Contents:
Defense in depth layers come in many shapes and sizes. This might become confusing for someone who is new to the concept, so please allow me to explain what they are and how they work. In my previous article on defense in depth cybersecurity, I went over its basic notions. To briefly recap, defense in depth is an information security approach that involves placing a series of controls and protocols throughout the network to create redundancy in the case of one system failing. It was based on an eponymous ancient military strategy that implied slowing down an attack with various lines of defense instead of focusing resources on one large formation. Another thing I briefly touched on in that post was the fact that defense in depth is a layered cybersecurity architecture. In this article, I will focus solely on the concept of defense in depth layers from this point on. So, let’s get into it.
Types of Defense in Depth Layers
Defense in depth layers can be classified by two separate sorting systems that sometimes intersect in terms of components. The two resulting categories are that of control layers and that of cybersecurity layers respectively.
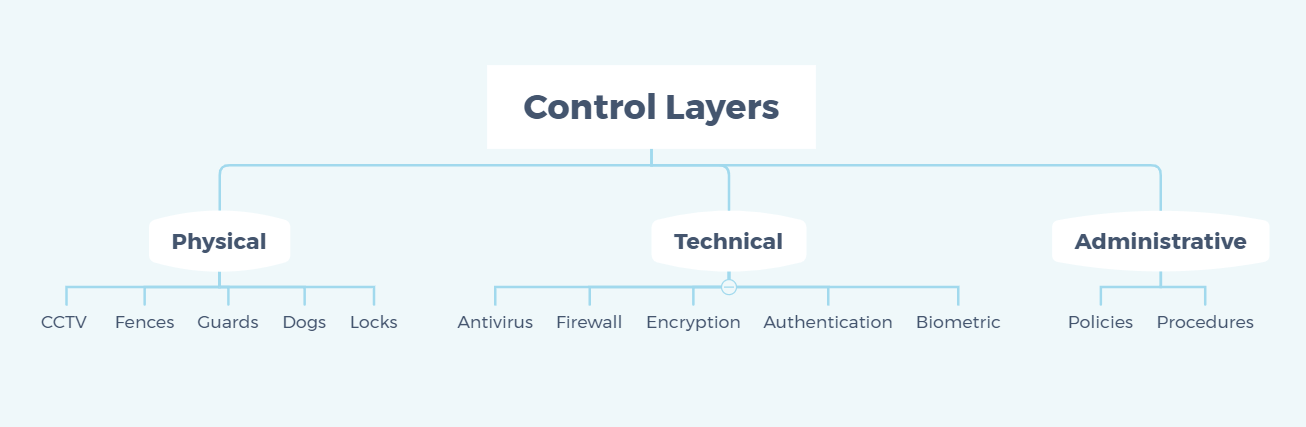
Control Layers
Defense in depth can be divided into three control layers according to the point of focus. These are physical controls, technical controls, and administrative controls. Let’s have a more detailed look at each one before moving on to the next subcategory.
Physical Controls
As the name suggests, physical controls are defense in depth layers that prevent physical access into an organization’s IT network. These are traditional fortifications that can be used for anything from home protection to military-grade security. They are not cybersecurity-exclusive. Examples include, but are not limited to:
- CCTV systems,
- reinforced fences,
- security guards,
- guard dogs,
- and locked doors.
Technical Controls
Technical controls are software and hardware components meant to protect an enterprise’s system and data resources. They differ from physical controls in the sense that they protect the contents of a system rather than the physical system itself. Some instances of technical controls applied to an organization consist of:
- antivirus software,
- software or hardware firewall,
- disk encryption,
- authentication controls,
- and biometric scanning.
Administrative Controls
Finally, the notion of administrative controls refers to an organization’s IT network security policies and procedures. The intention behind this category of defense in depth layers is to provide proper cybersecurity guidance, as well as to ensure that regulations are respected within a company. The list for this subtype contains:
- security requirements,
- data handling procedures,
- hiring practices,
- digital code of conduct,
- and confidentiality policies.
Cybersecurity Layers
The subcategory of cybersecurity layers consists of defense in depth layers that focus solely on the cybersecurity aspect, intersecting with the subcategory of technical controls within the larger control layer infrastructure.
Data Protection
Data protection is an example of defense in depth layers of cybersecurity. Its purpose, as the name implies, is to guard the integrity of information resources within a company network. Some processes pertaining to it that you can include in your strategy are data hashing, encryption at rest, and encrypted backups. Data hashing refers to the practice of transforming a string of characters into a shorter key with a fixed length. In fact, the hashes that result from this process are usually the same length regardless of how rich the initial information you feed into it is. Its most common use within a corporate computing environment is in the case of passwords, but it can be used as a cipher for various other bits of data. Next, encryption at rest deals with the protection of data at rest, which entails information or content that is stored locally on the devices in a network. By encrypting such files with a strong RSA or AES algorithm, you are ensuring that someone gaining unlawful entry into company systems won’t be able to read what is stored on them. Encrypted backups function after more or less the same premise, with the exception that they target data that is stored externally, either offline on adjacent devices or online in the cloud.
Access Measures
An essential part of the defense in depth layers infrastructure is the segment of access measures. These are procedures put into place through either policies or software that regulate who enters your company network and to what extent. Essential components include virtual private networks, authentication controls, biometric scanning, and privileged access management. A virtual private network, or VPN for short, routes traffic through an encrypted virtual tunnel, hiding a user’s IP address in the process. It acts as a barrier between the device and the Internet at large, protecting against external cyberattacks. The business version of a VPN secures your employees’ computers regardless of where they are connecting to the company network. Authentication controls handle how members of staff and other enterprise users confirm their identity when logging into the network. Requirements may include a token, a password, a PIN code, a public/private key, or biometric scanning. The latter refers to verification procedures that involve a bodily part, such as fingerprint, retina, or facial features. Using two or more of these methods in tandem creates a multi-factor authentication architecture. Finally, privileged access management enforces the principle of least privilege within a company, through which users in a network have the minimum access rights they need only. It is a way to securely manage privileged accounts that have access to critical and confidential resources within your enterprise. This type of accounts is prime real estate for cyberattackers, which is why I recommend enforcing PAM with the help of a solution such as our Heimdal™ Privileged Access Management. Heimdal® Privileged Access
Management
System Monitoring
The practice of system monitoring consists of examining your company network to detect security gaps and prevent attacks. Processes in this category include vulnerability management, as well as both network logging and network auditing. Vulnerability management entails both scanning for security gaps that can be potential entry points for hackers, as well as closing these gateways. The latter is achieved by installing software updates and patches as soon as they are deployed by their respective third-party developers. The easiest way to solve this issue is with an automated software updater. Network logging and auditing is a two-part process that involves keeping records of events that occur in a system, then reviewing them to discover security gaps and other issues. It is carried out with the help of a network log that contains information on users, processes, access requests, errors, and so on. These are then analyzed during an audit.
Endpoint Protection
Endpoint protection deals with defense in depth layers that apply to an organization’s workstations. These can be located on the company perimeter or outside it. Thus, these measures are designed to be equally efficient regardless of where in the world an employee is connecting from. The main software types in this subcategory are represented by antivirus, email protection, and DNS filtering. First things first, antivirus software is a form of endpoint protection that has been around since the 1980s, when the first computer viruses appeared in the wild. Over the years, AV has evolved to be efficient against various forms of malware, such as Trojans, worms, or exploits. However, traditional antivirus still can’t beat advanced threats like polymorphic malware. This is where next-generation antivirus (NGAV) comes in. A cutting-edge cybersecurity solution, NGAV adds sandboxing, as well as behavioral and backdoor analysis to the outdated code-based detection of regular AV software. What is more, it usually comes with an inbuilt firewall, which monitors traffic and blocks malicious entry attempts following a predetermined set of requirements. But more on that in the following (and final) section of the article. DNS filtering consists of monitoring incoming and outgoing traffic at the level of the Domain Name System, taking endpoint protection one step further. Implementing it as one of your defense in depth layers means that you will be able to not only detect threats but also actively hunt and prevent them. You can easily apply DNS filtering on company devices regardless of their location with our Heimdal™ Threat Prevention for Endpoints. Heimdal® DNS Security Solution
Network Protection
Network protection deals with the online network perimeter of an enterprise. What you need to consider in this respect is first of all the firewall, then enhance its traffic filtering capabilities with an intrusion prevention and detection system. A firewall is a classic network security tool that acts as a barrier between incoming and outgoing queries and the Internet at large. As previously mentioned, it functions according to a predefined set of rules that allow it to identify known threats and block infiltration attempts. However, it can only act against threats that are known. This is where the intrusion prevention and detection system swoops in to boost your company’s defenses. By taking query filtering at the level at the DNS, an IPDS such as our Heimdal™ Threat Prevention for Networks logs all traffic and spots hidden threats through the power of artificial intelligence. In this way, your network will be guarded against previously unknown threats and infamous ones alike.
Wrapping Up…
Defense in depth layers can be categorized in two main ways. But regardless of what you prefer calling them, their strength is in numbers. To successfully implement this cybersecurity approach within your enterprise, you will need to implement at least two of the aforementioned components, although I recommend aiming for a lot more than that. A holistic suite of solutions that creates an adequate balance between physical, technical, and administrative, as well as between network and endpoints is the best way to go.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









