Contents:
CrowdStrike and Carbon Black have their fair share of users and supporters. They’ve also earned almost 5 stars on Gartner for their EDR solutions.
As always, the devil is in the details. Security operations differ depending on a company’s needs, infrastructure, and resources.
That’s why it’s tough to judge if an EDR tool is overpriced, superior, or just worth it. Factors like automation capabilities, ease of access, visibility, tech support responsiveness, and pricing all come into play.
To get the best bang for the buck, read this article and see which cybersecurity software works best for your company.
Key takeaways:
- CrowdStrike is known for low resource consumption and effectiveness
- Carbon Black integrates well with other software
- CrowdStrike ranks 7 positions higher than Carbon Black on Gartner (rank 6 vs rank 13)
- Reviewers say both CrowdStrike and Carbon Black should improve tech support
- Automation, integration, and unity are the three most wanted key features in endpoint security software 2024
What is CrowdStrike?

Source – G2 website
CrowdStrike offers cybersecurity solutions, leveraging cloud-native technology to provide threat detection and real-time incident response.
They launched their endpoint detection and response (EDR) module in 2013. Now they offer:
- Managed Detection and Response
- Cloud Detection and Response
- Identity Protection
- Technical Risk and SOC assessment
- Endpoint Recovery
- Red Team vs Blue Team exercises, etc.
Their CrowdStrike Falcon platform is cloud-based and uses a lightweight-agent architecture.
Features
- Threat hunting
- Single-agent design
- Behavioral learning and behavioral analytics
- Supports various OS: Windows, Linux, Mac
- Cloud-based
- Firewall management
- API integration
Pros
Low resource consumption is one of the recurrent benefits that users name in their reviews on Gartner.
I barely notice any performance hit on my PC, compared to other solutions. If something dangerous were to happen, it immediately deactivates my network to limit the spread of a virus. I generally do not notice it’s there, which is a good thing.
Source – Gartner review
Other pros of CS Falcon are:
- low system impact
- accurate threat identification and blocking
- real-time visibility and response
- effective technical support
- continuous monitoring
- easy to install and scalable
Cons
Although the product is praised as one of the best in its category, Gartner reviewers also highlighted some CrowdStrike cons. The review below is dated December 2023:
Need to improve the services and support. Once we create a ticket next working day only, we will get response from the support team
Source – Gartner review
This subreddit on their Reddit community can give you a wider view regarding CrowdStrike’s potential troubleshooting issues.
Other cons CrowdStrike Falcon users mention on software review platforms are:
- High cost compared to competitors
- Complex installation process
- Requires high-skilled staff
- Poor customization
Pricing
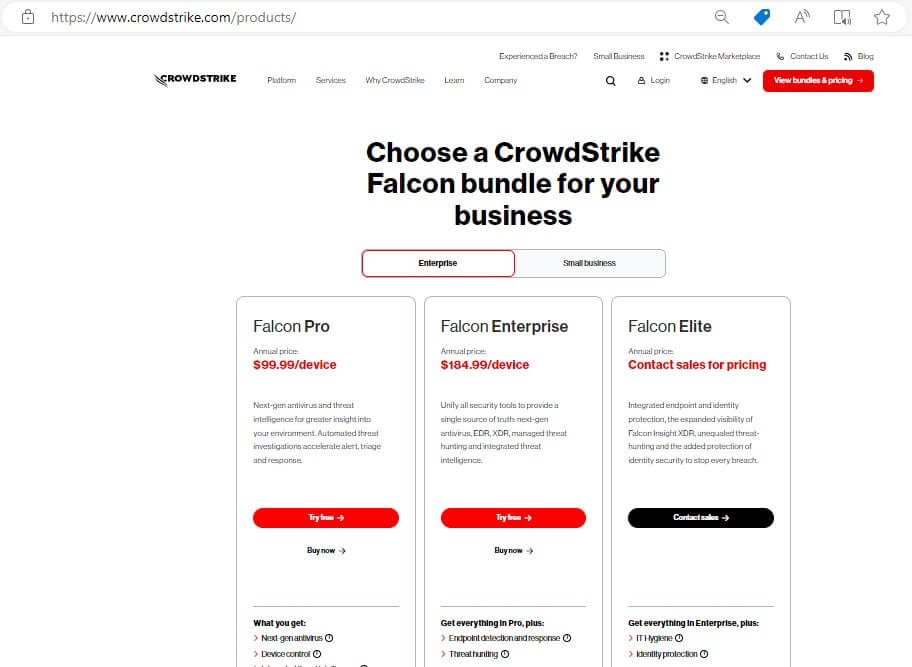
CrowdStrike showcases three price options for large companies and two for small businesses. Of course, each package includes different tools and features.
- The basic package (Falcon Pro) for enterprises is $99.99 /device/year.
- SMBs can start using Falcon Go, which is $4.99/device/month. That’s $59.88 per year. Falcon Go offers a next generation AV, device control and express support.
- For some of CrowdStrike’s premium services they reveal the price by request.
What is Carbon Black?
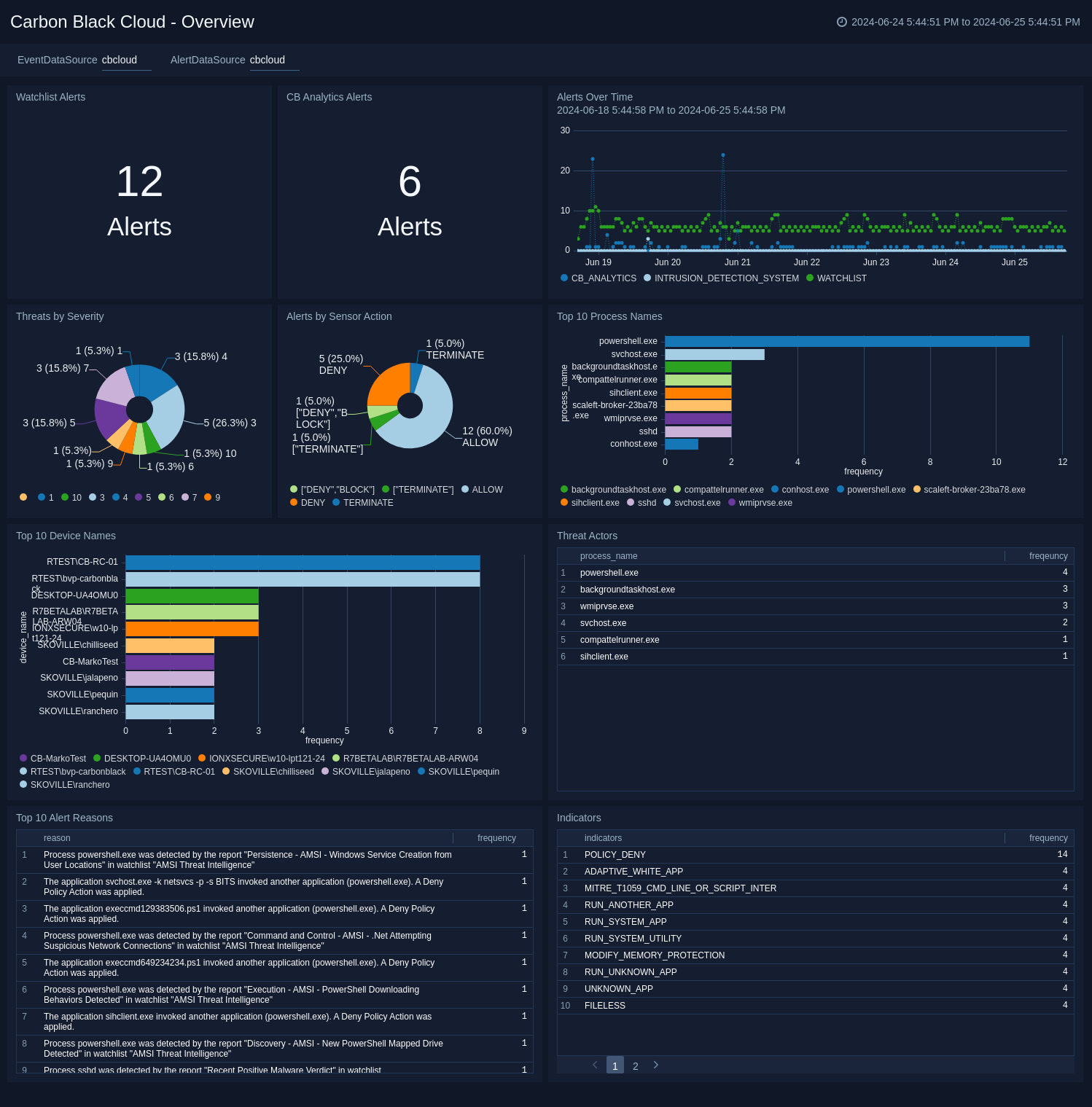
Source – Sumo Logic website
VMware Carbon Black is another notorious cybersecurity brand that offers an endpoint security platform. The platform uses analytics and machine learning for threat hunting and offers real-time response to threats.
Their offer includes:
- Endpoint Detection and Response (EDR)
- Managed Detection and Response (MDR)
- Asset Management
- App control
- Host-based firewall
Features
- Threat hunting
- Behavioral endpoint detection and response (EDR)
- Compatible with various OS: Windows, Linux, Mac
- Single-agent platform
- Offline scanning available
- Cloud-based
- Integrated firewall management available
- API integration
Pros
Cloud centralized control is one of Carbon Black’s most appreciated features, according to Gartner reviews.
You can deploy it through the cloud so that even if your stuff is outside of your controlled environment, you are still under control, based on the policies you create. The policies are controlled through the cloud. For example, if I don’t allow anyone to do a certain activity or to install a particular app, and a consultant or a partner who is not part of our environment is doing so, it will stop them as well., says Imad Taha, CIO at a construction company
Source – Gartner reviews
Other pros of the Carbon Black endpoint protection platform are:
- User friendly
- Advanced machine learning Antivirus
- Scalable
- Integrates with other products
- Easy to configure
Cons
Just like CrowdStrike, VMware Carbon Black endpoint too has its downsides, according to its reviewers. Although some describe it as user-friendly and easy to configure, there are also users that experienced the opposite:
Complex deployment. Having to run manual scripts with company codes is not convenient for deployments. Heavily resource intensive. It’s always at the top of the list of used resources in terms of memory and CPU
Source – Gartner review
Other cons to this endpoint security solution are:
- Slow support
- Frequent false positive alerts
- Can’t schedule scanning
- Automate scanning not available
- Can only set policies manually
- Can be resource-intensive
Pricing
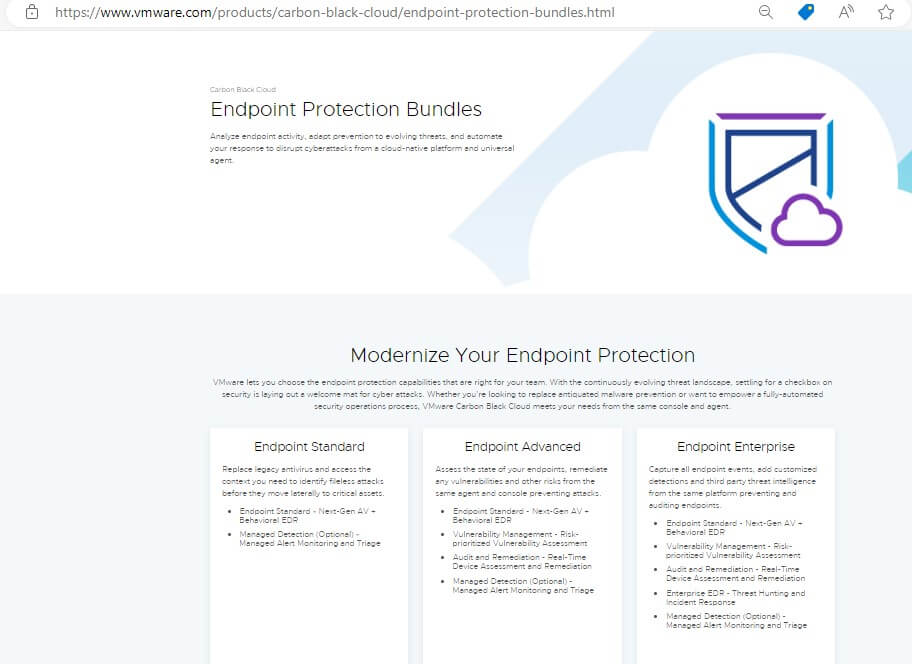
VMware Carbon Black doesn’t reveal any prices on their website. However, their offer is structured in three packages of various complexity:
- Endpoint Standard – only includes Next-Gen AV and Behavioral EDR, but you can add MDR by request
- Endpoint Advanced – includes vulnerability management, device assessment and remediation. MDR is also optional
- Endpoint Enterprise – includes all the above, plus EDR. Managed Detection is optional
Trending key features of cybersecurity tools 2024
Now you have a good understanding of what both CrowdStrike and Carbon Black have to offer. Before you choose, let’s see what the latest trends in cybersecurity tools are for 2024.
Why? Because keeping up with technology bolsters your company’s security posture. A traditional antivirus, for example, can’t keep up with nowadays hacking tools.
Automation, integration, and unification are key features of modern cybersecurity tools. Let’s find out what they do for you and what makes them essential.
Automation
Automation helps perform endpoint protection tasks without human intervention. This includes:
- patch management
- threat detection
- incident response
- security policy enforcement
By automating redundant tasks, security teams can:
- Detect malicious activity in real-time, by continuously monitoring network traffic and endpoints for suspicious activities
- Respond on the spot, by blocking malicious communication before it happens or immediately isolating compromised devices.
- Get more time to focus on more strategic initiatives
- Reduce human error
- Enforce security policies across the whole organization
Integration
Integration refers to the ability of different cybersecurity tools and systems to work together. An integrated security solution can share data and intelligence with other tools, which leads to better threat detection and response.
Here’s what makes integration a key feature:
- Enhances threat detection due to a unified view of the organization’s IT environment: networks, endpoints, and cloud infrastructure. Seeing all infrastructure at the same glance helps IT teams find and respond to potential threats faster.
- Improves coordination by data sharing between disparate security tools and teams. Real time communication speeds up incident response.
- Streamlines workflows and reduces manual effort by eliminating duplicate tasks and data silos.
Unification
Unification brings all security tools under a single umbrella. Using a single platform for monitoring, reporting, responding, etc. comes with lots of benefits:
- The ability to manage and monitor all security operations from the same dashboard, which means easier management.
- Better visibility due to bringing endpoint protection, network security, and threat on the same dashboard
- Enhanced security, as total visibility leads to faster threat detection and response
- Streamlined workflows, as unification eliminates the need to switch between multiple tools and interfaces. Unification makes security teams more efficient.
CrowdStrike vs Carbon Black
Both Carbon Black and CrowdStrike prioritize automation, integration and unification. They offer automated threat hunting, incident response and patch management, and do a great job protecting endpoints. Also, both Carbon Black and CrowdStrike use behavioral analysis to detect advanced threats.
Some users warned that you’ll need to manually create and update policies for the AV part, if you choose Carbon Black’s Endpoint Standard.
Both solutions are agent-based, and you can use them from a unified dashboard.
However, users say CrowdStrike has the lowest false positives alert ratio. One main difference is that CrowdStrike installs at a kernel level. This means it detects more events off the endpoint. More events history leads to better threat intelligence and better defense.
On the other hand, users say Carbon Black is easier to customize.
CrowdStrike & Carbon Black in users’ reviews
Now you have a broad view on the key features, strong points, and downsides of both security solutions.
VMware Carbon Black ranks 13th on Gartner’s Best Endpoint Protection Platforms Reviews 2024, with 398 ratings. That’s 7 ranks below CrowdStrike Falcon, which sits on the sixth rank, with 1439 reviews.
CrowdStrike gets 4.8, with 98% of its users willing to recommend it, while Carbon Black gets 4.4 out of 5 stars, and 87% users would recommend them.
Although CrowdStrike Falcon is obviously more popular, both are top cybersecurity solutions, with high scores in reviews. So, how do you decide which works best for you?
Who’s it for?
CrowdStrike
Users say CrowdStrike is an efficient, but pricey and hard to learn tool, if you don’t have much experience with endpoint security.
The cost and the need for a highly skilled workforce are not usually a problem for large companies (10,000+ seats). Small and medium companies that lack technical talent could find CrowdStrike hard to use and configure.
Carbon Black
Large companies working in Telecommunications, Healthcare, Banking and Finance, Retail and Manufacturing are some of Carbon Black’s users. Reviewers on Capterra say it’s pricey, so small and medium businesses can’t afford it.
Like CrowdStrike’s, their dashboard is easy to use and intuitive if the user already knows their way around endpoint security. A less skilled security team would find the learning curve steep and might misconfigure settings.
Heimdal’s alternative to CrowdStrike and Carbon Black
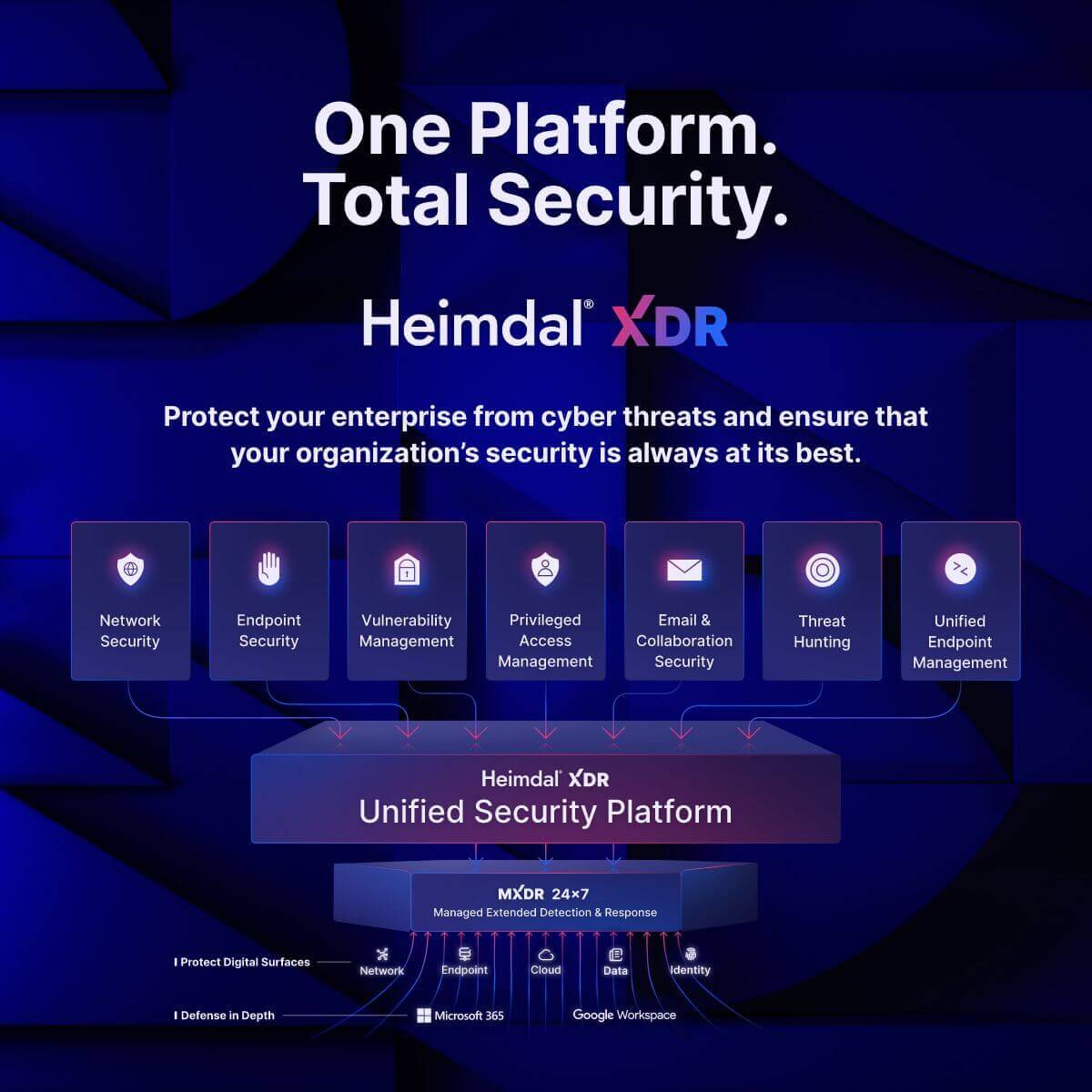
Heimdal offers a user-friendly, cloud-delivered XDR solution from a unified dashboard.
Pricing and easy to learn dashboard are not the only things that make it a better choice to protect endpoints. Heimdal’s XDR offers DNS filtering, which other endpoint detection and response tools, like CrowdStrike, don’t. This feature increases the anomaly detection capabilities and increases your chances to maintain a safe environment.
Heimdal’s XDR platform integrates:
- Network security
- Endpoint security
- DNS security
- Next-Gen AV, able to detect advanced cyber threats
- Ransomware encryption protection
- Vulnerability management
- Patch and asset management
- Infinity management
- Privileged access management
- Privilege Elevation & Delegation Management
- Privileged Account & Session Management
- Application Control
- Email security
- Threat hunting
- Unified endpoint management
- Remote management
- BitLocker management
Heimdal XDR platform. Who’s it for?
Heimdal works best for medium-sized and large businesses looking for comprehensive endpoint security and easy management. Its lightweight agent and focus on traffic filtering make it a good match for organizations with limited IT resources or technical expertise. You can use it to secure various operating systems: Windows, Linux and MacOS.
Companies running on a hybrid or remote work environment appreciate Heimdal’s remote monitoring and management capabilities and ease of deployment.
Also, scalability makes Heimdal one of the best software for MSPs and MSSPs. The fact that it brings it all together on the same dashboard is another way that Heimdal’s XDR supports MSPs worldwide.
Heimdal offers users full flexibility. You can choose to use the XDR platform, or only pick one of its tools. Managed services are also available, if you’re running a large, complex IT infrastructure.
Heimdal’s patch and asset management, DNS Security, Privileged Access Management and next generation AV integrate with various other tools, regardless of vendor.
If a highly skilled workforce is a challenge in your company, go for Heimdal MXDR, which is also available.
Another advantage Heimdal’s user mention on reviews is its support service, which was described as
Support is second to none – very responsive and helpful. Peace of mind is absolute and the admin overview and ability to remediate remotely is fantastic. It is also built for the work-at-home culture when have settled into after covid.
Source – Capterra reviews
Conclusion
Is choosing between Carbon Black and CrowdStrike really the best option for you? Before you make a decision, see what other vendors have to offer in the field of endpoint protection.
Think about buying endpoint security software like you do when buying a car:
- What will you use it for?
- What features do you need it to have?
- How does your choice impact your budget in the long run?
- Is there a similar alternative on the market at the same or lower price?
You shouldn’t pay for a Ferrari if you’re usually driving your three kids to school at rush hour. Or go for a SUV if you don’t do off roads.
Set realistic expectations, do your research, put it all on paper and decide what endpoint protection tool suits you better.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

- End-to-end consolidated cybersecurity;
- Complete visibility across your entire IT infrastructure;
- Faster and more accurate threat detection and response;
- Efficient one-click automated and assisted actioning










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security