Contents:
DNS filtering is a security process that companies use to block malicious communication and protect against cyberattacks.
DNS filtering solutions prevent users from accessing untrusted, harmful domains. Also, IT admins use DNS filtering to prevent users from accessing malicious websites.
Key takeaways:
- DNS-level security can prevent ransomware attacks and data leaks
- Filtering tools stop hackers from gaining initial access through phishing attacks
- Common DNS filters include category and content filtering
- You can automatize web filtering
How Does DNS Filtering Work
When you click on a domain name, you generate a DNS query that goes to the DNS resolver. If your DNS services provider uses a DNS filter the resolver will check a block or allowlist before solving any DNS queries.
Blocklist filtering
You can configure the DNS resolver to block:
- domains known to host malicious content
- suspicious domain names
- domains with inappropriate content
- domains that employees should not visit during working hours
The resolver will block the DNS query if the requested domain is in any of these categories. You won’t be able to access the malicious site. No credentials stealing, malware downloading in the background, or harm done.
Allowlist filtering
If you choose using an allowlist, the user will only get access to a preapproved list of websites. None of the websites, malicious or not, that are not on that list will be accessible to the user. This is a more restrictive filtering policy than the one based on a blocklist.
DNS filtering has a fast response time, so accessing safe websites that adhere to the company’s authorized Internet usage standards will be almost instantaneous.
The problem with malicious domain lists is that hackers know about them. So, they use Domain Generation Algorithms (DGAs) to avoid blocking. This means they use special software to generate thousands of fresh domain names that usual DNS filtering engines will not detect as malicious.
Heimdal’s DNS Security Module goes one step further in addressing this issue. Its two-ways DNS filtering engine uses predictive DNS technology. This is an AI & ML algorithm that can tell with 96% accuracy if a domain is malicious before anyone else reports it.
Being able to recognize in time an unreported malicious domain adds an extra protection layer to your defense.
If you’re not using a DNS filter, you can implement this kind of restriction at the router level through the Internet Service Provider (ISP). The client – say, a company – would redirect their DNS to the ISP. As a result, access to websites on this ISP’s blacklist will be restricted.
Additionally, the ISP can also help restrict access to specific categories of sites, such as pornography, file-sharing portals, gambling, and online gaming sites.
For that, your company should develop an acceptable usage policy (AUP) and integrate it with the ISP.
Common DNS filters
Depending on your company’s access needs, there are various filtering patterns you can include in your DNS filtering policy:
Category filters
Category filters allow administrators to block access according to the nature of the website. Like social media platforms, torrent websites that are already marked as illegal, etc.
Keyword filters
Content filtering uses keywords to block access to websites or web applications. Keyword filters work by identifying specific words found in the websites’ content: racial hatred, pornography, gambling, etc.
URL filters
A website is blocked or allowed depending on its URL.
Application filters
This filter blocks access to apps that have a high risk of being malicious, like streaming services or peer-to-peer sharing
DNS filtering benefits
DNS filtering reduces the risk of cyberattacks conducted through visiting a malicious domain. While it’s not a stand-alone security solution, it is a first layer of defense for both endpoints and networks. DNS filtering can help you prevent malware, ransomware, and phishing attacks.
Detecting and stopping cyber threats at DNS traffic level helps increase productivity, reduces HR issues and ensures a safer browsing experience.
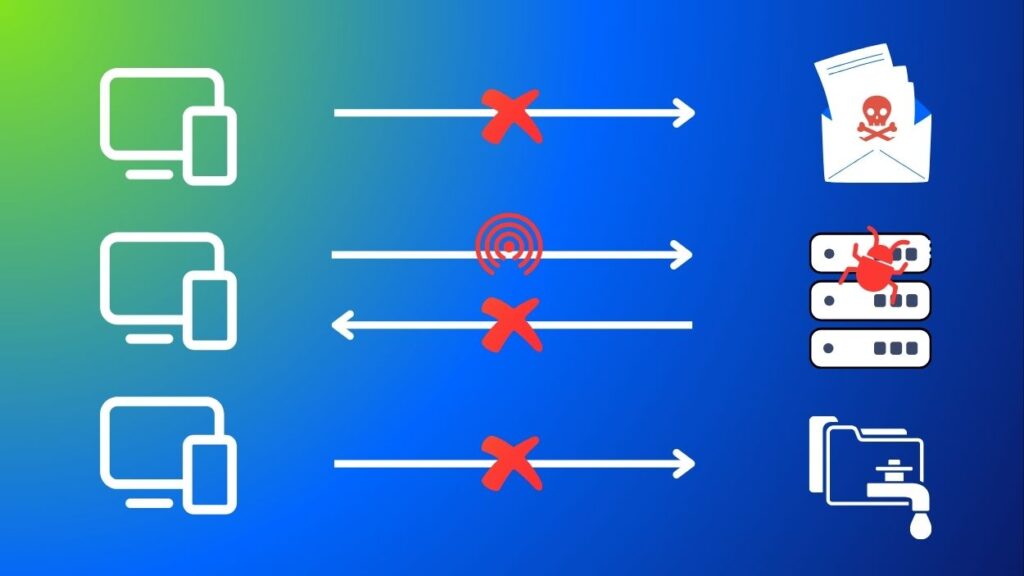
Here are some of the benefits of using a DNS filtering tool:
Blocks Malvertising
The internet abounds in malicious ads trying to convince users to download forged software, or access malicious sites. Yes, getting Adobe Illustrator for free or at half the price may sound tempting, but you’ll probably end up installing malware on your computer.
The simple act of clicking on a tempting ad may trigger a drive-by download. This means that as soon as the webpage opens, it instantaneously downloads malware on your device.
DNS filtering can stop these kinds of intrusions by spotting and blocking in time a malicious domain.
Prevents phishing attacks
Phishing attacks are in the top three initial access methods that hackers use, according to the 2024 Data Breach Investigation Report conducted by Verizon:
The three primary ways in which attackers access an organization are stolen credentials, phishing and exploitation of vulnerabilities.
Experience showed that even the most educated, cybersecurity-aware employees can fall victim to phishing emails.
Yes, you should still train people to identify phishing emails and social engineering attempts. But people make mistakes. This is why DNS filtering does a better job than security training at preventing phishing attacks.
A phishing website is a phony website created for the purpose of phishing attacks to collect user credentials. The domain name often spoofs the legitimate one, so that most users won’t seize the difference. The objective of phishing attacks is to trick the user into providing their login details to a forged site that hackers control.
A professional DNS filtering system can recognize illegitimate IP addresses and domains. Blocking communication with reported malicious websites that were uploaded on the blocklist is an important prevention measure. It’s not perfect, but it does reduce risks.
The best choice is to use a DNS filtering tool that can recognize a malicious domain that is not yet on any blocklist.
Prevents ransomware attacks
DNS filtering prevents ransomware attacks in two ways. First, it blocks communication to a malicious website that might attempt downloading ransomware on a device. Second, if a computer is already infected, it blocks communication with the Command-and-Control Server.
This means that hackers will not be able to:
- beacon to the C2 server that they infiltrated the network
- install additional, encryption malware
Prevents data breaches
DNS filtering prevents data breaches by blocking communication with the C2 server. Thus, the attacker will not be able to exfiltrate any data.
What are the risks of not using DNS filtering
There are various types of DNS-related attacks that can lead to money, reputation and time losses.
Here are some of the most common risks of not protecting your infrastructure at DNS level:
Subdomain attacks
Attackers could try to overload authoritative name servers with queries for inexistent subdomains (111aaa.example.com instead of example.com, for instance), consuming its resources and causing disruption to legitimate queries.
Cache poisoning
Cache poisoning attacks aim to corrupt the resolver servers. They try to manipulate the answers the resolver stores in its cache. If they succeed, any subsequent query will get the corrupted answer.
Phantom domain
Phantom Domain attacks also involve authoritative servers and imply asking for non-existent recursive name servers. This wastes the DNS server’s time and fills up the cache with useless answers.
Ransomware attacks
Hackers need to maintain communication to make a profit. One way of obtaining it is through DNS. Ransomware uses DNS to communicate with the command-and-control server, but also to update itself, like the famous WannaCry ransomware.
Hijacking and redirection
In this type of attack, the hackers divert DNS traffic to websites they control. The unsuspecting users will end up on malicious sites.
Data exfiltration
To exfiltrate data, hackers can use DNS tunneling. This technique involves encoding messages in DNS queries and answers to avoid detection. DNS filtering prevents data exfiltration by preventing the DNS server from communicating with malicious sites.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How can Heimdal® help?
One of the four levels of security the Heimdal® products are built on is prevention. In order to help you achieve unique threat prevention, we propose two main modules: Heimdal® DNS Security Network and/or Heimdal® DNS Security Endpoint.
DNS Security Network is a powerful Intrusion Prevention System that protects your organization’s network at the perimeter level. It prevents, detects, and blocks ATPs, ransomware, data leaks, and network malware.
Also, it automatically blocks command and control server connections, logs network traffic, checks activities, and tracks the history of threats that were unknown. Depending on your company’s needs, the filtering solution offers the possibility to use custom block pages and to allow/blocklist.
DNS Security Network is made of two Heimdal trademarked engines:
- DarkLayer Guard™ which offers full DNS protection, as well as active and passive modes and full network logging
- VectorN Detection™ uses Neural Network Transformed AI for tracking device-to-infrastructure communication to spot and stop attacks that firewalls cannot see.
Wrapping up
DNS protection is the first line of defense for networks that communicate online. Using the internet, which is vital nowadays for any company, relies on using the Domain Name System.
A professional DNS filtering solution is your best chance to protect your business against up to more than 90% of the existing cyber threats.
Whatever you choose, you should remember that Heimdal® always has your back and that our team is here to help you protect your company.
If you liked this article, make sure you follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security