Contents:
Riddle me this: what bears the name of a famous English, tights-wearing rogue but keeps the spoils instead of handing them out to the downtrodden? No, it’s not Robin Hood’s evil twin, but a new type of ransomware that’s slowly rising through the malware ranks.
This novel and audacious malicious agent is called the RobbinHood Ransomware (i.e. no, it’s not a typo) and, so far, it has managed to rake up something of a small treasure after hitting three North American cities. Today’s article is dedicated to this nascent ransomware. I’ll be covering methods of dissemination, infection mechanisms, occurrences, and countermeasures. Enjoy and stay safe out there!
What is the RobbinHood Ransomware?
The RobbinHood Ransomware belongs to the same family as Emotet, IceID, Mailto, Maze, REvil, Trickbot, and MedusaLocker. First spotted in the wild in 2019, RobbinHood has quickly managed to make a name for itself by compromising multiple networks from Maryland, Greenville, and Baltimore. The authorities estimated that the creators of RobbinHood managed to extort at least $1.5 million from their victims. Quite a performance, considering its relatively short time span.
As far as the name’s concerned, RobbinHood has nothing in common with the English crusader turned outlaw other than robbing the rich. This ransomware has been observed to earmark HVTs such as large companies or institutions. Unlike the dashing, bow-bearing rogue, the creators of this ransomware don’t hand out the spoils to the poor. They just keep them for themselves.
Since the RobbinHood ransomware only attacks high-value targets, the ransom is calculated accordingly. One estimate shows that the victims are asked to pay anywhere between 3 and 13 BTC. The prices are computed depending on the number of affected endpoints. For instance, the victims may be asked to pay 3 BTC ($40,538) for a single infected machine and up to 13 BTC ($176,000) for a network.
Apart from demanding a hefty ransom from its victims, the RobbinHood ransomware is also notorious for its sarcastic ad-libs. For instance, the variant that affected Greenville and Baltimore City included a seemingly honest piece of advice: “just pay the ransomware and end the suffering then get better cybersecurity.” Great advice, but at what cost?
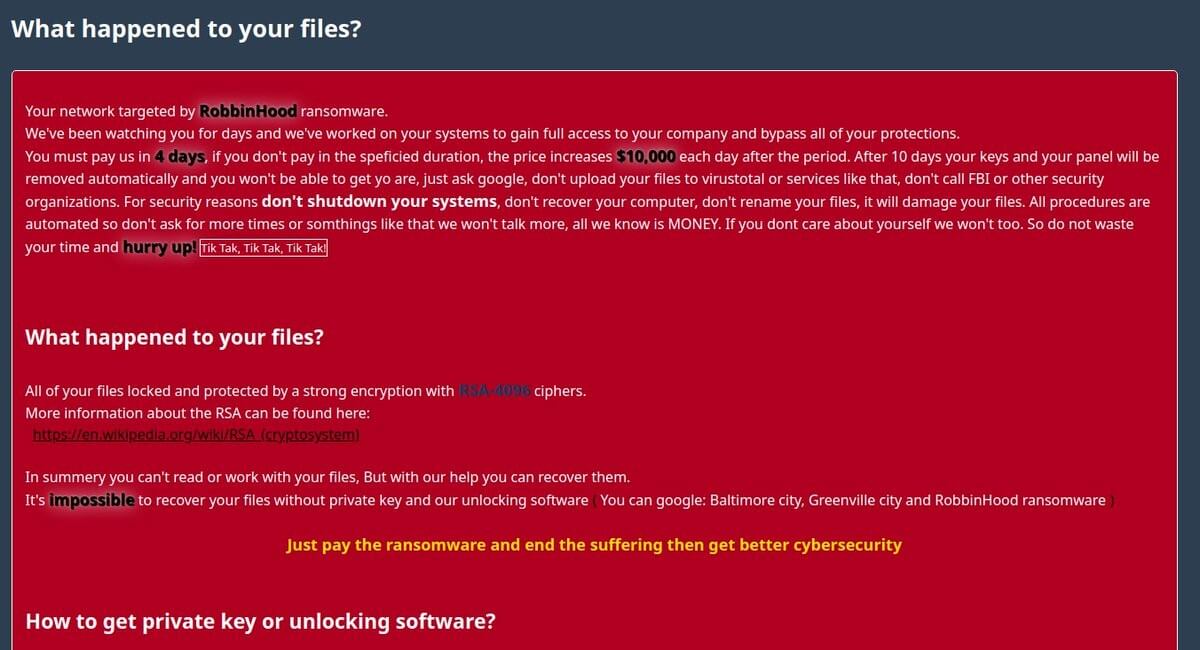
Naturally, one would ask what would ensue if the victim decides not to pay the ransom? As mentioned in the attached screenshot, the data would be forever lost and, on top of that, the ransom bumps up against another $10,000 with each passing day.
Courtesy of MalwareBytes Lab
RobbinHood ransomware’s implications are not limited to locking sensitive files. I’ll tackle this in the next section.
Breakdown of RobbinHood Ransomware – Attack patterns, infiltration, and obfuscation techniques
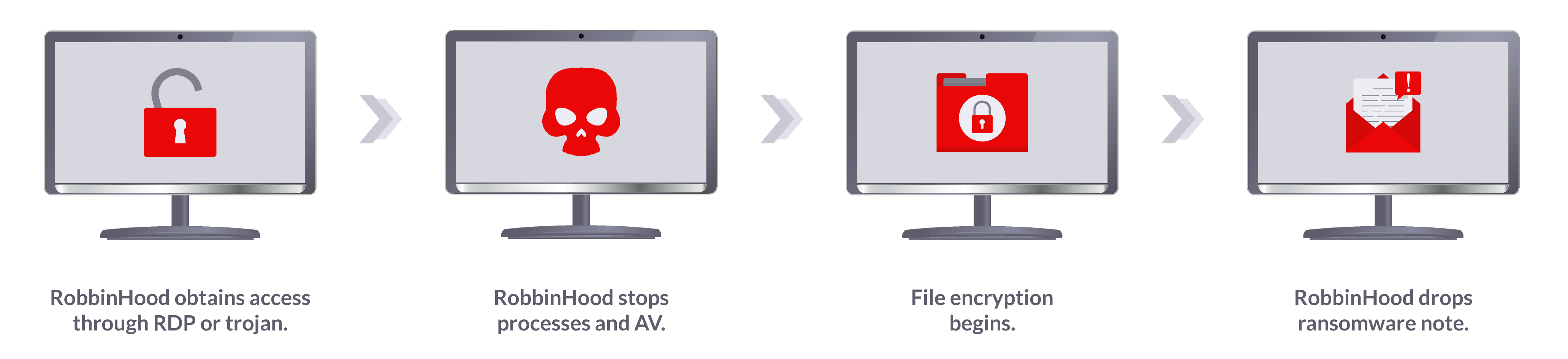
So far, this ransomware variant has lived up to its name by targeting large companies or institutions. It has been observed that RobbinHood’s favorite infiltration vector is the RDP port. The black-hat hackers usually gain access to the network by brute-force attacking the Remote Desktop Protocol port. In other cases, the ransomware used trojans in order to achieve the same goal. Curiously enough, Heimdal™ Security along with many cybersecurity experts have detected a surge in brute-force attacks, the most recent one taking place mid-October. No correlation has been established between the increase in brute-force attacks and RobbinHood ransomware.
After gaining access to the machine or network, the ransomware will attempt to gain enough traction to compromise key systems. Although highly disputed, it would seem that in Baltimore, Maryland, and Greenville, the ransomware prompted the affected systems to rubberstamp the installation of the kernel driver from the Taiwanese computer hardware manufacturer Gigabyte. The driver in question is Gdrv.sys, a low-level driver that executes Gigabyte Tools.
CVE Detail’s entry on the vulnerability earmarked CVE-2018-1932 shows that the kernel driver has been used in other graphics-related applications such as AORUS Graphics Engine (version 1.57 and earlier), OC Guru II (version 2.08), and XTREME GAMING ENGINE (version 1.26 and earlier).
Digital forensics shows that a vulnerability in the driver’s code can be used to trigger a ring0-memcpy functionality. The aforementioned functionality is employed in the Driver Signing Enforcement process. It’s only natural for RobbinHood’s creators to take advantage of this flaw because tampering with the DSE is the easiest way (well, not that easy) to abscond from any malware.
To summarize:
RobbinHood gains access through trojans or by brute-forcing the RPD port. Full system compromise is achieved by auto-installing a flawed (and digitally signed) Gigabyte motherboard driver. Since the device is signed by the vendor, it will not ask for the user’s approval. Once the ‘Gaining Access’ phase is complete, the ransomware will move in to remove or disable key-processes through the Gdrv.sys vulnerability. To avoid detection and take full control of the system, RobbinHood temporarily suspends and/or disables 181 system services. Furthermore, some behavioral analyses reveal that this ransomware strain also removes backup programs (if present) and disables AVs or antimalware software.
Morphology and behavior
The RobbinHood Ransomware has one module that consists of several embedded files. STEEL.EXE is the so-called kill application or the primary attack module. Its role is to disable or remove protective and non-protective system services by taking advantage of kernel drivers’ vulnerabilities. The files embedded into STEEL.EXE are as follows:
PLIST.TXTRBLN.SYSGDRV.SYSROBNR.EXE
The Steel executable is the kill application. Its task is to disable the processes and files associated with cybersecurity products (i.e. antivirus, antimalware). Moreover, STEEL.exe also is in charge of deploying ROBNR.EXE which further unpacks the unsigned vulnerable Gigabyte driver.
We should also note the fact that ROBNR.EXE also drops legit (and signed) third-party drivers in addition to the unsigned one, thus increasing its obfuscation factor. As stated above, GDRV.SYS is the vulnerable driver that allows STEEL.EXE and the embedded malicious kernel driver RBNL.SYS to disable system processes and delete files from the so-called kernel space.
PLIST.TXT*, the last component of STEEL.EXE (i.e. not embedded in the Steel executable; rather an addition to Steel, a text file that contains a long-winded list of all the applications RBNL.SYS will disable.
To summarize:
STEEL.EXE kills AVs and antimalware solutions, ROBNR.EXE deploys malicious kernel driver and signed third-party drivers, GDRV.SYS is deprecated, but digitally-signed motherboard driver used to assert control over the victim, RBNL.SYS is the malicious, kernel-space driver that’s capable of deleting system-locked files and kill processes. PLIST.TXT, while not included in STEEL.EXE, is a hit list containing the apps that will be disabled.
To disable vital system process, the malware will upload the following Command Prompt sequences: /c se.exe stop KAVFS, /c sc.exe stop RESvc, /c sc.exe stop SamSs, /c sc.exe stop W3Svc, /c sc.exe stop bedbg, /c sc.exe stop masvc, and /c net use* /DELETE /Y. The last command disconnects the machine from every network.
*List of services disabled by RobbinHood. Redacted for brevity.
Filter SSQL$SBSMONITORING,SQLWriter.Protection RESvc.TrueKey.System UI0Detect.SAVAdminService.SmcService.MsDtsServer100.VeeamBackupSvc.TrueKeyScheduler.POP3Svc.McTaskManager.ShMonitor.AVP.WRSVC.NetMsmActivator.DCAgent.MSExchangeIS. etc.
All of RobbinHood’s files are extracted and stored in the Windows Temp file. Apart from Steel and its malicious modules, the ransomware also offloads the files rf_l, rf_s, ro_l, and ro_s. The additional files were found to contain logs of all the files encrypted on the victim’s machine.
File encryption
After the protection and vital system services are stopped, RobbinHood will shortly begin the encryption process. However, research shows that before the encryption process can begin, the ransomware must first disable Windows’ auto-repair process. Also, RobbinHood deactivates networking sharing, deletes volume snapshot service records (i.e. shadow copies), and clears all event logs.
Now the encryption process can begin. It has been noted that RobbinHood operates a two-factored encryption process. First, the RobbinHood ransomware will encrypt each file using a custom-created AES key. The public key for this first encryption stage is taken from pub.key, a file located in the victim’s Temp folder. After that, both the original filename and the newly-created AES key will be encrypted to win a public RSA key (i.e. RSA-4096), which will later be added to the crypted file. After the encryption process is done, the malware will begin rewriting the extensions to match this format: enc_robbinhood.
Another curiosity of the RobbinHood Ransomware: ridiculing the victim after the encryption is done. In most cases, the console output function is disabled. This means that the encryption is done quietly, in the background. In remote cases, the ransomware creators would enable this function just to toy around with the victim. After the files are encrypted, a console screen would be displayed. The message reads: “[+] Done, Enjoy buddy 😊)))”
Post-file encryption and ransoming notes
After the file encryption stage is completed, RobbinHood will create four separate ransom note versions in the same folders that hold the altered files. The first half of the note is unique to each case. For instance, in this particular case, the attackers dropped the following note:
“Your network targeted (sic) by RobbinHood Ransomware”. We’ve been watching you for days and we’ve worked on your systems to gain full access to your company and bypass all of your protections. You must pay us in 4 days, if you don’t pay in the speficied (sic) duration, the increases $10,000 each day after the period. After 10 days your keys and your panel will be removed automatically and you won’t be able to get yo are (! sic), just ask google, don’t upload your files to virustotal or services like that, don’t call FBI or other security organizations. For security reasons don’t shutdown your system, don’t recover your computer, don’t rename your files, it will damage your files. All procedures are automated so don’t ask for more times (sic) or somthings (sic) like that we won’t talk more, all we know is MONEY. If you dont (sic) care about yourself we won’t too. So do not waste your time and hurry up! Tik Tak, Tik Tak, Tik Tak!”
The rest of ransom note is redacted below. Bear in mind that this is the part that remains (mostly) unchanged. For anonymity preservation reasons, the attackers will change the Bitcoin collection addresses and the onion link(s) to the attacker’s panel.
What happened to your files? All your files are encrypted with RSA-4096, Read more on https://en.wikipedia.org/wiki/RSA_(cryptosystem) RSA is an algorithm used by modern computers to encrypt and decrypt the data. RSA is an asymmetric cryptographic algorithm. Asymmetric means that there are two different keys. This is also called public key cryptography because one of the keys can be given to anyone: 1 – We encrypted your files with our “Public key” 2 – You can decrypt, the encrypted files with a specific “Private key” and your private key is in our hands (It’s not possible to recover your files without our private key) Is it possible to get back your data? Yes, We (sic) have a decrypter (sic) with all your private keys. We have two options to get all your data back. Follow the instructions to get all your data back: Option 1 Step 1: You must send us 3 Bitcoin(s) for each affected system Step 2: Inform us in panel with hostname(s) of the system you want, wait for confirmation and get your decrypter (sic) Option 2 Step 1: You must send us 13 Bitcoin(s) for all affected system Step 2: Inform us in the, wait for confirmation and get all your decrypters (sic) Our Bitcoin address is: <redacted> BE CAREFUL, THE COST OF YOUR PAYMENT INCREASES $10,000 EACH DAY AFTER THE FOURTH DAY Access to the panel (Contact us) The panel address: <redacted> Alternative addresses: <redacted> Access to the panel using Tor Browser In non (sic) of our links are accessible you can try tor browser to get in touch with us: Step 1: Download Tor Browser from here: https://www.torproject.org/download/download.html.en Step 2: Run Tor Browser and wait to connect Step 3: Visit our website at panel address If you’re having a problem with Tor Browser, Ask Google: how to use tor browser Wants (sic) to mare sure we have your decrypter? To make sure we have your decrypter you can upload at most 3 files (maximum size allowance is 10 MB in total) and get your data back as a demo. Where to buy Bitcoin? The easiest way is LocalBitcoins, but you can find more websites to buy bitcoin using Google Search: buy bitcoin online.
Step-by-step infection process
Protecting Your Infrastructure against the RobbinHood Ransomware
Removing ransomware has always been problematic, but more so with RobbinHood. Given the number of interactions with critical system processes, even if the victim decides to pay the ransom – which we do not recommend – the affected machines may experience long-lasting issues. One of the many reasons why Gigabyte decided to retire the motherboard driver is due to users complaining about BSODS, especially on machines running Windows 10.
By injecting the malicious kernel driver, the creators of RobbinHood ransomware can severely impair the machine long its removal. This issue can be fixed by manually uninstalling the defective driver. To do so, hit the Windows key on your keyboard, type in “Add or Remove Programs”, and scroll down until you see Gigabyte Tools. Highlight the app, press the “Uninstall” button, and follow the on-screen instructions. To ensure that all of the app’s files – including the defective driver- are removed from your machine, you can use utilities like Easy Tune, CCleaner, or AVG Tuneup.
Please take note that this removal method may effective up to a certain extent. The malicious kernel driver can be ‘locked out’ and inaccessible to the user even when running on admin rights. In this case, the solution would be restoring the machine from an image or a restore point. One more reason why you should backup your data on a regular basis.
This advice is applicable after the malware itself has been removed from the affected machine. Doing so in advance won’t protect your endpoint from the RobbinHood ransomware, except for the backup part.
As always, prevention is the best cure. Here’s how you can protect your machine and network from ransomware.
1. RDP port
Observations have revealed that the most common entryway used by RobbinHood is the RDP port (3389). Blocking the Remote Desktop Protocol port is one way of ensuring that the ransomware does not infiltrate your endpoint. If you’re not running a corporate cybersecurity solution, you can manually restrict/block the access to the RDP port from Windows Firewall. To do so, hit the Windows key and type in “Windows Firewall”. In the Windows Firewall menu, click on “Advanced settings”. You need administrator rights to commit these changes.
In the “Windows Firewall with Advanced Security”, click on Inbound Rules. In the right panel, under “Actions”, click on “New Rule”. The New Inbound Rule Wizard will be launched. Select “Port” and click “Next”. Chose TCP as inbound rule port selection.
Click on the checkmark next to the “Specific local ports” setting. Type in “139, 445, 3389”. Click “Next” when ready. Select “Block the connection” and click “Next”. In the following screen, ensure that all options are selected. Click “Next”, name your Inbound Rule, and provide a description if necessary. When you’re done, click Finish to enforce the new firewall rule.
For the purpose of security, I would strongly recommend a solution that blocks these ports by default. Heimdal™ Next-Gen Antivirus & MDM (as part of the Endpoint Security Suite) has a built-in module specifically designed to detect and avert brute-force attacks and other types of aggression directed at this port. We have fine-tuned the module to differentiate between user interactions (i.e. user typing in the incorrect password too many times) and brute-force attempts.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
2. Enforce Two-factor authentication
Decrease the probability of unauthorized attempts by enforcing 2FA whenever possible. The best practice in this case would be an account tied to a smartphone application like Google Authenticator or Authy.
3. Frequent backups and restore points
Ensure that all your data, regardless of importance, is back up to the cloud. There is plenty of software that can help you streamline (and automate) this process. At the endpoint-level, it’s advisable to create restore points. If you don’t have an app that automatically manages this task, you can use Windows’ System Protection feature.
To create a restore point, hit the Windows key and type in “Create a restore point”. Under System Protection, select the drive you want to create a restore point for, and hit the configure button. In the next screen, highlight the Turn on system protection feature, adjust the disk usage slide, click Apply, name your restore point, and click Apply.
4. Cover alternative attack vectors
As mentioned, brute-force attacking the RDP port is just one way of gaining access to a machine or the network. The RobbinHood ransomware also spreads through trojans. Email attachments are notorious for harbouring macro viruses, worms, and trojans. Before opening any email attachment, please ensure that the email comes from a verifiable source.
Check for any inconsistencies in the email’s header, subject line, and body. Emails containing malicious attachments are usually laden with spelling errors. Email protection technologies have been developed and fine-tuned to detect and deal with this type of threat.
Heimdal™ Security’s Heimdal™ Email Fraud Prevention uses the deep attachment scan technology to flag and remediate mail-delivered malware such as phishing, spear-phishing, trojans, macro viruses, business email compromise, and more.

Heimdal® Email Security
- Completely secure your infrastructure against email-delivered threats;
- Deep content scanning for malicious attachments and links;
- Block Phishing and man-in-the-email attacks;
- Complete email-based reporting for compliance & auditing requirements;
Conclusion
The US cases highlighted in the ransom note are only the beginning. RobbinHood may not have the same notoriety as Netwalker or Zeus, but it’s slowly gaining strength. Heimdal™ Security’s advice is to refrain yourself to pay the ransom if your company should come under attack because there’s no guarantee that you’ll get your data back. The creators of this ransomware strain do have a point: if you don’t want to pay, get better protection. How would rate your company’s cybersecurity posture? Do you have the means to protect your endpoints against ransomware? Plan ahead, stay frosty and refrain from clicking on spammy links.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security