Endpoint detection and response (EDR) is one of the most important and fundamental cybersecurity products on the market.
Effectively, it acts as a modern-day, cloud-based defense against viruses, malware, and a whole range of other real-time cyber threats.
And of course, as with many others there are also some EDR best practices you can take into consideration to improve your experience.
But to get the most out of the tool you’re installing, you need to understand what these threats are targeting and how you can set your EDR product up to best respond to them.
Keep reading to find out how to do just that.
Extended Detection And Response: Context, Basics, And Definitions
Before we can explain how effective endpoint security works, it’s helpful to clarify a few terms first.
There are several different types of endpoint detection tools on the market, each with a slightly different objective, scope, and toolset.
Here are the main terms you need to know:
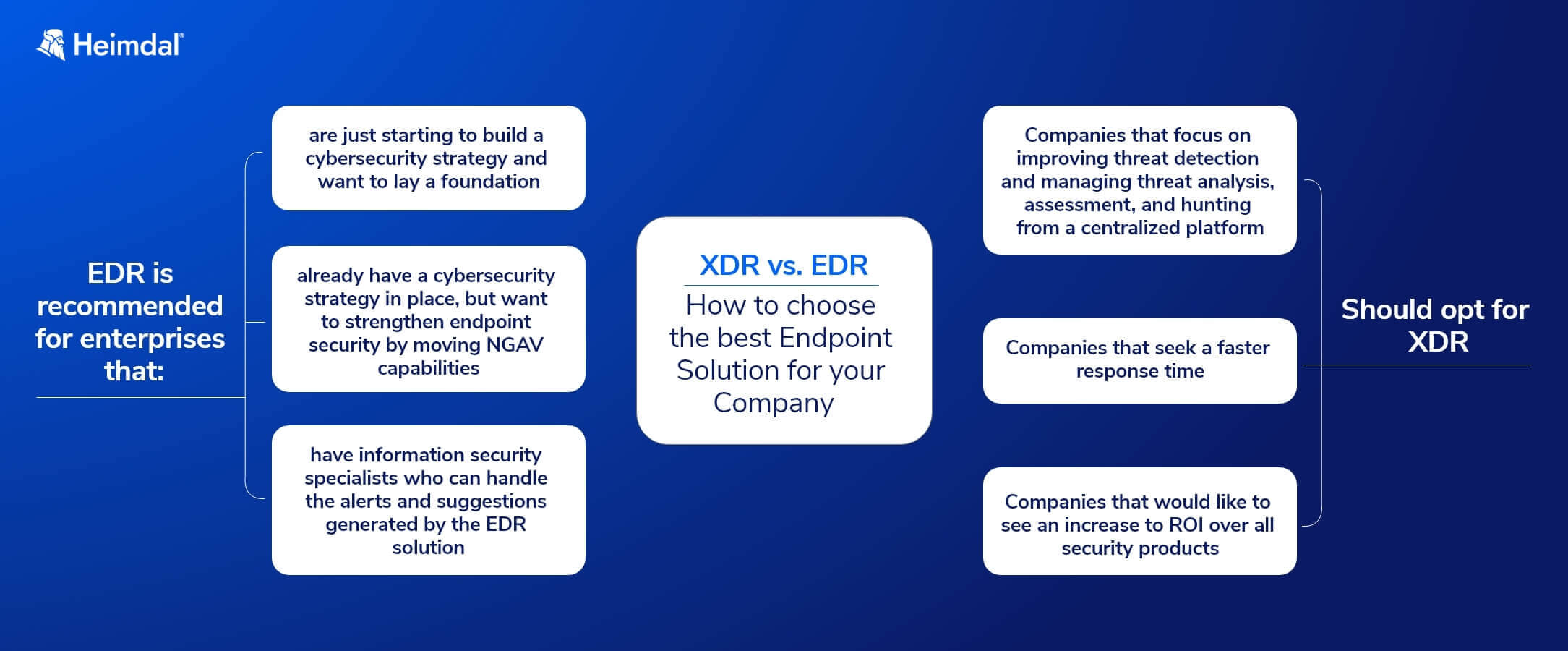
1. Endpoint Detection And Response (EDR)
EDR products are the default setting for endpoint protection.
They involve a series of tools to detect and protect a whole range of devices in your environment.
This includes state-of-the-art antivirus and anti-malware protections, as well as real-time behavioral monitoring to identify potential hackers.
2. Extended Detection And Response (XDR)
XDR products have all the same features as a standard EDR product, but they’re generally packaged into a much wider and more holistic cybersecurity suite.
The best of these include tools like privileged access management, vulnerability management, DNS security, email security, and much more.
Where endpoint detection is concerned, you can consider EDR and XDR pretty much interchangeable – the only difference is what other cybersecurity tools are also available.
Read more: XDR vs. EDR: A comparison
3. Mobile Device Management (MDM)
MDM products help security teams remotely manage mobile devices such as tablets or smartphones.
These tools evolved because traditional endpoint security solutions weren’t built to manage remote devices.
However, this is less likely to be the case with the most modern EDR and XDR tools. While MDM functionality is important – it’s often more effective to get this through a wider security solution than in a self-contained MDM product.
4. Managed Detection And Response (MDR)
Cybersecurity providers generally offer managed services alongside their EDR or XDR products, usually as an optional add-on. In these cases, the resulting service is referred to as MDR.
Generally, the underlying technology involved in a ‘managed’ solution will be the same as with the standard EDR or XDR product; the only difference is whether or not the customer chooses to opt-in to managed support.
This can be via the vendor themselves or through a third-party managed security service provider.
Read more: Top Managed EDR Benefits That Reduce Cybersecurity Risk
5. Security Information and Event Management (SIEM)
SIEM products fulfill a similar role as EDRs, but they tend to focus more on the broader IT environment than the specific endpoint devices within it.
By analyzing log files, they can monitor realtime ‘events’ in your IT environment to find patterns, create alerts, and highlight potential risks.
Unlike EDR products, however, they don’t tend to include antivirus and antimalware protections.
There is significant overlap in functionality between all the products listed above, so you could be forgiven for still not really understanding which is best for you.
Generally, the best approach is to find a product that gives you as much functionality as possible under a single license. For most medium-sized businesses and larger, this is probably going to be an XDR platform – since it’s by far the most expansive solution on this list.
8 EDR Best Practices for Effective Threat Detection and Response
It’s easy to think that the best way to implement EDR is to find the most expansive tool on the market, press install, and let it do its magic.
Sadly, it’s a bit more complicated than that – and there are many pitfalls that you need to be aware of as you roll out the new solution.
To help you get it right, here are the 8 most important best practices you need to be aware of:
1. Understand Where Risk Lies
Before you can effectively use your EDR tool, it’s important to understand what data exists in your organization, where the risk lies, and what’s in most need of protection.
Not all data is equally as sensitive to the organization or valuable to hackers.
For devices and endpoints, this is comparatively easy; an effective EDR tool should be able to scan and identify all the devices in your network.
From there, you can identify the most sensitive assets – generally anything involving critical servers, customer-facing applications, and anything that could cause significant damage to revenue or reputation if affected.
For data, things are a bit more tricky – because no scan can really quantify how critical a file is to your organization or the material cost of a breach.
Here, you’re going to have to use your judgment. Luckily, there are a few patterns. Generally, your most sensitive data will be anything that involves personally identifiable information (PII), intellectual property, or trade secrets.
So why is this so important? Essentially, it’s about picking your battles. It’s not helpful to be constantly responding to minor alerts on non-sensitive assets – and indeed there’s a good chance you’ll miss the most important alerts if you do.
Instead, you should target your policies where they’ll be the most effective.
Read more: How to Conduct a Cybersecurity Risk Assessment (2026)
2. Use a Layered Approach
Let’s pretend that a hacker is trying to gain access to your business environment through a phishing strategy directed at a non-technical sales executive, who we’ll call Jane.
Luckily, Jane works for a savvy organization that’s put multiple defenses in place.
The first is an email protection platform that monitors incoming messages for suspicious signals, using anomaly analysis.
If successful, it can block or redirect the incoming phishing attempt, stopping Jane from seeing it in her inbox and allowing the security team to safely investigate the message later.
But let’s pretend that the email passes through these defenses undetected. It’s not likely, but it does happen. The next defense is Jane herself, who’s received extensive training and knows how to spot the warning signs of a phishing attack.
When she sees the message, she knows not to click the link and gets in touch with the IT team immediately to report the attempt.
This isn’t foolproof, however, and even the best-trained employees can make mistakes.
Let’s pretend Jane’s having an off day, forgets her training, and clicks on the link. The hacker gets the login details and attempts to access Jane’s account.
Luckily, the company has multi-factor authentication enabled for all logins from new devices and locations.
Moments later, Jane’s smartphone receives the notification, and she realizes her mistake. Then, she can reject the attempt, inform security, and change her login credentials.
It’s easy to think that the solution to new and innovative threats is to have the most expensive, wide-ranging cybersecurity solution on the market. But even the best security solutions aren’t infallible. By far the best approach is to have a range of defenses that can be coordinated from a single, integrated platform.
Most importantly, this should include defenses that can inhibit or lock down the hacker’s progress, even after they’ve accessed your IT environment.
3. Avoid Multiple Solutions

- Andrei Hinodache, Cybersecurity Community Leader
The cybersecurity market is full of self-contained products designed to do a single thing well. It can be tempting to string together several of these tools in an attempt to combine the best of all worlds. But this approach is fraught with risk.
The more tools you have, the less effective the whole solution is going to be – even if the constituent products that make it up are the best the market has to offer.
Firstly, multiple licenses are going to create more admin and confusion for the IT team (ie: you) that has to administer and monitor them.
But more importantly – it’s also bad for your overall security posture, because multiple tools create conflicting policies. If a hacker is trying to install malware on a remote device, the last thing you want is for your EDR and MDM products to trip over each other with conflicting policies that make the problem worse.
This is why security teams are increasingly trying to consolidate their cybersecurity products as much as possible. Done right, this will avoid conflict and confusion, without sacrificing the breadth of security functionality you need to stay safe.
Read more: Less Is More: Why MSPs Are Moving to the Cybersecurity Platform Model
4. Don’t Roll Out Everything All at Once
When you first install your EDR or XDR product, you’re going to have a number of decisions to make, including automations, policies, exceptions, alerts, and more. All these options will have a real impact on the everyday workflows of employees and customers.
Getting these policies right can take time, and it’s important not to create havoc while you’re experimenting.
So how do you avoid this? First, start in detect-only mode.
This lets you develop the intelligence you need to devise your policies without locking down key apps or workflows.
Next, it’s important to roll out your policies to a pilot group so you can identify any issues.
Generally, this will be proactive business users, technical teams, and executives. You should focus here on users with privileged access, since these are the people who the EDR will most likely affect.
This means you can test your policies in a controlled manner and receive feedback from engaged users who know what’s happening. Once you and the pilot group are happy, you can roll out the EDR across the whole IT environment.
5. Take Advantage of Automated Responses
No IT team has the bandwidth to manually review each event and decide how to respond. There are simply too many people, endpoints, and interactions in a business IT environment.
Instead, a robust tool should offer you a range of policies that can automate responses, based on particular triggers or events.
These automated policies are now pretty standard across EDR and XDR tools – though some have more granular security controls and flexibility than others.
The main benefit of automation is it avoids your IT team having to respond to each potentially risky event.
The vast majority of risk signals are still fairly harmless – like users signing in from a new device or location. Here, you might want to build automated policies to require extra verification (ie MFA) – but there’s certainly no need for your IT team to get involved in every sign-in attempt.
But crucially, an automated EDR/XDR can also offer a more efficient response when genuinely risky behavior is detected, generally by locking down the account until the IT admin has the time to investigate. This avoids any further damage or lateral movement being done while the admin responds.
Then, you can investigate calmly and logically in your own time – safe in the knowledge that any dangerous behavior has been stopped.
Read more: Automated Incident Response: What You Need to Know
6. Be Careful of False Positives
Even the most advanced products on the market can’t correctly identify suspicious behavior with 100% certainty.
The vast majority of events are perfectly normal and pose little to no risk. Some will be so anomalous that they have ‘cyberattack’ written all over them – and you can create automated policies to quickly lock the affected account in these cases.
But for events that fall somewhere between, the situation can be more tricky.
This is where false positives come in. These are normal events that for one reason or another are flagged as risky.
The challenge is that the more false positives your EDR product identifies, the more time your team is going to spend manually reviewing them. Crucially, it also makes it much easier for a genuine attack to slip through the defense – since it’s harder to spot it through all the noise.
So what’s the solution? EDR tools have different methodologies for identifying anomalous activity.
Some of these are better at avoiding false positives than others – so it can be helpful to go through the user reviews of a chosen platform to see what other business users think.
Perhaps more importantly, however, the tool needs to allow you the flexibility to customize your own policies.
To reduce false positives, it’s important to prioritize your security measures, automations, and policies on the assets or data that are most sensitive.
Where possible, automation should be used to avoid the IT team needing to step in.
Ultimately, the best approach is to have a flexible, customizable security platform that puts you in the driving seat of where those policies can be best targeted and how much risk you’re willing to accept.
7. Adjust, Adapt, Respond
Effective cybersecurity isn’t a case of setting up policies and putting your feet up.
Every decision you take is a balancing act between the amount of admin required for IT teams, the amount of restrictions end users have to manage, and the amount of risk you’re willing to accept.
Few organizations are going to get this balance right from day one. Instead, it’s important to monitor, test, and audit.
Ultimately, you want to keep your eye on how much friction your policies are creating, how many false positives you have to review, and where the biggest risk signals are being detected.
Most EDR and XDR products will collect the data you need to monitor this – you just need to keep your eye on it and adjust your policies over time.
You should also keep a line of communication open with employees so you can understand the amount of friction your policies are creating, and the associated business impact. This will allow you to continuously review and monitor your policies to ensure you’re striking the right balance.
8. Use a Modern XDR Platform
Read more: What Is XDR (Extended Detection and Response)? Features, Benefits, and Beyond
As we’ve explained elsewhere in this piece, having a series of siloed and disconnected tools can be a real issue for cybersecurity.
It creates rising costs, extra admin, overlapping functionality, and confusion about what tools should deal with which issues.
That’s why we developed the Heimdal® XDR platform, which offers a single one-stop shop for all your cybersecurity requirements, regardless of the technology you’re using, the endpoints you’re monitoring, or the data you’re protecting. This means no more clicking between SIEMs, SOARs, EDRs, MDMs, and more.
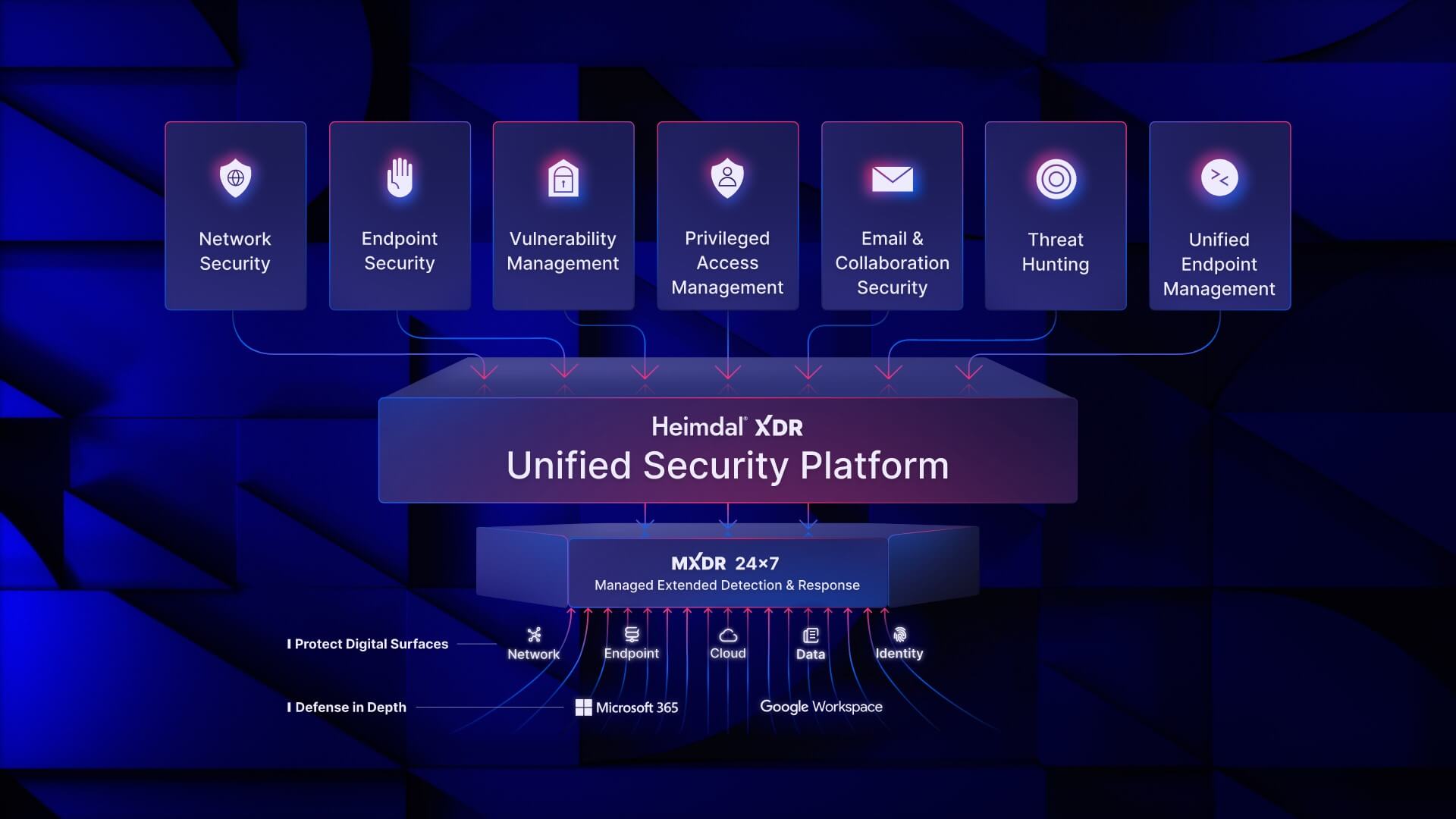
Instead, we offer a single dashboard through which a whole range of different cybersecurity tools can be accessed, managed, and deployed, including:
- Network security
- Endpoint security
- Vulnerability management
- Privileged access management
- Email and collaboration security
- Threat hunting
- Unified endpoint management
Check Out the Widest Cybersecurity Platform on the Market! Schedule a Live Demo With Heimdal Now!
Heimdal®: One Dashboard, One License, All the Functionality

- Andrei Hinodache, Cybersecurity Community Leader
Increasingly, the secret to effective cybersecurity is to find whichever product offers you the largest amount of functionality under one license.
If this is your goal, Heimdal® is by far the most effective choice. The vast majority of other cybersecurity providers will split their security tools across different products and licenses, creating more confusion and less effective security.
With Heimdal®, you get all these modules under a single license, and accessible through a single dashboard. Get lower costs, less confusion, and better security with Heimdal®.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








