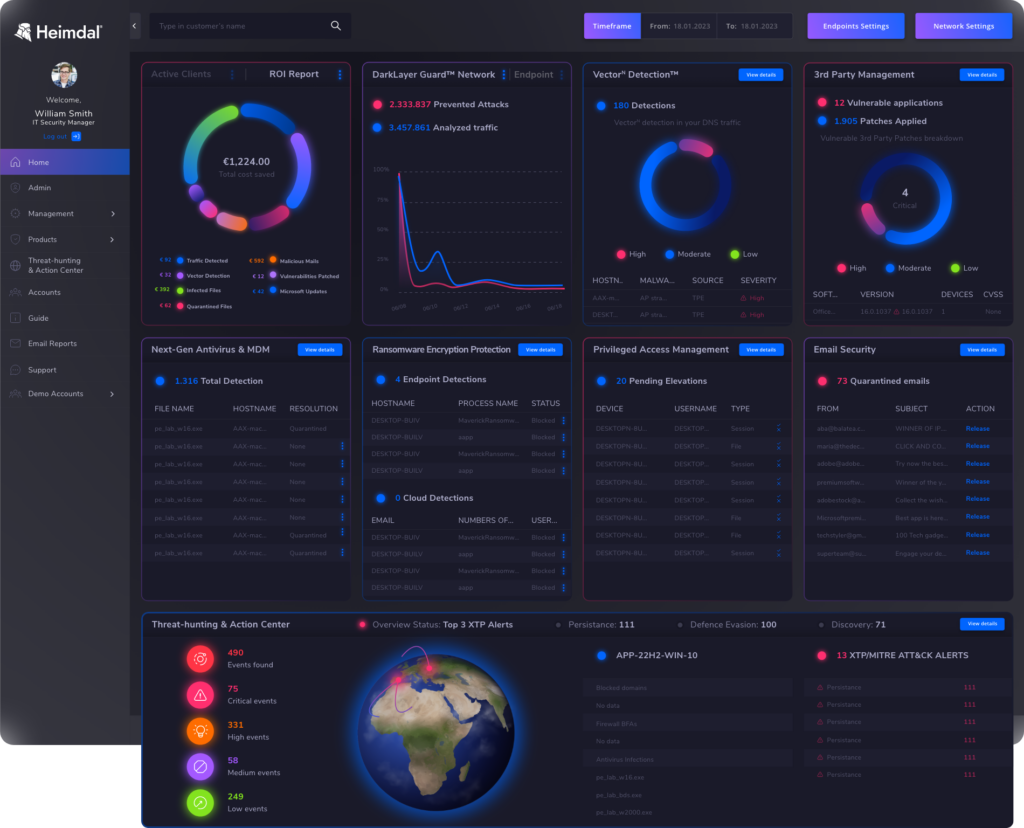
At Heimdal, we do this by combining a whole range of tools into a single cybersecurity platform. In fact, Heimdal’s XDR is the widest and fully modular platform in the industry. It includes:
- Vulnerability management
- Email security
- DNS security
- Real time threat detection
- Privileged access management
- Ransomware encryption protection
Read more: Cybersecurity Silos Disrupt Your Defense. See How Unified Security Platforms Prevent it
Protect every endpoint with Heimdal's unified cybersecurity platform!
Discover Heimdal's all-in-one security solution here.
Implementing forensic telemetry data
When a hacker first gains access to your systems, they’re probably not planning to execute the attack immediately. Instead, they’ll work to elevate their privileges, as well as ‘move laterally’ through your IT environment to understand your defenses and cover their tracks.
You’ll want to identify and lock down their behavior as soon as possible, to reduce the potential for damage and escalation.
Therefore, you’ll need tools that can identify hackers as they move through your IT environment, including XDRs, SIEMs, and more.
Generally, these products do this by analyzing ‘telemetry signals’, or user behavior and identifying anomalous or suspicious activity.
Ensuring fast action and response
When suspicious activity is detected, you’ll need to understand what’s happening before you decide on the response.
But every second you spend working out what’s going on is precious time the hacker can use to further infiltrate your IT environment and escalate their attack.
Master cybersecurity incident response with Heimdal!
Download our FREE incident response template here.
Therefore, it’s crucial that you quickly identify and categorize threats, so you can deploy the right response.
The best way to do this is using the MITRE ATT&CK framework.
This is a common model for classifying attacks and tactics, used widely by cybersecurity professionals and products across the industry. Using this framework helps you respond faster and more effectively in case of an incident.
Read more: Automated Incident Response: What You Need to Know
Ensure effective actionability
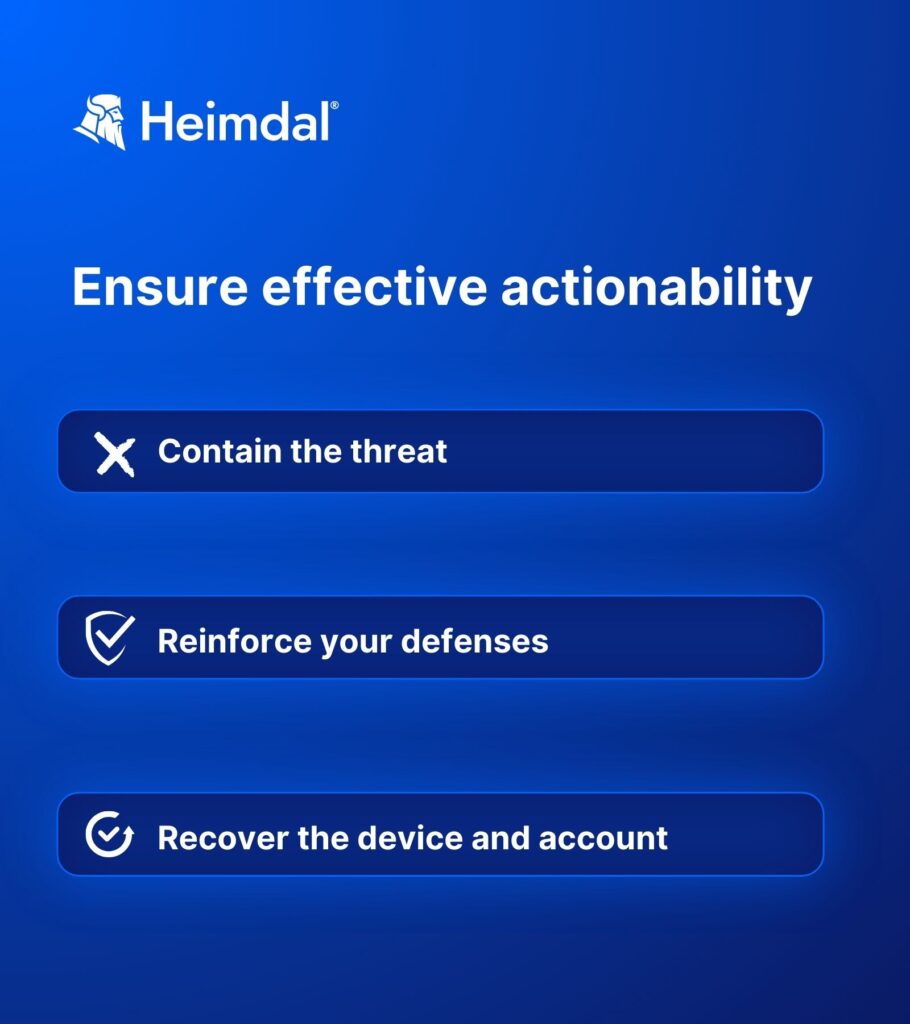
At this point, you’ve identified the suspicious behavior and categorized the threat. The next stage is to respond to the attack and lock it down, as quickly as possible.
The best way to do this is through automation. Using XDRs, SOARs, and more, you can design a range of policies that can respond to specific threats when detected.
This can be as simple as requiring a user to complete multi-factor authentication when they log in on a different device or location. Here, it’s just a case of adding an extra layer of security without the IT team having to be a bottleneck.
But if evidence of malicious activity, lateral movement, or reconnaissance is detected, you’ll need fast response measures at your fingertips:
Contain the threat
To eliminate the immediate danger, you’ll need to either isolate the affected machine or lock the user’s account. This will buy you time to investigate the threat and its ramifications.
Ideally, this should be done instantly and automatically when suspicious behavior is detected.
It would either stop the hacker entirely or significantly limit their ability to do damage.
Reinforce your defenses
You could also strengthen your reactive defense by locking down infected IP, files, or processes.
This is one of several automated responses you can configure when particular threat signals are detected.
The measure ensures that infected files cannot be executed on the infected machine or any other company resources.
Recover the device and account
You’ll also need a process to return to normal operations once the attack has been mitigated. To do this, you’ll need to analyze the hackers’ behavior to understand how they entered the environment and what they did there.
Crucially, you’ll need to ensure that there’s no residual danger, including hidden backdoors, compromised credentials, or residue malware. Then, you can unlock the affected accounts and return to normal operations.
Mitigate the human factor

Effective cybersecurity involves three key factors
- processes
- technology
- people
Most of the article so far has focused on the first two. But without the right training or processes, employees can easily become the weakest link in your defense. Here’s what you need to keep in mind:
Enforce strong password controls
Weak passwords are a hugely attractive entry point for hackers, which they can often exploit using brute force tactics.
Luckily, a range of simple policies can help ensure employees don’t resort to duplicated or easily guessable passwords.
This can include policies to ensure passwords are unique, regularly changed, and have a certain number of special characters. Combine this with multi-factor authentication where possible to create an extra layer of defense.
Invest in thorough employee training
Employee training also has a key role to play in creating an effective cybersecurity defense. Well trained employees can create an effective extra line of defense if they know what they’re looking for.
Often, employee training starts and ends with phishing, since these attacks specifically target end users. But in fact, a whole range of anomalous behavior can be spotted by employees. This could include other employees accessing files, apps, or systems they wouldn’t usually need to use – potentially at strange times.
Create a foolproof offboarding process
Often, organizations have far more user accounts in their IT environment than they need.
This is because it’s too easy for the IT team to forget to remove accounts and de-escalate privileges when they’re no longer needed. But just because an employee has left the company, doesn’t mean their account can no longer be hacked.
Over time, this ever-expanding web of accounts and privileges can drastically increase your overall attack surface.
Therefore, it’s important to create a robust process to ensure accounts are removed when employees leave the company. You should also regularly audit accounts and privileges to detect any that the IT team has missed or lost track of.
Heimdal XDR: Reduce complexity, boost security, cut costs

If there’s one running theme throughout this whole piece, it’s this: IT environments are more complex than ever. This has created a whole range of new entry points and tactics for hackers to use. At the same time, it has made the challenge of securing these various attack vectors harder and harder.
The cybersecurity market is starting to understand why that complexity is one of the biggest single risks to your IT environment.
That means cybersecurity products are moving from solving one very specific problem to consolidating as much functionality from siloed tools as possible.
Heimdal is right at the front of this trend. In fact, we’ve taken it a step further than anybody else on the market by consolidating the widest possible range of security tools in one license, including:
- DNS security
- Vulnerability management
- Privileged access management
- Email and collaboration security
- Unified endpoint management
- Threat hunting
Heimdal’s XDR platform gives you all the tools you need to reduce complexity and overlapping security licenses, while improving overall security.
Ready to get started? Get your custom Heimdal pricing quote.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








