Contents:
To understand what targeted ransomware is and to know the difference between opportunistic and targeted ransomware, we first need to kick off this article at the very beginning. What is ransomware?
Ransomware is malware that encrypts a victim’s data and charges them to reaccess it. Then, a ransom is demanded to provide access to the data unless they find a way to get it back on their own. Pretty straightforward, right?
Though ransomware may have initially been designed to spread across a network and target database servers, it’s worth noting that it can quickly become a growing threat to many businesses and organizations.
In addition, it generates billions of dollars in profits for cybercriminals, which has resulted in companies’ significant expenditures of time, equipment, and personnel.
Here’s a little infographic we put together showing you some relevant ransomware statistics for 2021-2022:
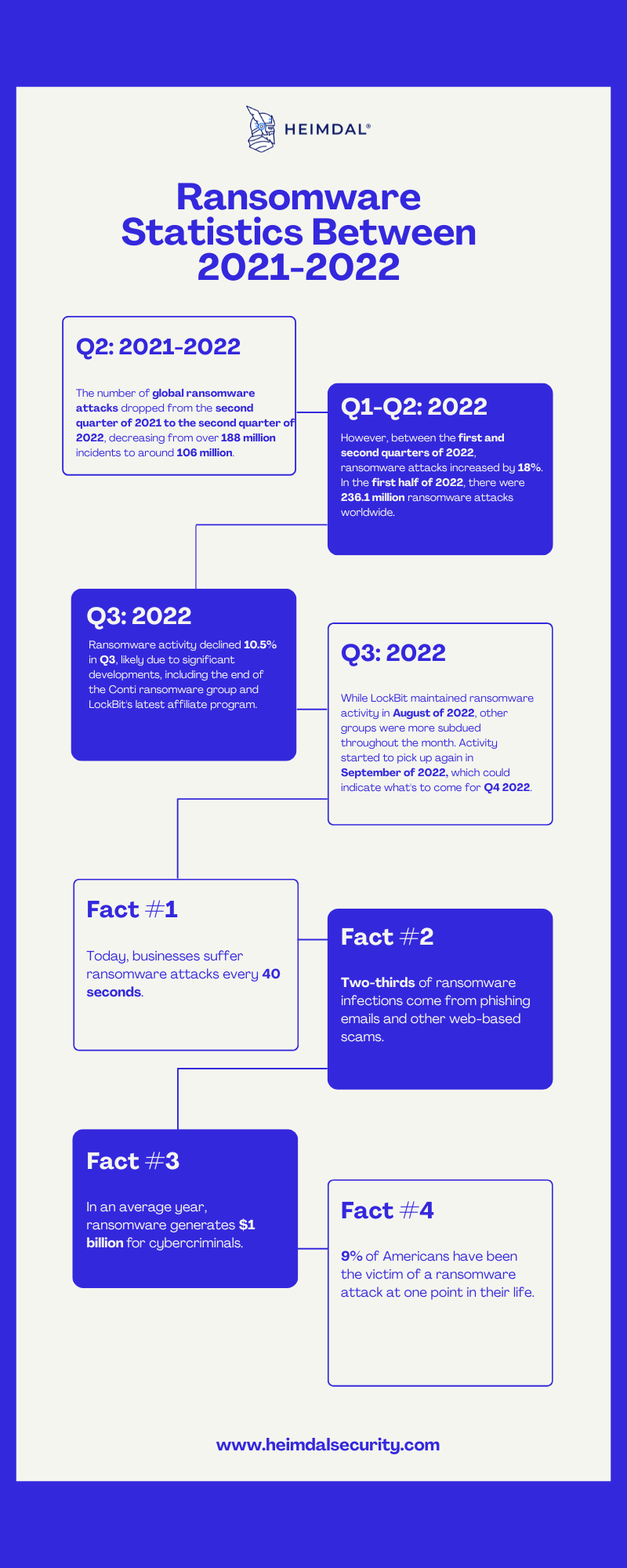
As you can see by the numbers, ransomware has become a preferred means of extortion by opportunistic attackers for two key reasons:
- Firstly, many organizations either don’t practice proper security hygiene when backing up their data or don’t take the right steps when recovering that data if and when it’s lost.
- Secondly, many organizations rely heavily on traditional antivirus solutions, often less effective in blocking ransomware.
These solutions maintain an inventory of known malware samples and stop future executions. But since these solutions must be updated quickly enough to keep up with the mutations created by ransomware developers every minute and subsequent new versions of the malware, protecting against infection is difficult at best.
And in the quest for higher payments, skilled criminals have shifted to targeted ransomware techniques. This is often called “big game hunting.”
So let’s take a look at what targeted malware is more precisely.
What Is Targeted Ransomware?
Since the past few years, more sophisticated ransomware attackers have shifted to targeted ransomware approaches to find organizations willing to pay larger ransoms. These attackers go after particular organizations based on their ability (or need) to pay hefty ransoms, using customized tactics and techniques designed for them.
These attackers are creative, going to great lengths to learn about your victims and exploit vulnerabilities in their systems. They will identify the most valuable data on the victim’s computer and encrypt it, holding it for ransom until they’re paid. These attackers are also very patient and take months or more before deploying ransomware payloads.
The U.S. Department of Homeland Security’s research unit, the 2021 Unit 42 Ransomware Threat Report, has found that attackers often target data backups. If the company can’t restore its files after they’ve been encrypted, it’ll likely be a financial disaster for the organization.
And attackers who do this know very well that they will be compensated for getting in the extra work-they demand $15 million or more in ransom from 2015-2019, with that number increasing to as high as $30 million in 2020.
Recent examples of this long-tail, targeted approach have appeared in ZDNet’s coverage of the Hades ransomware attacks. Hades ransomware operators have successfully breached three multinational profit organizations with annual revenues of over $1 billion. Among them are a transportation company, a retail company, and a manufacturer.
Based on the analysis of the latest Hades ransomware attacks by Accenture’s researchers, threat actors followed a familiar attack path. First, they stole valid credentials from a corporate identity to access company data via Remote Desktop Protocol (RDP) or Virtual Private Network (VPN).
Once inside, they escalated their privileges and moved laterally to establish persistence on the network. Once they had data, they exfiltrated it and deployed the Hades ransomware to encrypt files. Finally, they demanded hefty ransoms as part of a one-two, double extortion punch.
The researchers noted, “We observed significant effort by the threat group to disable or bypass endpoint defenses, including Endpoint Detection and Response (EDR) tooling.”
There are some very troubling things about targeted ransomware attacks. One of these is that just because an organization has been targeted once doesn’t mean it won’t happen again.
To maintain persistence on target networks, attackers often construct backdoors that allow them to reenter at will. As a result, most companies can’t afford to withstand the business impact of one ransomware attack, never mind two.
Why Targeted Ransomware Is So Dangerous
Cybercriminals use targeted ransomware attacks because they know that the organization contains vulnerabilities. If this attack hits a company, it’s highly likely to succeed. Cybersecurity experts state that cybercriminals usually attack companies with an insecure RDP connection.
It’s important to note that this connection escalates privileges and eventually gets administrator controls. This allows them to deactivate security solutions and ultimately infect the system with ransomware.
One significant difference between ransomware attacks and targeted ransomware attacks is that in a typical mass ransomware campaign, the attacker sends out the virus and waits for responses.
However, in targeted ransomware attacks, the attackers are always there: they are responsible for infecting the system, even if they don’t know who their victim will be.
These attacks are an example of live hacking, where the attacker is much more resourceful than traditional security measures and sometimes even manages to get around them.
Why is ransomware so pervasive, and how can these attacks continue to be successful? To answer that, we must first understand how opportunistic and targeted ransomware attacks work.
What Is Opportunistic Ransomware?
Unlike targeted ransomware attacks, opportunistic attacks are meant to be accessible by anyone. For example, they may come through a mass mailing or an exploit kit that targets vulnerabilities on certain websites.
The 2020 Verizon Data Breach Investigations Report found that 86% of all breaches were financially motivated. Attackers know that ransomware is one of the quickest, easiest ways to turn a profit. With do-it-yourself (DIY) kits readily available on the dark web and with low barriers to entry, more attackers are likely to start using this tactic.
Since ransomware is delivered in bulk, attackers can infect many organizations and target as many desktops, laptops, and servers as they want with just one attack. Furthermore, once deployed, ransomware prevents users from accessing their files or systems until the attacker receives a ransom payment — usually in the form of cryptocurrencies like Bitcoin.
2017 was a challenging year for many businesses. One of the most notable examples was the April WannaCry ransomware attack, which infected over 200,000 devices in 150 countries. Although this attack affected many sectors, it impacted healthcare companies the most. Imagine someone’s livelihood being at risk because their emergency medical facility isn’t open for business.
Opportunistic or Targeted, the Initial Attack Vector Remains the Same
Opportunistic or targeted ransomware attacks start and happen on the endpoint. They use desktops, laptops, and servers that are inadequately protected from stealing and encrypting data.
One thing that becomes clear when examining ransomware attacks is that more than relying on one solution for endpoint security is needed.
Instead, we recommend an eyes-wide-open approach to be vulnerable — plenty of organizations are wise to adopt this mentality to reduce the likelihood that their system will be attacked by ransomware.
It’s also important to layer various security controls to reduce gaps, exposure, and overall vulnerability through a defense-in-depth strategy. This means that one plus one can equal three regarding endpoint security.
Heimdal® Privileged Access Management helps prevent malicious attackers and insiders from accessing sensitive data. It also makes it difficult for these entities to harm your business by being able to mask themselves as trustworthy users.
Organizations can minimize risk by managing the privileges on their endpoints by combining endpoint detection and response with anti-virus/NGAV, application patching, OS patching, and privileges management.
With Patch & Asset Management from Heimdal®, you can achieve compliance and mitigate vulnerabilities across your organization. You have the tools to close existing vulnerabilities, deploy patches and updates and install software remotely – on any machine in your organization, anywhere in the world.
An organization can quickly detect ransomware and determine its source by implementing a restriction model that only trusts applications run by specific accounts under specific conditions. By taking this comprehensive approach to endpoint security, businesses can protect against broad and targeted attacks.
Heimdal™ Ransomware Encryption Protection
How Can Heimdal® Protect You From Ransomwares?
Our Ransomware Encryption Protection solution is compatible with any Antivirus and can detect any ransomware without needing signatures or behavioral patterns.
You’ll be able to see the full details of any malicious encryption attempts on your company’s system from its dashboard, including timestamps, diagrams of process callbacks, PowerShell scripts, computed MD5 hashes, and more.
In addition, Heimdal® Email Security is a spam filter and malware protection system that protects your business email software against spam, malware, and ransomware. It can also guard against phishing emails, malicious web links, botnet attacks, email exploits, and more.
All our cybersecurity solutions feature a unified dashboard and agent to ensure exceptional endpoint protection, monitoring, and response. In addition, the enhanced EDR software can help find threats with DNS traffic filtering, automatic security updates, vulnerability management, inventory management, and more.
Wrap Up
Targeted ransomware is an advanced type of malware that can affect organizations of all shapes and sizes. Sadly, the ideal target for hacking is a company without many security measures. A good defense against cybercrime is cybersecurity.
That’s why companies need proactive cybersecurity solutions to defend against attackers’ modern capabilities. Of course, closing every vulnerability is the best way to ensure attackers can’t get into your system.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









