Contents:
A Google Chrome browser extension named VenomSoftX is being deployed by Windows malware to steal cryptocurrency and clipboard contents as people browse the web.
The Chrome extension is a JavaScript-based Trojan. It also hijacks other internet browsers, including Safari and Firefox.
ViperSoftX has been around since 2020. Security researchers Cerberus and Colin Cowie discovered it in a report by Fortinet, and today Avast is publishing new details regarding the malicious browser extension operated by ViperSoftX.
An Overview of Recent Events
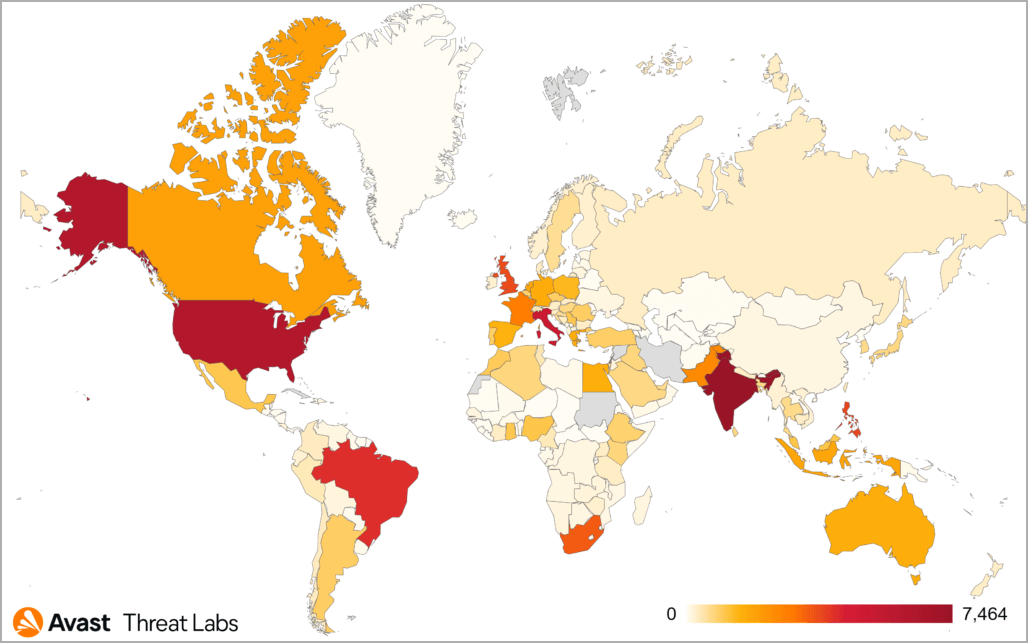
As of the beginning of 2022, Avast has been able to stop 93,000 ViperSoftX virus attacks on its customers. This mainly affects the US, Italy, Brazil, and India.
ViperSoftX distributes its cracked games and software through torrents.
Avast analyzed two malware samples and found that the two attackers had jointly earned approximately $130,000 by November 8th, 2022.
This stolen cryptocurrency was obtained by breaking into devices and diverting attempted transactions. It does not include profits from similar activities.
What do you think is in the downloaded executable? It’s actually a malware loader that decrypts AES data to create the following five files:
- Log file hiding a ViperSoftX PowerShell payload;
- XML file for the task scheduler;
- VBS file for establishing persistence by creating a scheduled task;
- Application binary (promised game or software);
- Manifest file.
The Virus That Infects Google Chrome
To start, let’s look at what ViperSoftX is capable of stealing. First, ViperSoftX performs fingerprinting of the infected machine, focusing on various types of information, including:
- Computer name;
- Username;
- The operating system’s information and architecture;
- Installed antivirus software.
This type of malware has different strategies:
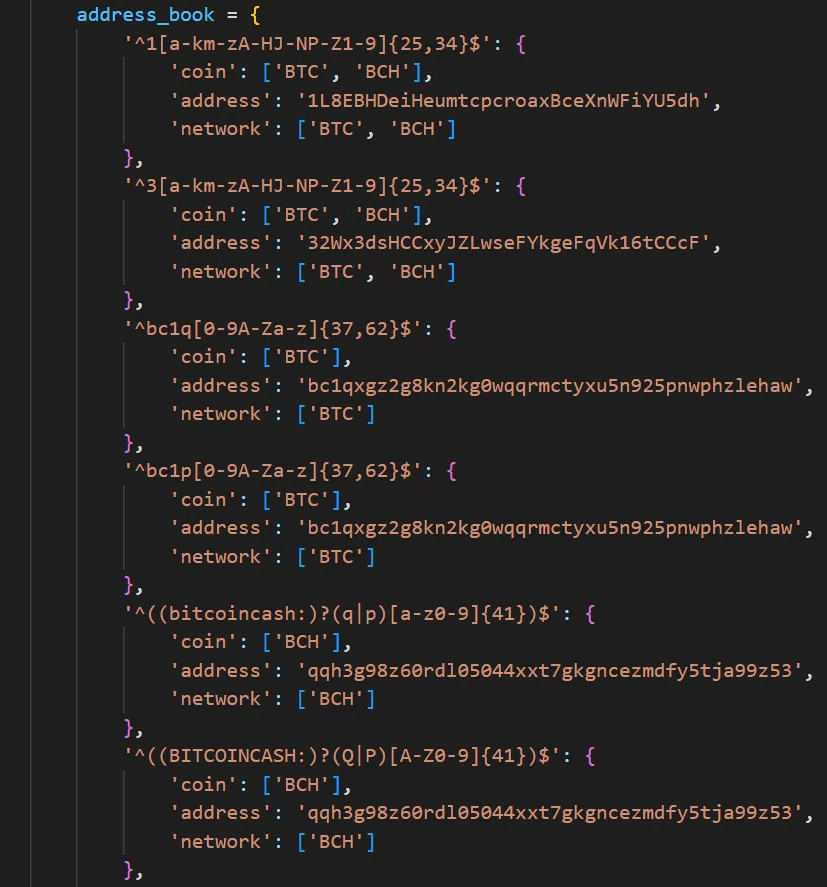
It will search familiar places for browser extensions and locally stored wallets. You can find the complete list of these locations in the Appendix.
It will also get general information such as your operating system, architecture, username-using Windows Management Instrumentation (WMI), and system variables.
The malicious code is just a single line of text that hides at the bottom of the log file and decrypts a payload. The payload is called VipersoftX stealer.
Newer ViperSoftX variants are similar to those analyzed in previous years, including stealing cryptocurrency wallet data, arbitrary code execution, payload downloads from the C2, etc.
A key feature of newer ViperSoftX variants is installing a malicious browser extension VenomSoftX on Chrome-based browsers (Chrome, Brave, Edge, or Opera).
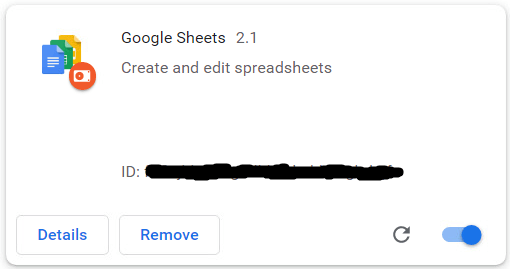
To stay hidden from the victims, the installed extension appears as a productivity app called “Google Sheets 2.1”. Security researcher Colin Cowie also reported seeing it installed as “Update Manager” in May.
While they may appear to target similar victims, VenomSoftX is doing something different to give the operators a higher success rate. The company mostly steals crypto by hooking API requests to big exchanges victims visits/have an account with, as explained in the report.
VenomSoftX has modified requests made to an API when sending money so they will be redirected to an attacker instead.
“When a request is made for an API to transfer money, VenomSoftX will intercept the request and tamper with it to redirect the money to the attacker instead.”, explains Avast.
This extension monitors Blockchain.com, Binance, Coinbase, Gate.io, and Kucoin services for transactions. It also records any addresses you copy to your clipboard so that others can’t use them.
Furthermore, the extension can modify HTML on websites to display a user’s cryptocurrency wallet address while manipulating the background elements to direct payments to the perpetrator.
The VenomSoftX extension will intercept all API requests to the services mentioned above. It then sets the transaction amount to the maximum available, siphoning all funds from a victim’s account.
And if you thought that was it, you’re wrong! In addition to ending cryptocurrency mining from your device, the extension will also attempt to steal your passwords entered on Blockchain.info.
“This module focuses on ![]() , and it tries to hook
, and it tries to hook ![]() ” explains Avast. “It also modifies the getter of the password field to steal entered passwords.”
” explains Avast. “It also modifies the getter of the password field to steal entered passwords.”
“The first step is to request the API endpoint from the hosted wallet. The JSON request parameters include the address and a hashed password. The wallet address, password, and secure connection are then bundled together in base64 format.”
If a user copies and pastes words or sentences into any website, the extension will check if those words or sentences correspond to the regular expressions shown above. If so, it will send them to the threat actors.
As Google Sheets is usually installed as an app under chrome://apps, you need to check your browser’s extension page to ensure it’s enabled.
If not, you’ll need to disable the extension and clear your browsing data to ensure the malicious add-on is no longer used.
Take The Next Steps With Heimdal®
This isn’t the first time hackers have used Chrome extensions as a threat vector. For example, VenomSoftX overlaps with ViperSoftX, an older malware that’s been tracked for some time.
So how can you stay safe?
The Heimdal® Next-Gen Endpoint Antivirus will intelligently monitor running processes within a customer’s IT environment and block anything that looks malicious or suspicious.
This solution has a high detection rate against malware, ransomware, rootkits, and brute-force attacks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










