Contents:
In the digital world, security is a top priority. The internet is riddled with hackers, phishers, and other cybercriminals who are always looking for ways to steal data and money and eventually disrupt businesses. Zero trust is an effective way to secure an organization’s network. It is usually implemented through a privileged access management solution.
Read on to find out more about this security model, its principles, its benefits, and how zero trust implementation can help you remain a step ahead of malicious actors.
What Is the Zero Trust Security Model?
Zero Trust is a security architecture that mandates that all users, whether inside or outside an organization’s network, must authenticate and get authorized before accessing any systems or data.
The zero-trust security model runs on the belief that one should “never trust and always verify” which means that applications and data can only be accessed by authenticated and authorized users and devices. In contrast, conventional approaches to privileged access management assume that all users within an organization are trustworthy while users from the outside are unreliable.
The key idea behind applying the zero-trust security framework is to make it more difficult for attackers to move laterally through a network by limiting their access rights as they move from one subnet to another. Context (e.g., user identity and location, endpoint security posture, app or service being requested) is used to establish trust, with policy checks at each stage.
How Does Zero-Trust Work?
The zero-trust security model checks the user’s identity using a combination of technologies, including identity protection, risk-based multi-factor authentication, reliable cloud workload technology, and next-gen endpoint security.
Zero-trust operates under the principle of “never trust, always verify,” thus assuming all connections and endpoints to be potential threats and employing access policies based on context. The context might mean the role and the location of the user or what data they need access to, thus facilitating visibility and control across the traffic and users in the specific environment.
Every connection, for instance, when a user connects to an application or software to a data set via an application programming interface, is verified and authorized by a zero-trust security architecture. The communication between the two should be on the same page with the organization’s enforced security policies.
Zero Trust Security Principles
Much better understood as a security framework, zero trust security embodies many principles that indicate its functionality. Here they are:
Never Trust, Always Verify
The zero-trust model encompasses the “never trust, always verify” notion, which means that no activity or user is intrinsically trusted, as every access request should come with a form of authentication to be approved.
Ongoing Monitoring and Verification
Since the zero trust model concept is based upon the so-called “never trust, always verify” notion, the verification for users and machines identity and privileges is a continuous process of monitoring and validating of who or what has what access, of user behavior, changes in the network or different data alterations or movement.
Nowadays, zero trust encompasses a wider range of data, risk principles, and dynamic risk-based policies to provide a strong foundation for access decisions and ongoing monitoring as it has developed into a much more nuanced strategy.
Zero Trust Based on the Principle of Least Privilege
The zero trust security framework relies upon a very well-known principle, known as the principle of least privilege, or briefly POLP. This concept makes sure that the attack surface is restricted because users are given only the necessary access to complete a specific task and nothing else beyond. To put it simply, an HR employee will not have access to the DevSecOps database for instance.
Control over access extends to devices as well, as zero trust systems must keep track of how many different devices are trying to connect to their network, verify their validity, and assess their status to ensure they do not pose a risk to the network.
A Network That Is Zero Trusted
The zero trust network principle involves discovering your valuable assets and implementing microsegmentation. Through microsegmentation, the network perimeter is divided into small zones called subnets, a good method to implement separate access to different network areas. This successfully prevents a very threatening security issue which is lateral movement of infiltrated malicious actors across the network and it also works on limiting data breaches. An attacker cannot move across the network’s microsegments since zero trust access is segmented and must be re-established on a regular basis.
Security for Workloads
This is another principle of zero trust that says that workloads, especially cloud-based ones, should be properly secured as they serve as potential targets for malicious actors.
Zero Trust Data
The goal of zero trust is to keep data safe while it moves between desktops, mobile devices, application servers, databases, SaaS services, and so on. Thus, data usage controls are put in place once access is granted.
Multi-Factor Authentication
Another essential principle of the zero trust security is multi-factor authentication. Multi-factor authentication is a way to protect your account by requiring more than one form of identification. For example, you may need to enter your password and a code from an app on your phone.
Benefits of the Zero-Trust Model
The benefits of the security model called zero trust include:
Improved Business Security and Reduced Attack Surface
The zero-trust model has been shown to improve security by eliminating potential vulnerabilities in the network. With zero trust implementation, all applications and services are blocked to establish communication before they are verified. Since a zero-trust strategy performs ongoing monitoring, business security is improved, and the attack surface is reduced.
It also supports a lower risk of data breaches, since every authentication is checked to see if it’s trustworthy. This means fewer chances for a hacker to perform data exfiltration.
Besides, zero trust contributes to a clean cybersecurity posture by limiting the risk and detecting much faster malicious attempts like phishing emails, credentials theft, or abuse of privileged accounts like keylogger installation by means of privilege escalation attempts.
It Facilitates Control Over Cloud and Container Environments
When implementing a zero-trust security model, security policies are enabled in accordance with the workloads’ identities. This means that potential at-risk assets will not be impacted by ports, protocols, or IP addresses, since security is strictly correlated with the workload itself, this points out the fact that it will not be impacted if the environment suffers modifications.
Reduced Costs
Since zero trust means fewer data breaches, this also reduces costs as well as the number of necessary security updates.
Faster Response Times Due to Continuous Monitoring
The zero trust model has been shown to improve response times by minimizing the time it takes for detection and containment when there are breaches. Zero trust features a continuous strategy of monitoring and validation, thus facilitating a timely response to signs of compromise.
Helps Your Business Meet Compliance
With zero trust, no user or workload internet connections face the risk of exposure to malicious hackers which also triggers another benefit of the zero-trust model: meeting compliance and helping you provide a spotless audit trail.
It Enhances Visibility into the Network Perimeter
With zero trust you achieve a holistic view of your users, devices, components, and workloads throughout your whole ecosystem.
Traditional Security Architecture vs. Zero Trust Architecture
The difference between traditional security architecture and zero trust architecture is quite straightforward. The first says “trust, but verify”, and the second “never trust, always verify”, basically not even giving the benefit of the doubt to users and devices. Simply put, traditional security assumes that anything within the perimeter can be trusted, relying on firewalls to block what comes from outside. Thus, access is automatically granted to insider users and resources, while the risk posed by “anything” outside the perimeter continues to be the main focus. Zero trust security is quite the opposite, nothing is trusted until verification, be it an insider or an outsider.
The traditional security architecture is often referred to as the perimeter model after the castle-with-moat approach encountered in physical security. Through this model, protection is given by building multiple lines of defenses that attackers must go past before eventually gaining access, while possible insider threats are not taken into account. The traditional network security architecture divides networks into zones within one or more firewalls. In this case, each zone is assigned a certain level of trust, that decides which network resources are allowed to reach. Through this model, high-risk resources (like web servers connected to the public internet) are put into an exclusion zone (oftentimes known as “DMZ” or “demilitarized zone”). Here, traffic can be closely monitored and controlled.
Zero Trust Best Practices
If you wonder what’s the best approach to zero trust security, here are some best practices that might help you:
#1. Know Your Architecture
The first and most important thing you should do is create an inventory of your assets and know everything about every single component of your architecture, including your users, their devices, and the data they are accessing. Furthermore, before moving to a Zero Trust architecture, you need to consider all your existing services since they may not have been designed for the Zero Trust scenario and, therefore, may be unsafe in front of potential attackers.
#2. Create a Single Strong User Identity
Your organization should use a single user directory and know which accounts are connected to which individuals. For granular access control, you should be creating specific roles for each user. This way, in case of an attack, it’s crucial for you to understand exactly which user is responsible, what they are trying to access, and if they do have the necessary permissions to access certain data.
#3. Create a Strong Device Identity
Besides users and accounts, every device owned by your organization should be uniquely identifiable in a single device directory. Moreover, zero trust systems have to monitor what devices are trying to access their network and ensure that every single one is authorized. This practice will further minimize the attack surface of your network.
#4. Authenticate Everywhere
In your zero trust architecture, all connections should require authentication. At the same time, authentication should be stronger than just a username and password. Multi-factor or two-factor authentication is considered to be a core value of Zero Trust. So, besides entering a password, users should be able to provide additional proof that they are who they claim to be, for instance, by submitting a code received on their mobile device as evidence.
#5. Know the Health of Your Devices and Services
To be able to know the health of your devices and services in real time is crucial. You should be asking yourself different questions, such as: Are the latest operating system updates installed? Are the latest software patches applied? Do I have a complete overview of my environment available at all times? Your systems need to be kept up-to-date with the latest patches and you should be able to determine the version and patch level of the services you are using. For instance, a tool like Heimdal Patch & Asset Management can help you automate both Windows and 3rd party software updates.
#6. Focus Your Monitoring on Devices and Services
Given that devices and services are more vulnerable to network attacks than in traditional architectures it’s important that comprehensive monitoring for attacks is carried out.
#7. Set Policies According to the Value of Services or Data
The access policies you set up define the power of your zero trust architecture. This means that your policies should be defined according to the value of the data accessed or taken action.
#8. Control Access to Your Services and Data
You should not be granting your users access to a service unless the request is authorized against a policy. What’s more, always make sure your transmitted data is protected with encryption.
#9. Don’t Trust the Network, Including the Local Network
In order to remove trust from the network, you need to build trust in the devices and services. Do not automatically trust any network between the device and the service it is trying to access, including your local network. Devices should be configured to prevent DNS spoofing, Man in the Middle attacks, unsolicited inbound connections, etc.
#10. Choose Services Designed for Zero Trust
Last but not least, always opt for services specifically designed to support Zero Trust. Keep in mind that legacy services may require additional components to enable Zero Trust, so always make sure you have the resources to handle this.
Brief History of Zero Trust
The “zero trust” concept was coined in 2010 by John Kindervag, a former Forrester analyst. Its architecture allows companies to map out both external and internal security threats and maximize the chances of timely mitigation.
Many of the concepts articulated in zero trust networking, on the other hand, may be traced back to a far earlier idea termed de-perimeterization, which was proposed by the Jericho Forum in 2004. De-perimeterization is a cybersecurity strategy that promotes a segmented and multi-layered security system that relies upon authentication and encryption instead of the traditional protection that separates a network from the internet.
How to Implement Zero Trust with Heimdal®
Following the last recommended best practice, we want to let you know that we have a product that facilitates zero-trust implementation effortlessly: it’s called Privileged Access Management and supports a zero-trust function.
PAM is an automated tool that permits you to escalate and de-escalate user rights, giving you full control and protection over privileged permissions within your organization.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
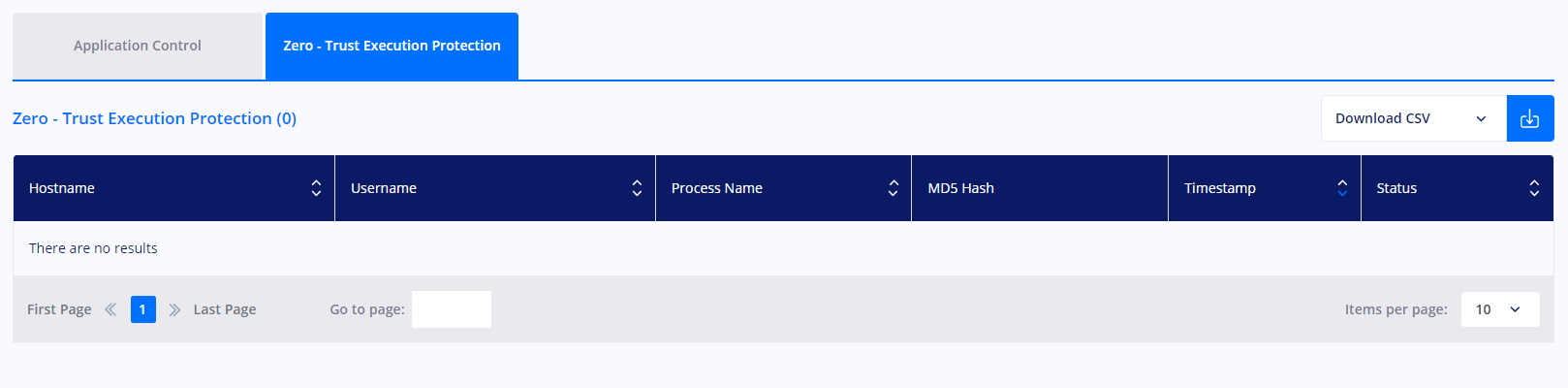
In the Privileges & App Control – Privileged Access Management view, you can find the Zero – Trust Execution Protection display that includes many details like the processes (non-signed executable files) that the zero trust execution protection engine intercepted with data on Hostname, Username, Process Name, MD5 Hash, Timestamp, and Status.
The Zero trust execution process within the Heimdal Privileged and Access Management allows you to safeguard your environment from zero-hour threats (it can be enabled/disabled from the Endpoint Detection -> Next-Gen Antivirus module as well as the Privileges & App Control -> Application Control module).
Conclusion
Zero Trust is quite a new approach to network security and at the same time, it’s also part of a broader philosophy, which implies that you must not automatically trust your network. Instead, you should first think that any connection can potentially be malicious, and only after you’ve verified it, you can be confident that you can trust it. So, consider redesigning and rebuilding your security strategy based on the Zero Trust concept to reduce the chances of breaches and strengthen your defenses.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.
This article was initially written by Bianca Soare in 2019 and updated by Andra Andrioaie and Antonia Din in 2022.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security