Contents:
5G is no longer technology of the future, but a current reality. Entire markets have already started to switch to 5G, which marks the beginning of a new era. This is the only technology created so far with a huge potential to elevate the use of the Internet of Things (IoT), foster an environment of interconnectivity, and sustain economic growth. 5G will bring along a plethora of benefits, such as increased data speed, lower latency on network response time, and higher reliability. However, at the same time, new cybersecurity threats are likely to arise. This is why your business must be ready to face the 5G dangers.
Your company’s and customers’ sensitive data could be compromised due to cyber-attacks in a 5G world. What’s more, your connected IoT devices could be affected too, each and every one of them being likely to pose security risks for your entire network. And once IoT devices are overridden by cybercriminals, they can wreak havoc in your organization and even cause physical damage.
What is 5G?
First of all, let’s try to understand more about the 5G technology and why it can be so dangerous for your business from a cybersecurity standpoint.
The “G” stands for “Generation”. In the simplest terms, the higher the number close to the letter “G”, the higher the speed and the lower the latency. Here is a quick comparison between the 5 Generations:
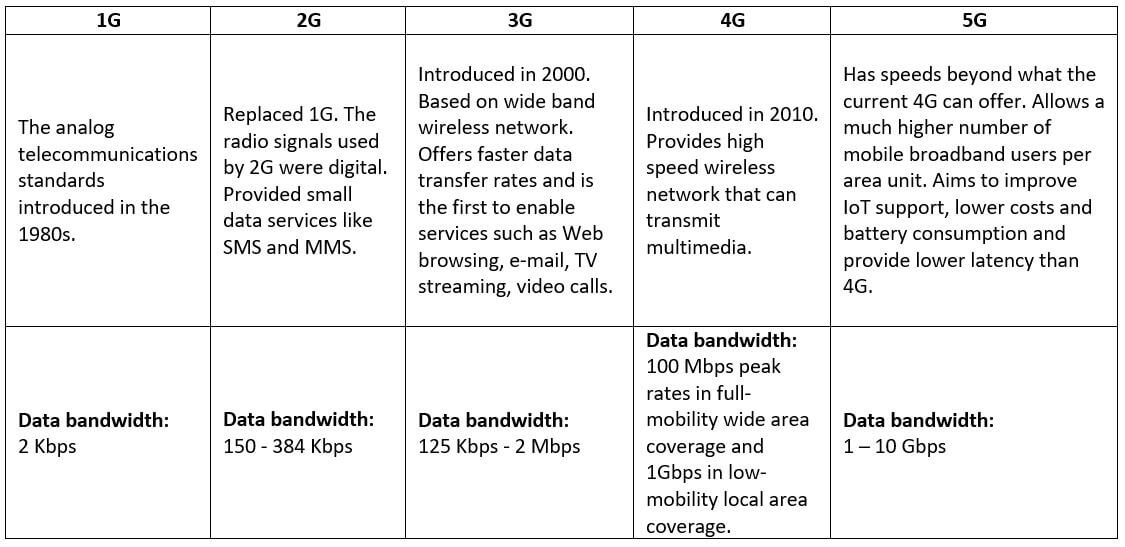
Source: Adaptation after “A Review of Wireless Mobile Technology”, published in the International Journal of Science and Research (IJSR).
At some point, 5G will most probably replace the existing 4G networks. According to Ericsson’s Mobility Report released in June 2019, 5G subscriptions will reach 1.9 billion by the end of 2024, making up over 20% of all mobile subscriptions at that time. So while we’re still quite early in the game, it is not too soon to start thinking about the 5G implications for your business, both positive and negative.
How will your business benefit from 5G?
Let’s start off with evaluating the potential benefits. As we transition to the 5G technology, your business can expect better use of resources and improvement of your daily operations and communication. More specifically, here are the main areas your business will benefit from once you’ll start using 5G:
#1. Increased network speed
As I’ve pointed out above, the first benefit that comes to mind is the high speed supported by the network, which will increase your employees’ productivity once they will be able to complete tasks much faster.
#2. Better communication
The virtual communication and collaboration will certainly be improved as well. Also, cutting-edge communication methods that involve VR and AR will be successfully sustained by the powerful 5G network.
#3. The IoT network will be taken to the next level
5G will seamlessly connect all the devices that make up your IoT network. This aspect will enable tremendous opportunities for IoT uses, ranging from drones, self-driving cars, VR and AR equipment, and other emerging technologies.
#4. More innovation
The 5G technology will most likely become a catalyst for innovation. In major industry verticals such as healthcare, automotive, and manufacturing we will witness technology advancements that have never been seen before.
#5. Reduced costs and energy consumption
The 5G technology will supposedly reduce the core network consumption by 90% and extend the battery life of your devices aims to extend device battery life ten times.
Organizations are impatient to use 5G
According to a survey recently released by Gartner, two-thirds of organizations are planning to deploy 5G by 2020. Yet apparently, businesses want to embark on the 5G journey faster than communication vendors can provide it. Furthermore, they are planning to use 5G networks mainly for IoT communications, with operational efficiency as key driver.
Gartner has also stated that, by 2022, half of the communication vendors which have completed commercial 5G deployments will not be able to monetize their back-end technology infrastructure investments. This will not be possible due to the fact that systems will not completely meet the 5G use case requirements.
“Most CSPs will only achieve a complete end-to-end 5G infrastructure on their public networks during the 2025-to-2030 time frame — as they focus on 5G radio first, then core slicing and edge computing,” said Sylvain Fabre, senior research director at Gartner.
Initially, communication service providers will focus on consumer broadband services, which may delay investments in edge computing and core slicing. And the latter are much more valuable and relevant to the 5G technology.
Security flaws in 5G enable various types of attacks
As pointed out by security researchers during Black Hat 2019, a security flaw in 5G allows Man-in-the-Middle (MiTM) attacks. It seems that security protocols and algorithms for 5G are now being ported from 4G standard and experts have discovered that this can allow device fingerprinting for targeted attacks and MiTM assaults.
How can this happen exactly? The 5G network is comprised of base stations, or cells, that cover a certain area. They connect to the cloud, and the latter connects to the base network. In order for the connection to be possible, 5G devices send information to the base station. The station then sends it to the chain for authentication to the core network. The information delivered includes details such as “whether or not voice calling is enabled, SMS ability, vehicle to vehicle communication (V2V) support, what frequency bands are being used, the device category, […] radio requirements”.
During the same Black Hat conference, researchers revealed that in 5G, as with 4G, the device capability information is sent to the base station before any security measures are applied to the connection. Basically, the traffic is encrypted from the endpoint to the base station, but since the device capabilities are sent before the encryption is applied, they can still be read in plain text. And this enables multiple types of attack, like Mobile network mapping (MNmap), bidding down, and battery drain on the narrowband Internet of Things (NB IoT) devices.
The research team that unveiled this threat was capable of creating a map of devices connected to a certain network and list very specific details like device manufacturer, operating system, version, model, allowing them to precisely categorize a device as an Android or iOS, IoT or a phone, car modem, router, etc. And this flaw opens the gate to targeted attacks against specific devices.
Attackers can intercept calls and track phone locations
Researchers have also discovered three security flaws in both 4G and 5G, which can be exploited to intercept phone calls and track the locations of cell phone users. And the scary part is that academics are saying that anyone with a little knowledge of cellular paging protocols will be able to conduct this kind of attack.
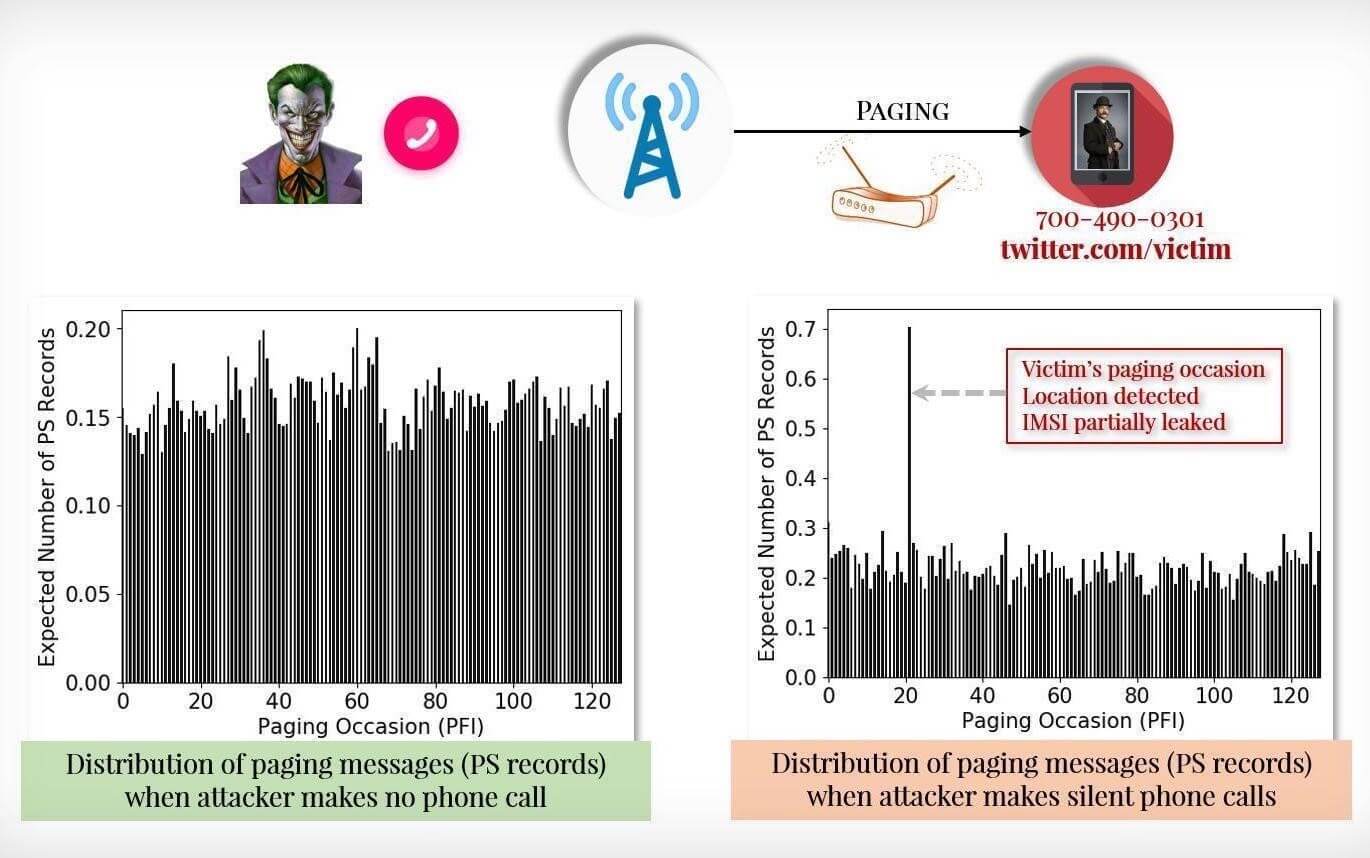
Image source: TechCrunch – The Torpedo attack — or “TRacking via Paging mEssage DistributiOn.
The 5G Dangers for Your Company
Now, imagine what a negative impact 5G could have on your business. First of all, it will certainly enable more entry points for cyberattacks. And while the level of connectivity and speed between your interconnected IoT devices will increase, multiple opportunities for malicious actors to break into your systems will unfold. Thus, you might witness attacks at a scale never seen before.
What’s more, the 5G technology could also lead to botnet attacks, which will spread at a much higher speed than the current networks allow it. Attackers could also use botnets to initiate Distributed-Denial-of-Service attacks.
How can you avoid 5G threats?
With the rapid development of IoT and 5G, It’s crucial for you to evaluate your overall security strategy before your organization starts adopting the 5G technology. As with any emerging technology, 5G will generate new use cases that will need appropriate cybersecurity measures. Thus, it’s mandatory for you to deploy 5G networks with security measures in mind.
Conclusion
Extreme outcomes of security breaches are likely to happen due to 5G security flaws. And they can prove to be both expensive and disastrous. This brings us to the most critical aspect that security experts should begin with, namely the fact that 5G networks must have, first of all, built-in security measures in place. But the first important step will remain to identify the security regulations that the 5G technology truly needs, coupled with strict cybersecurity rules and regulations imposed to 5G network providers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










