Contents:
Is your organization planning to implement a privileged access management (PAM) solution? If you already have passwords, an anti-virus, and a firewall, you might be wondering why you need to implement another cybersecurity technology.
This article will help you understand better what PAM is and why it’s important. You’ll learn about:
- What PAM does
- What PAM looks like
- 5 ways PAM benefits your business
What is PAM?
Privileged access management is a process rather than a specific technology. It describes the way an organization controls, monitors, and secures access to data and critical IT systems.
Each organization is different. Each has a unique approach to security and risk. So, the PAM model will change from one business to the other. But the general principles are the same everywhere.
In most corporate IT systems today, there are users with different ‘privilege’ levels:
General user accounts
These people are only allowed to upload, open, or edit files they have permission to interact with. For example, only salespeople can enter the sales folder. Only HR people can open the HR software, etc.
Privileged accounts
These people have more control over the IT system – they’re often on the IT help desk. Privileged account users might have permission to:
- create new user accounts (i.e. if a new employee joins the company)
- update people’s passwords if they forget them
- install new software on devices
Domain level accounts
These people typically have the most control over the entire IT system. Among other high-level privileges, they can:
- allow or remove privileges for other colleagues
- configure servers
- install workstations
Note that the above is a simplified description – organizations can have multiple layers of privilege levels.
Your organization’s security teams will usually have planned a PAM policy with relevant department heads. This policy will have specified ‘standard’ privileges for different kinds of people. If an employee needs to get access to a folder that they don’t usually open or install some software, they then need to ask an administrator to give them permission to do so.
PAM technology is designed to support these PAM processes. Essentially, it makes it easier, more efficient and more coherent to implement a PAM policy, while also identifying any risky behavior.
PAM and cyber-crime
It is unclear exactly how many cyber-crimes are linked to access management issues. However, in a snap poll during a recent Heimdal webinar, 38% of IT professionals told us they’d experienced a major IT incident due to admin credentials or unauthorized rights elevation at some point in their careers.
Meanwhile, a 2024 report from Verizon estimates that about 10% of all security breaches in the previous year were related to internal privilege misuse by employees. Another significant chunk of breaches will be related to hackers entering company systems and exploiting lax privileges.
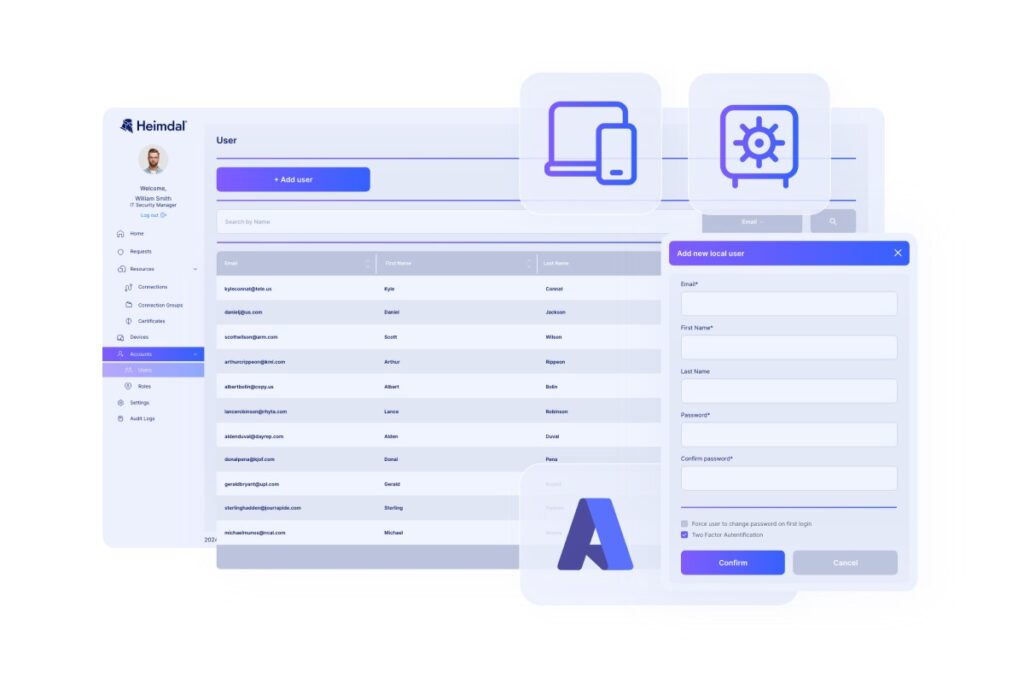
Features of a PAM solution
Privileged access management tools are designed to enforce PAM policies. Best PAM software solutions are flexible and allow you to tailor them to the rules of your organization. You can customize for specific regulations, the number of people you employ, and so on.
Key features of a PAM solution include:
- Real-time session monitoring, including recording
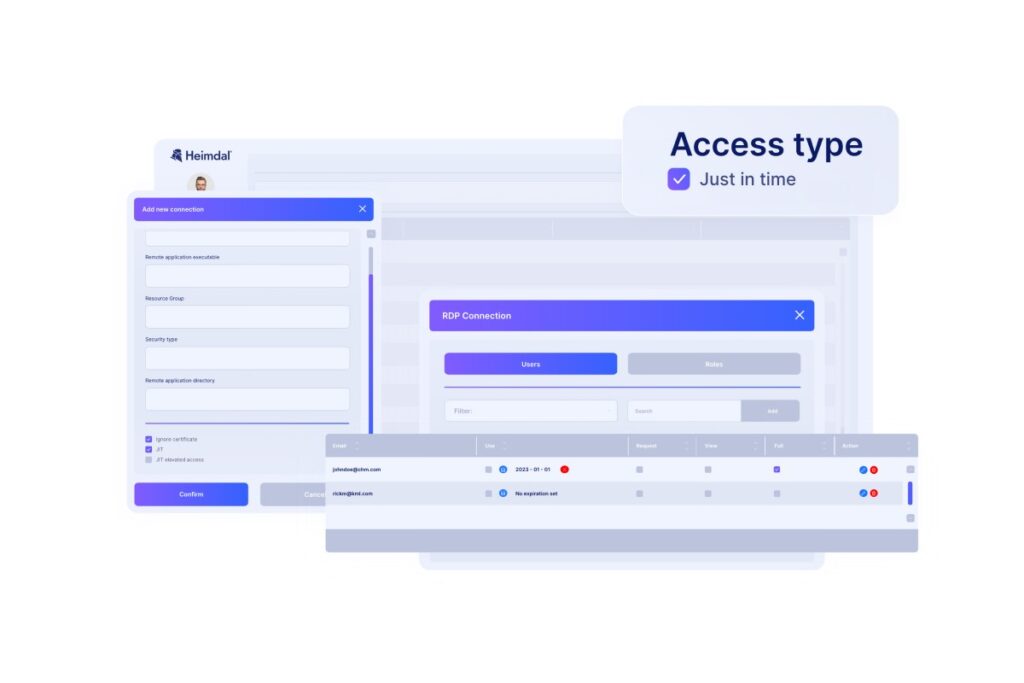
- Just-in-Time session management. Just-in-time access means you give users time-restricted privileges to systems they don’t usually access.
- Credential vaults
- Multi-factor authentication (MFA)
- One-click remote access
- Zero Trust features
- Unified access management
- Application and device control
Hotel key card analogy – understanding PAM
“The principle of least privilege – that’s exactly what you experience when you’re going to a hotel and receive a key card” – Andrei Hinodache, Heimdal.
In a recent webinar, Heimdal’s Cybersecurity Community Leader, Andrei Hinodache, compared PAM to hotel key cards. It’s an analogy that works really well.
Imagine you’ve just checked into a fancy hotel. The receptionist gives you a key card that provides access to your bedroom, the pool area, and the parking garage. In this analogy, the key card is like the basic privileges that a business user has in a company’s IT system. They can only enter the rooms they need access to. They can’t enter other guests’ rooms, the kitchen, or staff rooms. In cybersecurity, this is called the principle of least privilege.
But other people at the hotel have key cards with much greater privileges. The cleaning staff, for instance, can access every single guest room so they can change people’s bed sheets.
But their key cards don’t give them access to the management offices, where financial information is held. Sometimes, one member of the cleaning team might temporarily be given access to the management office for a specific task, but they then have to return the key to their boss.
This is just like PAM. It’s about managing people’s privileges – and includes giving people temporary access from time to time.
To reiterate, privileged access management is about deciding how much access people get and what they can do with it. PAM technology supports those policies.
5 reasons to use PAM solutions
PAM solutions are important because they help enforce your privileged access management policies. While most organizations have rules defining who has access to what, making sure those rules are implemented is very complex.
And that’s where PAM solutions come in. They let you grant or rescind access at the click of a button, monitor activity, and control what people can do while they have elevated privileges.
Here are five of the top reasons to use a PAM solution.
Enhanced security
A PAM solution can – and should – play a role in your organization’s security posture. The technology will enforce your access management policies. This means that, even if there is a bad actor inside your systems, there will be limits to what they can do:
- Zero Trust tools will make it very hard for hackers to perform a lateral movement once they are inside your systems.
- Just-in-Time security features ensure that people are only given access to files or systems for restricted time periods – meaning, for example, that an employee with a grudge can download much less information.
- Activity monitoring reminds people they are being recorded when installing software or opening files – which is a deterrent to bad behavior.
- PAM makes it harder for people to find workarounds for restrictions. If people do begin using workarounds, they can jeopardize the entire system’s security.
PAM tools save time
One of the most common points of friction between the business and IT is around requesting access to files, or permissions to make system changes. Automated PAM tools make the process much faster.
For example, if someone wants to install a software update and doesn’t have the permissions to do so, they typically have to email or call the IT help desk. The help desk may either access their machine via a remote access solution, or temporarily grant the employee privileges (which IT must remember to rescind once the update is complete). This process, however, can be very time consuming – with employees often waiting around until their ticket reaches the front of the queue.
For the individual employee that might be 15 wasted minutes. But multiply that over a large organization with hundreds or thousands of staff making dozens of access requests per week. The scale of the problem becomes enormous.
Again, PAM tools make this so much faster. Permission can be given at the click of a button – or even automatically. User sessions are recorded (ensuring no proscribed activity happens). And any permissions are rescinded as soon as the activity is complete. Thus, you avoid another open gate for cyber attackers – privilege creep.
PAM tools cut ‘hidden’ costs
On a similar note, PAM tools can save organizations enormous sums of money in terms of missed productivity:
- If an employee cannot work because they don’t have access to a file or app, they cannot be productive. They’ll waste time while waiting for permission to be granted.
- Very often, employees who are unable to work will distract those around them – complaining to their colleagues about the delay, suggesting people come for a coffee with them – and other disruptions!
- It takes time for people to get back into the flow of work after having to stop (one study suggests it takes the average person 23 minutes to get back to focus after a disruption).
By providing an almost instant way to approve requests, employees can keep working with much fewer disruptions. And that saves the business money.
Enhanced accountability
Some PAM tools allow organizations to log privileged sessions. Knowing that their activity is being monitored when they’ve been given access to a restricted file or system dissuades people from doing things they’re not supposed to.
Imagine, for instance, that a manager has temporarily been given access to an HR environment so they can download an onboarding document. If they know their screen is being recorded, they’re much less likely to ‘snoop’ on their coworkers’ personal records.
PAM tools underpin compliance
Another major benefit of PAM technology is that it can support compliance with various kinds of legislation. ISO 27001, for example, is an international standard for information security that challenges CISOs and IT administrators worldwide.
These technologies provide solid evidence that you have implemented data management policies and are enforcing them too:
- PAM tools can automatically produce reports demonstrating permissions levels and activity during privileged sessions.
- When people are given additional access, PAM tools can record activity to prove security policies are being followed.
- This recording also supports investigations into breaches.
- The use of Zero Trust and MFA also support various kinds of compliance and show you have followed best practice.
Understand privileged access management
A strong PAM policy – underpinned by PAM technology – can play a key role in boosting your organization’s security. It should reduce the risk of breaches, and help you comply with regulations.
Privileged access management is, ultimately, about good security hygiene and sound business practices. Just as a hotel wouldn’t give the ‘master’ key card to anyone walking in off the street, neither should businesses allow random employees to enter every area of their IT system or install any kind of software they want.
Heimdal’s PAM solutions give organizations a powerful, flexible, and robust suite of tools to enforce their PAM policies. Learn how it works, or contact us for a demo today.
Frequently asked questions
We answer your FAQs about privileged access management.
Who is in charge of PAM?
An IT leader or cybersecurity team will usually be in charge of PAM technology. However, the PAM strategy also requires a lot of input from other business departments. The PAM ‘owner’ will usually work closely with the CISO, the CIO, heads of departments, knowledge management teams, HR, Legal, and other relevant teams who will have a say about the privileged access management system.
How long does it take to roll a PAM solution out?
It depends on your organization’s size and complexity, as well as the granularity of control needed. Simpler PAM technology rollouts can take as little as a couple of weeks. But larger projects can take several months to deploy and fine-tune. Our guide to PAM rollouts can help you plan.
Is PAM technology worth it?
Yes, most organizations would benefit from PAM technology. Rolling it out can be complex. However, the benefits – particularly around productivity, efficiency and security – are significant. A well-planned PAM is far superior to relying on opaque, manual approaches with no accountability.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security