Contents:
Choosing the right cybersecurity solution is crucial for protecting your business, and when comparing Crowdstrike vs Sophos, it’s essential to evaluate their offerings carefully.
In this article, we’ll focus on two prominent solutions: Falcon by CrowdStrike and Intercept X by Sophos.
We’ll analyze the strengths and weaknesses of each solution, providing you with valuable insights to make an informed decision.
Additionally, we’ll explore an alternative option, providing you with a comprehensive perspective.
Let’s dive in!
Introduction to CrowdStrike and Sophos
What Is CrowdStrike Falcon?
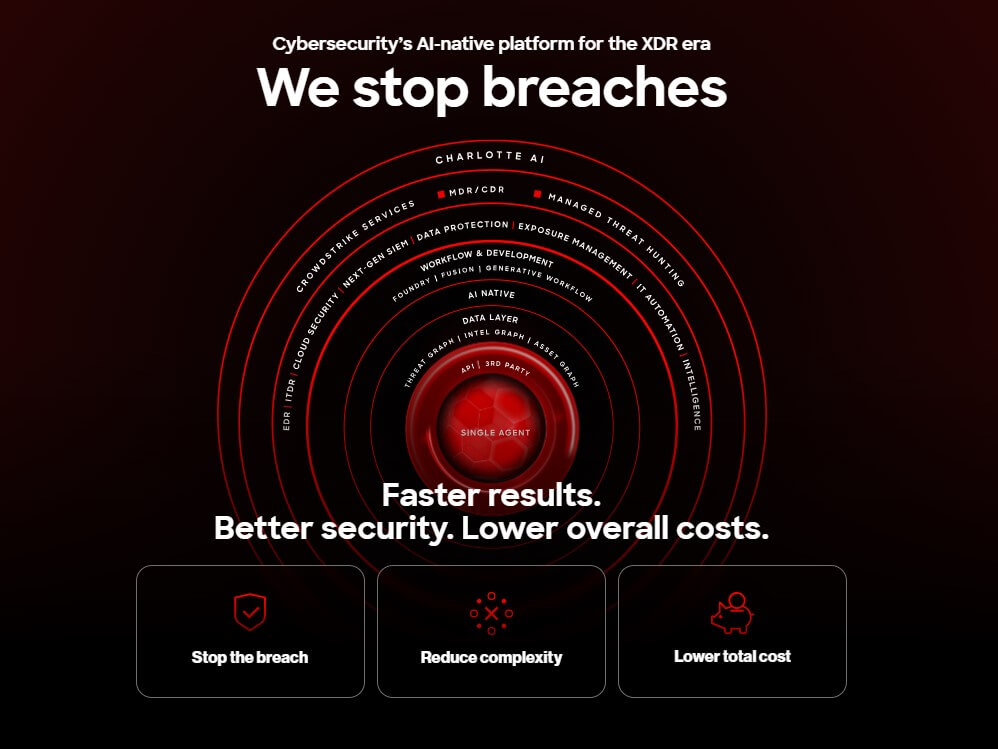
CrowdStrike Falcon is a cloud-based cybersecurity platform designed to prevent a wide range of attacks, including malware and beyond.
It offers next-generation antivirus, endpoint detection and response, threat intelligence, managed threat hunting, and security hygiene capabilities—all in a single lightweight sensor managed through the cloud.
It’s a comprehensive solution that aims to stop breaches by addressing modern threats such as exploits, zero days, and credential theft.
What is Sophos Intercept X?

Sophos Intercept X is an enterprise-level endpoint protection solution that proactively monitors for malware and exploits to block and remove threats from networks.
It offers powerful XDR capabilities for IT operations and threat hunting, enabling quick identification and remediation of potential issues.
Additionally, Sophos provides Managed Detection and Response (MDR) services with two tiers (Standard and Advanced) for organizations of all sizes and maturity levels.
CrowdStrike vs Sophos: Core Features
CrowdStrike Falcon
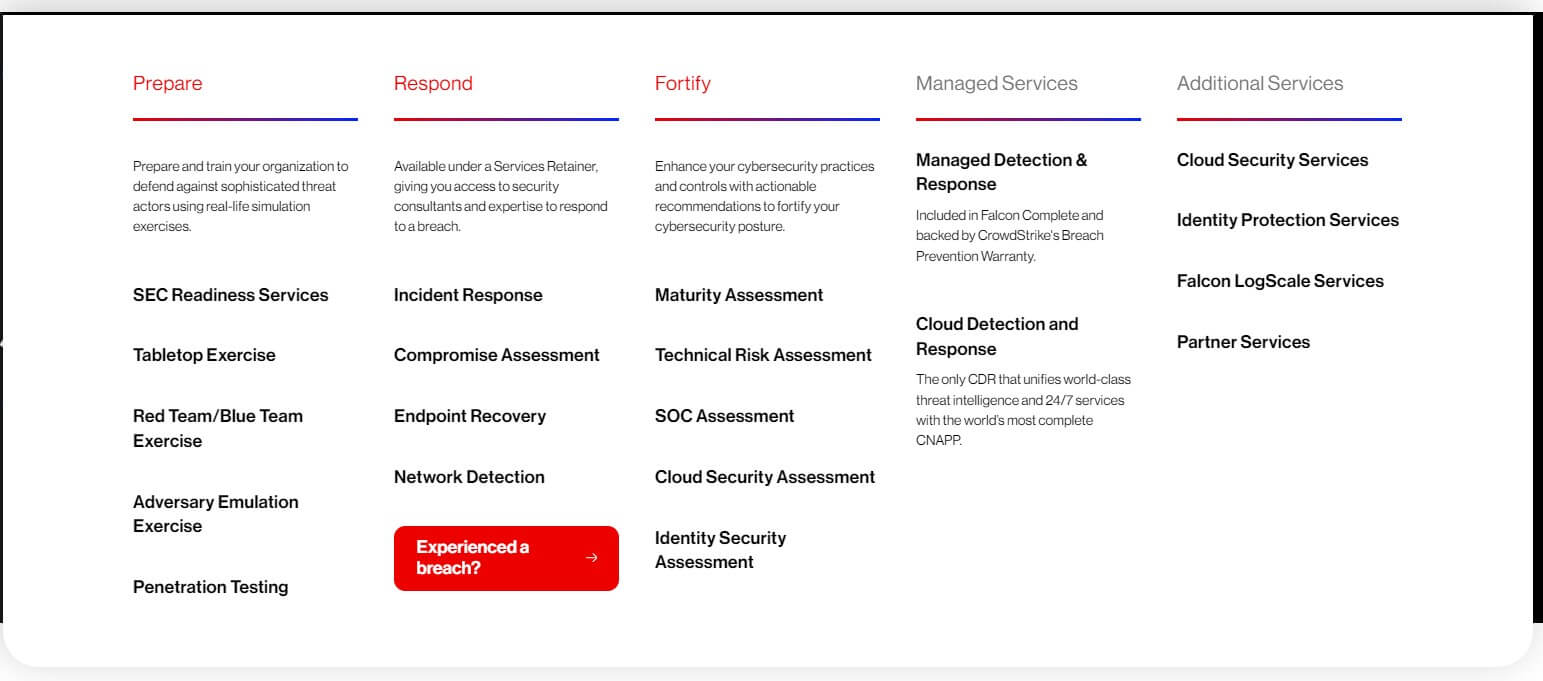
Here’s an overview of its key components:
- Falcon Prevent: Next Generation Antivirus (NGAV) for proactive threat prevention.
- Falcon Insight: Endpoint Detection and Response (EDR) for continuous monitoring and response.
- Falcon Device Control: USB Device Control to manage and control USB devices.
- Falcon Firewall Management: Host Firewall Control for firewall management.
- Falcon For Mobile: Mobile Endpoint Detection and Response for securing mobile devices.
- Falcon Forensics: Forensic Data Analysis for in-depth investigation and analysis of security incidents.
- Falcon OverWatch: Managed Threat Hunting for proactive threat detection and response.
- Falcon Discover: Security Hygiene for maintaining good security practices and hygiene.
- Falcon Spotlight: Vulnerability Management for identifying and prioritizing vulnerabilities.
- CrowdStrike Falcon Intelligence: Threat Intelligence for staying ahead of emerging threats.
- Falcon Search Engine: Malware Search Engine for quickly searching and identifying malware.
- Falcon Sandbox: Automated Malware Analysis for analyzing and understanding malware behavior.
- Falcon Cloud Workload Protection: Protection for cloud workloads on AWS, Azure, and GCP.
- Falcon Horizon: Cloud Security Posture Management (CSPM) for monitoring and securing cloud environments.
- Container Security: Security solutions tailored for containerized environments.
- Falcon Identity Threat Protection (ITD): Protection against identity-based threats.
- Falcon Zero Trust: Solutions for implementing zero trust security principles.
Sophos Intercept X

Sophos Intercept X is a robust cybersecurity solution equipped with a variety of core features designed to provide comprehensive protection against modern threats. Here’s an overview of its key components:
- AI/Machine Learning: Leveraging artificial intelligence and machine learning algorithms to detect and prevent advanced threats in real-time.
- Access Controls/Permissions: Managing and controlling access to sensitive data and resources, ensuring only authorized users have access.
- Activity Dashboard: Providing a centralized dashboard to monitor security events, alerts, and activities across endpoints.
- Activity Tracking: Tracking and logging user activities, file modifications, and system changes for forensic analysis and threat investigation.
- Alerts/Escalation: Generating alerts for suspicious activities or security incidents and escalating them to appropriate personnel for further investigation and response.
- Anti-Virus: Traditional antivirus protection to detect and remove known malware, viruses, and other malicious software.
- Application Security: Ensuring the security of applications by monitoring for vulnerabilities, misconfigurations, and unauthorized access attempts.
- Behavioral Analytics: Analyzing user and system behaviors to detect anomalous activities and potential security threats.
Pricing Comparison
Pricing Structure of CrowdStrike Falcon
Falcon Pro offers next-gen antivirus with integrated threat intelligence, while Falcon Enterprise expands to include endpoint detection and response (EDR) and threat hunting; Falcon Elite provides integrated endpoint and identity protection, advanced threat hunting, and identity security, but requires contacting sales for pricing.
Pricing Structure of Sophos Intercept X
Sophos Intercept X offers custom pricing. It provides cloud-managed endpoint security with quick deployment, simple per-user pricing, and no hidden costs, providing options for varying levels of protection: Advanced, Advanced with XDR, and Advanced with MDR Complete, ensuring comprehensive defense against breaches, ransomware, and emerging threats.
CrowdStrike vs. Qualys: What Do Users Think?
CrowdStrike Falcon User Reviews
Users appreciate CrowdStrike Falcon’s exceptional EDR capabilities and fast response from the managed SOC, as well as its ability to map out threat vectors for visualization.
Exceptional EDR capabilities along with fast response from the managed SOC. I like the way the product maps out any threat/potential threat vector. It provides a great visulatization for users to trace the source.
G2 User Review of CrowdStrike Falcon
However, they are complaining about the premium price of the endpoint security solution and the need for improvement in support compared to other solutions.
Some organizations may find the price of CrowdStrike Falcon’s premium endpoint security solution to be on the expensive side. Also, compared to some other endpoint security solutions, CrowdStrike Falcon’s support can be improved.
G2 User Review of CrowdStrike Falcon
Sophos Intercept X User Reviews
Users appreciate Sophos Intercept X’s seamless integration with other software, minimal interference with daily tasks, intuitive cloud-based management, and effective prevention of issues like clicking on malicious links.
First , it intergrates well with the other software we use. We have had very few problems with it interfering with people doing their jobs like we have with Symantec. The cloud based management is very intuitive. You can really dig deep into any issue with the XDR portion of the program. The threat hunting capabilities are really impressive but difficult to use. I have found that Intercept X stops most problems like people following bad links in web sites from happening. Intercept X is very easy to deploy.
G2 User Review of Sophos Intercept X
However, some find the threat hunting capabilities impressive yet difficult to use. Concerns arise regarding security breaches.
I have recently received scam emails which detailed some of my security information. I do not know if this is a result of a third party having had customers’ information being hacked, or of Sophos not protecting users adequately, so I have therefore given it a neutral rating.
G2 User Review of Sophos Intercept X
CrowdStrike vs. Sophos: What Does Reddit Think?
CrowdStrike is appreciated by cybersecurity professionals for its effectiveness, ease of management, and ability to intervene or investigate.
Sophos receives mixed reviews, with complaints about vague logs and isolation of devices without clear reasons, as well as criticisms of resource consumption, but it is still acknowledged as a good antivirus product for threat detection and elimination.
Here’s what some have to say about CrowdStrike and Sophos:
Crowdstrike is by far my favorite tool in our toolset and has definitely saved our asses before. Easy to manage and highly effective. We don’t have their monitoring service. The Windows defender standard is basically impossible to manage at an Enterprise level. The product itself is effective but there is no great way to manually intervene or investigate”.
Reddit Review of CrowdStrike and Sophos
Our org is actively looking at CrowdStrike for endpoint. Sophos is vague in its logs and often isolates devices with no clear reason as to why other than “hey this process caused it” and that’s all. For us, it’s typically native Windows processes like explorer.exe, and that’s all the information it provides which is practically useless.
Reddit Review of CrowdStrike and Sophos
Sophos is a good AV product for its ability to detect and eliminate a threat, but it is extremely resource hungry. This needs to be considered when ordering end-user devices.
Reddit Review of CrowdStrike and Sophos
CrowdStrike vs. Sophos: How to Choose the Best Solution
When it comes to choosing the right cybersecurity solution for your needs, there are several important factors to consider. Here’s a breakdown to help you decide between CrowdStrike and Sophos:
1. Your Risk Profile
Consider how well the cybersecurity solution aligns with your specific security needs and risk profile.
Evaluate factors such as the types of threats most relevant to your business, data sensitivity, compliance requirements, and existing IT infrastructure.
While deciding about a cybersecurity platform, a key factor a business should consider is the alignment of the platform with the business’ specific security needs and risk profile. This involves assessing the types of threats most relevant to the business, the sensitivity of the data being protected, compliance requirements and the existing IT infrastructure.
2. Vendor’s Development Practices and Policies
Ensure that the solution follows secure development practices and has zero-trust policies in place to minimize the risk of being leveraged as an attack vector.
Look for vendors with a strong commitment to reducing risk rather than increasing it.
Businesses should ensure the cybersecurity solutions they purchase reduce their risk, not increase it. This sounds like a no-brainer, but recent vulnerabilities—such as Citrix Bleed and coordinated attacks on firewalls at dozens of energy suppliers—show that there’s real risk. Look for solutions that have secure development practices and zero-trust policies in place so they can’t be leveraged as an attack vector.
3. Advanced and Additional Protections
Assess whether the solution provides advanced or additional protection beyond your current capabilities.
Consider the time and resources required to operate the solution and weigh them against the increased protection it offers.
When a business is considering a new cybersecurity platform, its leaders should strongly consider if the product provides advanced and/or additional protection beyond the company’s existing capabilities—and consider the risk of inaction. Businesses should also consider the time and resources needed to operate a new cybersecurity platform, as well as whether any increased allocations are worth the increased protection.
4. The Different ‘Weapons’ You Need
Choose solutions that address the specific attack surfaces relevant to your business.
Look for best-of-breed solutions tailored to your unique cybersecurity needs rather than relying on a single vendor for all security layers.
Cybersecurity is extremely complex, because not only do you have a multitude of attack surfaces, but you also need different “weapons” to defend yourself. No single company sells all of these, so it’s important to pick best-of-breed solutions predicated on the attack surface.
5. The Potential Business Impact
Understand the potential business impact of implementing the cybersecurity solution.
Consider factors such as business uptime, minimizing disruptions to daily operations, and maintaining operational efficiency alongside robust security measures.
Besides choosing between best-of-breed or “single pane of glass” (that is, a platform delivered by one vendor that covers all layers of protection) solutions, one of the top things organizations need to understand is the potential business impact the product or platform will create. It’s not just about security—it’s also about business uptime and minimizing the impact on business continuity the product will cause (and it will).
An Alternative for CrowdStrike and Sophos? Why Not Heimdal®?
If CrowdStrike and Sophos aren’t cutting it for you, consider Heimdal® for unified, automated cybersecurity.
Heimdal’s XDR – Unified Security Platform solution combines advanced threat detection, automated incident response, and threat hunting into a unified platform. This empowers organizations to proactively defend against sophisticated attacks.
Our solution uses the Extended Threat Protection (XTP) detection engine. Supported by AI/ML predictive models, this technology will quickly identify threats and take appropriate action.
By utilizing MITRE ATT&CK methodologies, Heimdal® gives security and IT teams enhanced forensics information, ransomware data processing, bilateral telemetry, and a comprehensive picture of the attack chain.
This way, it enables them to successfully defend against even the most complex attacks.
Heimdal® Suite of Solutions:
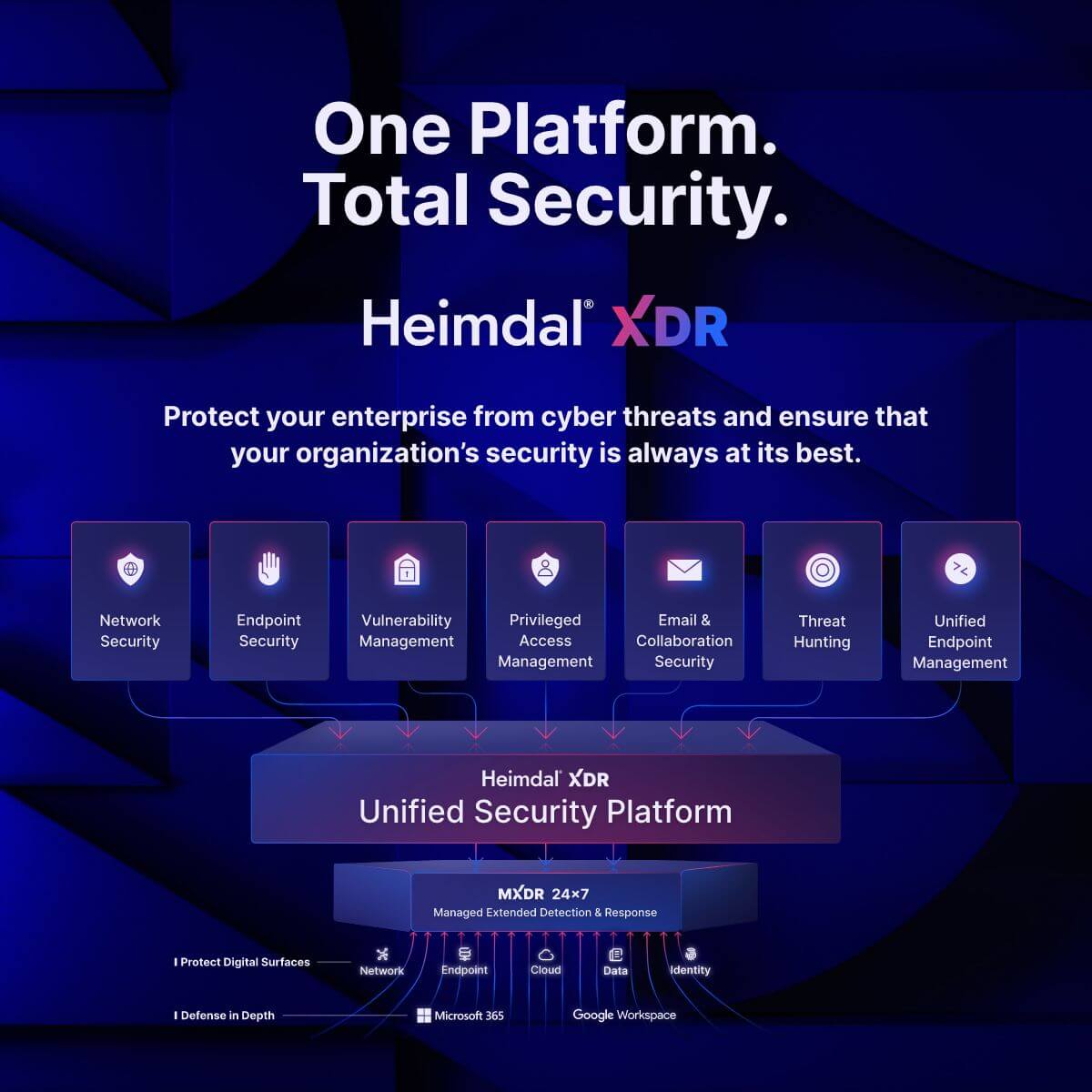
Heimdal® offers a comprehensive suite of solutions tailored to meet the diverse needs of organizations:
- MXDR Service: Sprouting from the XDR solution, Heimdal®’s MXDR service combines threat detection and response, endpoint security, and data protection into a unified platform, providing organizations with robust defense mechanisms against cyber threats.
- Patch and Asset Management: Heimdal®’s Patch and Asset Management solution streamlines the patching process, ensuring systems remain up-to-date and secure against known vulnerabilities. With automated patch deployment, customizable policies, and comprehensive reporting capabilities, organizations can maintain compliance and mitigate risks effectively.
- Cybersecurity Tools: Heimdal® provides a wide range of cybersecurity tools, including network security, vulnerability management, privileged access management, endpoint management, threat hunting, email, and collaboration security, among others. These tools equip IT professionals with everything they need to deliver top-notch cybersecurity services to their clients.
Why is Heimdal® a Great Alternative?:
- Comprehensive Protection: Heimdal®’s MXDR service offers holistic protection against cyber threats, covering detection, response, endpoint security, and data protection. This comprehensive approach ensures organizations of all sizes and industries can effectively safeguard their assets and sensitive information.
- Tailored Security Features: Heimdal®’s solutions are adaptable to organizations’ unique requirements, making them suitable for multinational corporations, SMBs, and everything in between. IT professionals can leverage Heimdal®’s flexible offerings to enhance their clients’ security posture and mitigate cyber risks efficiently.
- Customization and Integration: Heimdal®’s Patch and Asset Management solution stands out for its customization capabilities, allowing IT professionals to tailor the software to their specific business needs. Furthermore, Heimdal® offers seamless integration with other modules, providing IT professionals with a unified platform to address their clients’ cybersecurity needs comprehensively.
- Ease of Management: With Heimdal®, IT professionals can efficiently manage cybersecurity tasks across multiple clients through an intuitive dashboard and automated processes. This saves time and resources while ensuring clients’ systems remain secure and compliant with industry regulations.
What People Like About Heimdal®
People love Heimdal® for its generous selection of cybersecurity solutions boasting the world’s widest cybersecurity platform with 13 products , unified all-in-one approach, amazing customer support and overall ease of use.
It features highly customizable solutions, meaning that companies of all kind will find the right balance for their needs whatsoever.
Pricing:
Heimdal®’s pricing is flexible and tailored to the specific needs of IT professionals. Organizations can book a call with Heimdal®’s experts to receive more information on pricing plans and benefit from an exclusive demo of the solutions.
This personalized approach enables organizations to choose the right package that aligns with their budget and requirements, ensuring maximum value and ROI.
Conclusions
Choosing the right cybersecurity solution is crucial. We’ve looked at CrowdStrike and Sophos, but what if they don’t quite fit your needs? That’s where Heimdal® comes in.
Heimdal® offers automated, unified cybersecurity. Its MXDR service provides solid protection for businesses of any size.
When it comes to keeping your business safe, don’t settle for the usual options. Consider Heimdal® for straightforward, effective cybersecurity.
Frequently Asked Questions (FAQ)
What is the difference between Sophos Central and CrowdStrike?
Sophos delivers protection directly on the device and responds automatically, swiftly eliminating threats as they arise. In contrast, CrowdStrike collects and evaluates data in the cloud, which can lead to delays in response.
What is the difference between Sophos XDR and CrowdStrike EDR?
Sophos employs on-device protection in real-time to thwart ransomware, halt exploits, restrict lateral movement, deploy dynamic defenses against direct attackers, and autonomously isolate compromised endpoints. On the other hand, CrowdStrike predominantly depends on cloud-based data collection for threat detection.
What is better than CrowdStrike?
Consider Heimdal® as a strong alternative to CrowdStrike. Heimdal® prioritizes on-device protection and automated response, offering a comprehensive suite of cybersecurity solutions. Unlike CrowdStrike’s reliance on cloud-based data collection, Heimdal® emphasizes proactive, unified defense mechanisms for swift and effective protection against evolving threats.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










