Contents:
Hackers leaked 2.7 billion data records containing personal information belonging to citizens of the United States for free, on a dark forum.
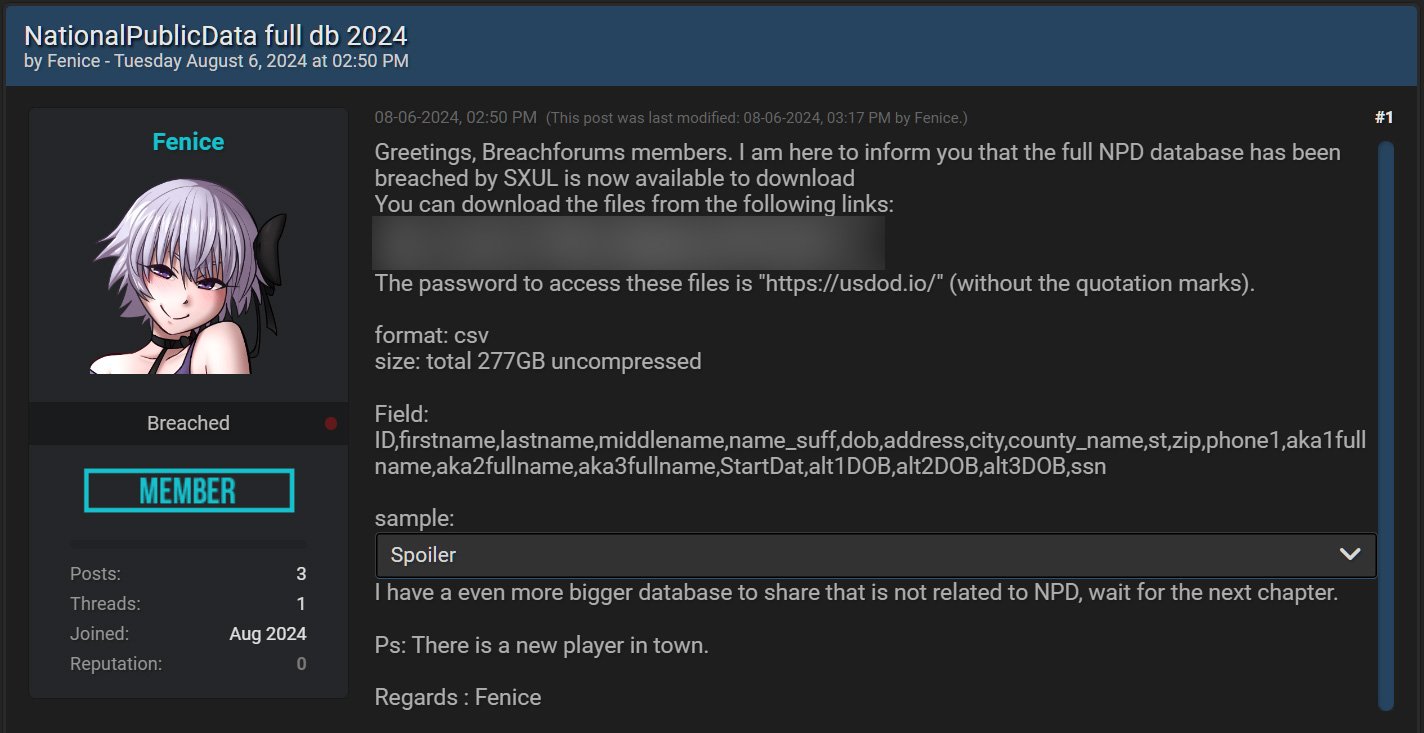
The attackers claim they had exfiltrated the data from the National Public Data.
The type of data in the 2.7 billion leaked data records
The 277GB data leakage revealed two text files that contained around 2.7 billion unencrypted records.
The compromised data are:
- full names
- e-mail addresses
- Social Security numbers
In some cases, the records include other names associated with the person. Regarding the number of US citizens that the data leakage impacted, BleepingComputer.com said:
It is important to note that a person will have multiple records, one for each address they are known to have lived. This also means that this data breach did not impact 3 billion people as has been erroneously reported in many articles that did not properly research the data.
Their journalistic investigation revealed that in some cases, the name, e-mail and SSN don’t match, they belong to different people.
But there is still a risk of fraud, phishing, and smishing attacks. A previously leaked sample also included phone numbers.
Source – BleepingComputer
Why is National Public Data silent
This is not the first time hackers have claimed to have breached National Public Data. A threat actor dubbed USDoD attempted selling 2.9 billion data records of people in US, UK and Canada.
They’ve also claimed stealing the data from National Public Data. BleepingComputer.com said that at that moment they asked NPD for a point of view. Until now, they didn’t get any response.
Security specialists say none of the data was encrypted. Encrypting data both in storage and transit is one of the most important data security best practices.
In case of a data breach, data encryption prevents the attacker from reading and using the files.
If the data leakage is indeed connected to NPD, this means the company had collected and stored sensitive data without complying with one of the most important security measures.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







