PAM as a Service (PAMaaS) is a subscription-based solution that allows companies to use privileged access management without the hassle of self-implementation or maintenance.
PAMaaS offers all the benefits of a strong PAM program. It supports companies in managing and securing privileged accounts and credentials by outsourcing operational responsibilities to a third-party provider.
Implementing PAM can prove a burden, especially when it comes to infrastructure setup. PAM-as-a-Service saves both time and resources.
What you’ll find in this article:
- What is Pam as a Service (PAMaaS)?
- SaaS vs IaaS vs PAMaaS model.
- PAM vs. PAMaaS.
- Pam in the Cloud vs For the Cloud.
- Benefits of PAM-as-a-Service.
What is Pam as a Service (PAMaaS)?
Unattended pirvileged accounts, users, and assets can be used by hackers to gain access. Learn how to secure them.
Heimdal PAM Suite
PAMaaS is no different from other Security-as-a-Service.
An outsourced model means a third-party vendor provides security solutions to create, manage, and monitor activity on your privileged accounts as part of a cyber security program.
PAMaaS adds an extra layer of protection against security breaches, so you should include it in your defense strategy.
IT Managers can use PAMaaS to apply the privileged access management best practices effectively across the whole organization.
Just like on-premises privileged access management solutions, it helps you to:
- enable privileged rights only to those accounts that need them to do their job
- monitor how those privileges were used
- disable high-level permissions when they’re no longer needed
- keep track and audit regularly the privileged accounts in your company
- set and apply clear procedures and processes for asking and allowing privileged rights to users
The difference is you won’t have to manage additional infrastructure or delegate somebody in your IT team to manage allowing, revoking and monitoring privileges hands-on.
Privileged Access Management as a service frees up the time of your security professionals and goes light on your cyber defense budget.
SaaS vs IaaS vs PAMaaS
A few quick notes about how Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) work:
- SaaS stands for Software-as-a-Service and is a cloud-based software delivery model. The provider hosts the application, and the customer accesses it over the internet. Instead of installing software on each individual device, users interact with it through a web browser or app. Google Workspace and Salesforce are two well-known SaaS examples.
- IaaS stands for Infrastructure-as-a-Service. While it is also a cloud-based platform, it provides virtualized computing resources instead of software services. Instead buying and maintaining the additional physical hardware they need at some point, businesses use IaaS providers to access infrastructure on-demand.
PAMaaS merges all the benefits of SaaS and IaaS into your PAM solution.
It offers a secure, scalable, and easy-to-use system for privileged account management.
PAM vs. PAMaaS for security and business stakeholders
Privileged Access Management is used to track, handle, and control user and privileged accounts.
Some companies prefer the hands-on approach and might have the necessary resources to implement the PAM on premise model.
But, when comparing the two solution types, there are some key differences.
Many security breaches involve a faulty access management.
Cloud native
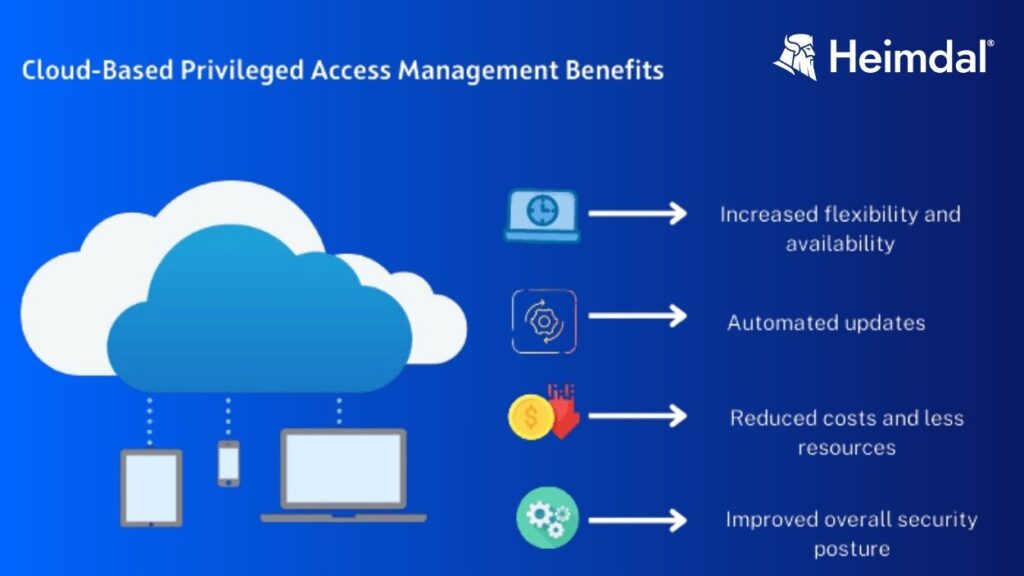
With PAMaaS, the ops move to the cloud rather than being installed on premise. For this to work, a relay referenced on the centralized server is deployed closer to resources.
Once implemented, no extra installation is required.
Financial advantages
Allows for better predictability of costs and spreads them over time.
Increased flexibility
Provides flexibility for external access of privileged users and a guaranteed secure connection. Being cloud-based, it supports scaling better than a traditional PAM solution.
Pam in the Cloud vs. for the Cloud
Another aspect security and business stakeholders must make is the one between PAM in the cloud and PAM for the cloud.
The first one replaces on-premises PAM infrastructure altogether with cloud-based architecture. PAM in the cloud is a PAMaaS component.
Many service providers using a hybrid cloud or multi-cloud service.
PAM for the cloud doesn’t refer to a cloud-based Privileged Access Management solution. It means the solution is used for cloud-based applications.
Benefits of PAM-as-a-Service
Security teams and organizations want to reduce costs and improve computing strength while addressing the issue of insufficient resources.
PAMaaS can also cut down the additional costs incurred by implementing security solutions that are disparate.
This makes managing on-premises infrastructure difficult.
We already mentioned that PAMaaS takes the weight off the infrastructure management.
Let’s quickly go through what else this solution brings to the table.
- Rapid implementation and quick, adaptable risk reduction for your organization.
- A simplified solution for safely storing credentials.
- Isolates and supervises sessions.
- Defend against techniques that enemies use to tap into privileged accounts.
- Helps companies enforce a robust privileged access management program.
Privileged Accounts Management with Heimdal®
PAM is an essential link in cybersecurity for companies and administrations, which must be able to monitor but also trace actions made by privileged users who can impact the security of the system.
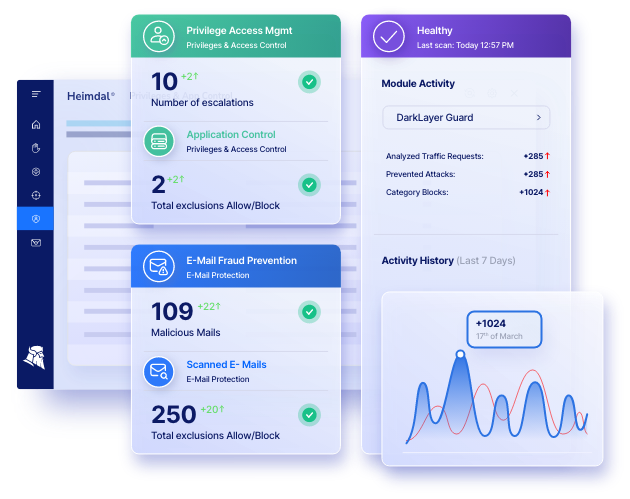
Our Privileged Access Management solution stands out through the following characteristics:
- When used together with our Nex-Gen Antivirus, it becomes the only software that automatically de-escalates user rights, in the event threats are detected on the machine.
- A very smooth approval/denial flow, as well as flexibility when it comes to escalating or deescalating user rights.
- Various characteristics such as AD group rights, escalation period customization, local admin rights removal, session tracking, system files elevation blocking, to name a few.
- Lightweight and stunning interface giving you complete control over the user’s elevated session. Approve or deny from the dashboard or on the go right from your mobile device.
- Advanced data analytics that will help investigate incidents and perform regular security checkups. Obtain graphic-rich reports on hostname details, average escalation duration, users or files escalated, files or processes ran during escalation, and more.
PAM and Application Control
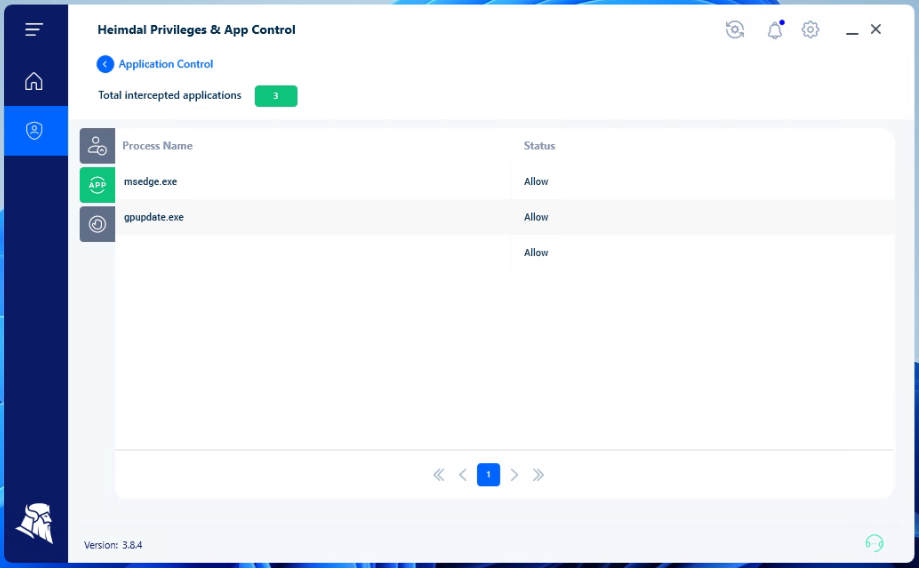
Further, you can add our Application Control module into the mix, and you will be able to perform application execution approval or denial or live session customization to further ensure business safety.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








