Contents:
A new malware was detected. Named by security researchers AbstractEmu, its attack methods consist of the use of anti-emulation checks and also code abstraction techniques. All these can result in compromised devices rooting with the goal of devices control takeover and system settings tweaking.
The ones who identified the new Android rooting malware under discussion were the Lookout Threat Labs’ security researchers who named it AbstractEmu.
The same experts explained in their report how AbstractEmu posed as functional apps so when a user downloads and opens the app, it will be activated.
AbstractEmu does not have any sophisticated zero-click remote exploit functionality used in advanced APT-style threats, it is activated simply by the user having opened the app. (…) As the malware is disguised as functional apps, most users will likely interact with them shortly after downloading.
Bundled with Apps
According to BleepingComputer, the new malware was bundled with 19 apps that could be found in Google Play or stores that contained third-party apps. We’re talking about Amazon Appstore, Aptoide, Samsung Galaxy Store, or APKPure.
Among the apps that bundled the malware password managers, data savers, and also app launchers could be found. However, these were removed from Google Play following the discovery, but it did not prevent other app stores to distribute them.
Lite Launcher is one of the apps that carried this malware on Android devices with 10,000 downloads registered at the moment of its removal from Google Play.
AbstractEmu: Details on How It Works
AbstractEmu works like this, as per the researchers’ report:
- After installation, AbstractEmu harvests and transmits info to its C2 server (command-and-control);
- During this time, the malware stays up for other commands;
- This uses many tools that are basically exploits intended to target vulnerabilities like CVE-2020-0041 for instance, tools that are useful to perform Android device rooting;
- Another MediaTek chips bug is abused by means of the CVE-2020-0069 exploit;
- The C2 server commands can determine AbstractEmu to perform file exfiltration and harvesting, to root the compromised devices or make sure new apps are installed and this would be based on their novelty or a certain pattern;
- What might happen after an affected device is rooted could be a series of actions like notifications monitoring, screenshot capturing, screen recording, or password resetting;
- Researchers also highlighted the fact that AbstractEmu gains access to various sensitive info through elevated privileges.
By using the rooting process to gain privileged access to the Android operating system, the threat actor can silently grant themselves dangerous permissions or install additional malware — steps that would normally require user interaction.
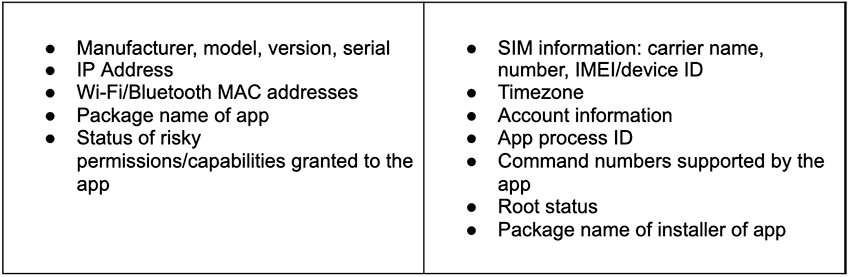
What System Info Can It Collect?
Here is a table mentioning what system info AbstractEmu can collect:
How to Stay Safe?
Malware makes every headline today: be it a RAT, ransomware, or a virus. We at Heimdal™ keep up with the latest cybersecurity trends and offer you effective solutions. Try our awarded Threat Prevention that will keep you away from threats having stunning accuracy, as it’s designed by means of Machine Learning, AI-based prevention, and cybercrime intelligence.
If you enjoyed this article, because we know that you surely did, don’t forget to follow us on Linkedin, Twitter, Youtube, or Instagram to never miss a thing we post.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










