Contents:
A new spam campaign pretending to be from Booking.com is now targeting users. The emails carry a document containing macro code. If someone clicks on the document, opens it, and allows the execution of the macro code, a loader will be spawned.
This will download and run ransomware of the Sodinokibi class.
How does the fake Booking.com email that infects you with ransomware work?
Below you can see how a Sodinokibi ransomware email looks like:
–
From: [Compromised email account]
Subject:
Booking.]com – New booking! (1571165841, Monday, 17 June 2019)
Attached:
[name of recipient].doc
–
If one clicks on the content of the document, the embedded object will decode the file “ms-word.exe”.
Once the file is run, it will spawn a shell that will run the ransomware’s loader, as you can see below:
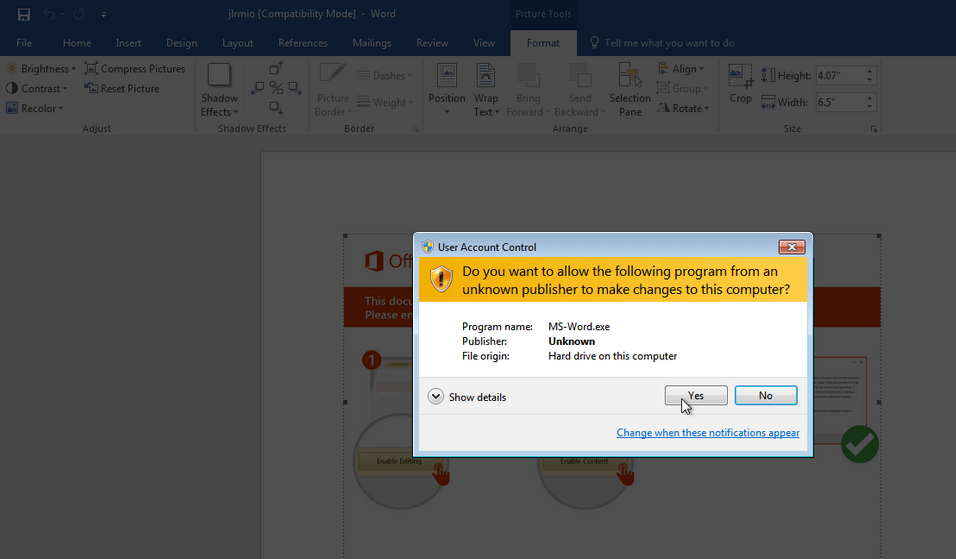
Similar to other ransomware families, the spawned shell will start with deleting shadow in order to make the restoration of the machine more complicated:
“C:\Windows\System32\cmd.exe” /c vssadmin.exe Delete Shadows /All /Quiet & bcdedit /set {default} recoveryenabled No & bcdedit /set {default} bootstatuspolicy ignoreallfailures.
The payload is difficult to be analyzed since the loader is packed with a custom packer.
The packer is different from variant to variant. But what they all have in common is that they always use a PE overwrite technique.
Then, it will connect to the following URL, from which it will run the main component (sanitized by CSIS) http://btta[.]xyz/hoja.exe.
When data files on the local machine have been encrypted, the following guide will appear to the victim (screen shot is from a previous infection, but is identical to this variant):
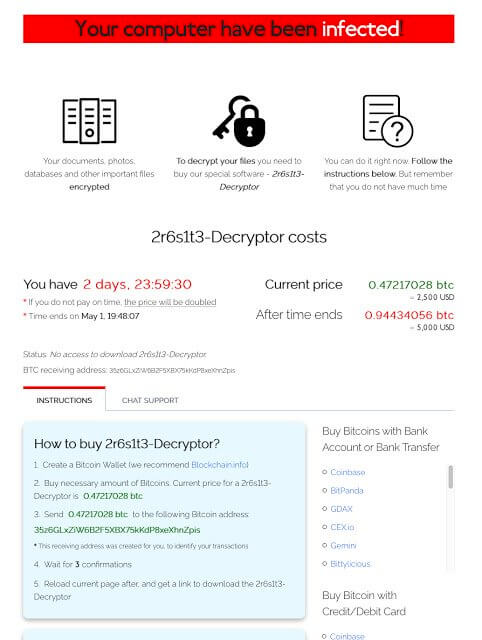
All posts to the C&C server are encrypted with AES256 in CTR (‘counter’) mode.
Only 17 antivirus solutions out of 53 picked it up:
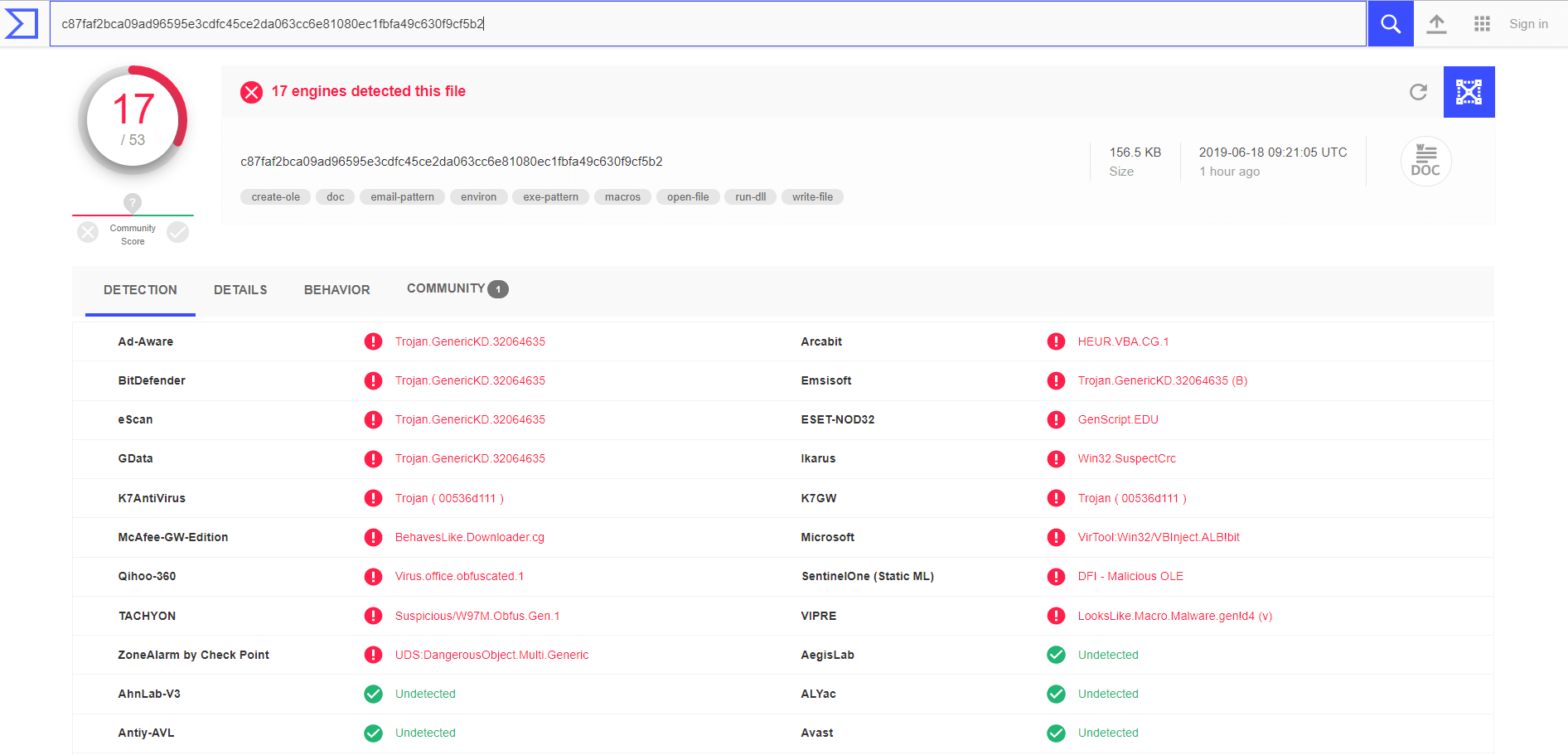
See the full detection test here.
Sodinokibi is a GandCrab ransomware strain
Sodinokibi is a GandCrab offspring, which was observed for the first time back in late April. At that time, it spread via vulnerable Oracle WebLogic servers.
This is a very real and serious threat.
Sodinokibi hit several companies in Denmark during the past week and caused downtime.
How to protect yourself against the Sodinokibi ransomware (and any ransomware in general):
- NEVER pay the ransom. There is no guarantee that you’ll ever recover your files.
- DO NOT open suspicious emails or attachments. Always make sure the emails are genuine.
- Keep your software updated, as malware mostly targets older systems.
- In case you get infected with ransomware, always back up your files.
- Stay informed about the latest types of cyber threats. Here are some free educational resources you can use to strengthen your cybersecurity knowledge.
- Use next-gen threat prevention solutions to make sure ransomware will never infect your computer.
Your active Thor subscription will protect you from unwanted threats. However, if you check your email from other devices unprotected by Thor, please be careful and double check if the messages you receive are legitimate.
*This article features cyber intelligence provided by CSIS Security Group researchers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










