Contents:
Researchers revealed that the largely used WordPress plugin ”Gravity Forms” is vulnerable to unauthenticated PHP Object Injection.
The flaw was tracked as CVE-2023-28782 and affects all plugin versions from 2.73 and below. The vendor fixed the vulnerability with the release of version 2.7.4, available for users starting April 11th, 2023. Cybersecurity specialists urge website admins to apply the security update as soon as possible.
Form builder Gravity Forms is used by over 930,000 websites for payment, registration, file upload, and different other forms needed for transactions, feedback, etc. Some of its most famous customers are Airbnb, ESPN, Nike, NASA, PennState, and Unicef.
More about CVE-2023-28782
The cause of the problem seems to be the lack of user-supplied input checks for the ‘maybe_unserialize’ function. If a form was built using the Gravity Forms plugin, submitting data to it might activate the issue.
According to the researchers who discovered the flaw:
Since PHP allows object serialization, an unauthenticated user could pass ad-hoc serialized strings to a vulnerable unserialize call, resulting in an arbitrary PHP object(s) injection into the application scope
Note that this vulnerability could be triggered on a default installation or configuration of the Gravity Forms plugin and only needs a created form that contains a list field.
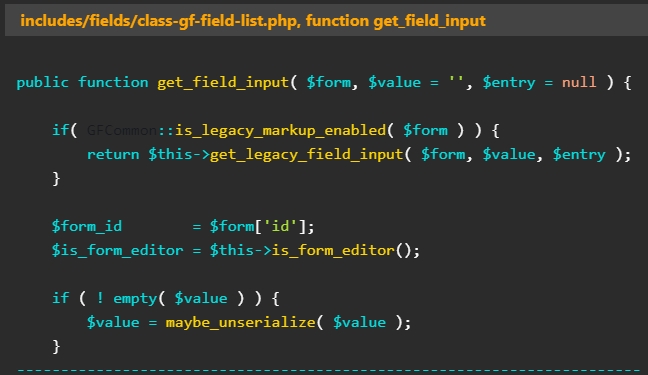
Despite CVE-2023-28782`s potential severity, researchers claim there is no significant property-oriented programming chain in the plugin.
Although this seems to mitigate the risk, the situation could become critical if the user installs other plugins or themes that do contain a POP chain. In that case, CVE-2023-28782 could cause serious damage. Threat actors could exploit the Gravity Forms vulnerability for arbitrary file access and modification, user/member data exfiltration, and code execution.
How to Keep Safe from CVE-2023-28782
Updating the Gravity Forms plugin to version 2.74 should solve the issue. The plugin vendor removed the use of the ‘maybe_unserialize’ function from the new version 2.74. he released.
As a caution measure, cybersecurity specialists recommend website admins keep track and apply available updates across all plugins and themes. This helps eliminate other attack vectors too.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







