Contents:
You might think that you’re taking all security measures to protect your company, but have you ever considered that the danger might come from within? Insider threat is a very serious menace, as many big organizations have discovered on their own.
What Is an Insider Threat?
The term insider threat refers to the threats that organizations face from employees, former employees, business associates, or contractors. These people have access to inside information related to the company’s data, computer systems, security practices, so any fraud, theft or sabotage on their part would hover over the organization’s security.
The malicious insiders’ cybercrimes can include espionage, unauthorized disclosure of information, information technology sabotage, loss or degradation of the organization’s resources.

According to the FBI, the malicious insiders’ motivations can be personal or organizational:
Personal Factors
[…]
Greed or Financial Need: A belief that money can fix anything. Excessive debt or overwhelming expenses.
Anger/Revenge: Disgruntlement to the point of wanting to retaliate against the organization.
Problems at work: A lack of recognition, disagreements with co-workers or managers, dissatisfaction with the job, a pending layoff. […]
Ego/Self-image: An “above the rules” attitude, or desire to repair wounds to their self-esteem. Vulnerability to flattery or the promise of a better job. Often coupled with Anger/Revenge or Adventure/Thrill. […]
Compulsive and destructive behaviour: Drug or alcohol abuse, or other addictive behaviours.
Family problems: Marital conflicts or separation from loved ones.
Organizational Factors
[…]
The availability and ease of acquiring proprietary, classified, or other protected materials. Providing access privileges to those who do not need it.
Proprietary or classified information is not labelled as such or is incorrectly labelled.
The ease that someone may exit the facility (or network system) with proprietary, classified or other protected materials.
Undefined policies regarding working from home on projects of a sensitive or proprietary nature. […]
Employees are not trained on how to properly protect proprietary information.
Types of Insider Threats
When it comes to the usual suspects, the press usually points out two types of insider threats: malicious insiders/turncoats and negligent insiders/pawns.
Malicious insiders deliberately steal data. Whatever their reasons might be, they will exfiltrate valuable data like financial or personally identifiable information through various means. They can create backdoors and install remote network administration tools, install malware or other unauthorized software, disable antivirus software and change passwords etc.
Negligent insiders simply refer to regular employees that make mistakes like sending an email with sensitive information to the wrong person, fall for a clever phishing or spearphishing attack, or lose access to their work accounts or devices.
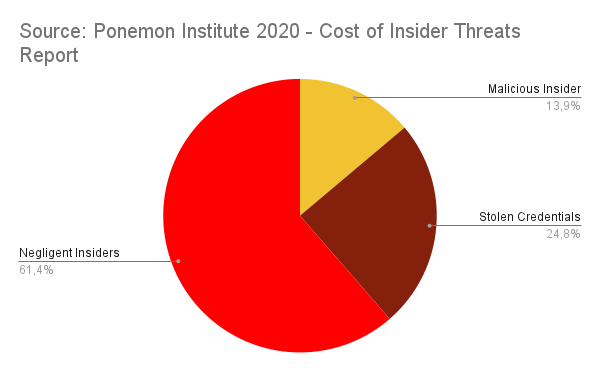
Insider Threat Indicators
As FBI notes, the clues that point to an insider threat are:
Without need or authorization, takes proprietary or another material home via documents, thumb drives, computer disks, or e-mail. Inappropriately seeks or obtains proprietary or classified information on subjects not related to their work duties.
Interest in matters outside the scope of their duties, particularly those of interest to foreign entities or business competitors.
Unnecessarily copies material, especially if it is proprietary or classified.
Remotely accesses the computer network while on vacation, sick leave, or at other odd times. […]
Works odd hours without authorization; notable enthusiasm for overtime work, weekend work, or unusual schedules when clandestine activities could be more easily conducted. […]
Overwhelmed by life crises or career disappointments.
Insider Threat Examples
Sage
The Microsoft data breach happened because, at the beginning of December 2019, the employees misconfigured the security rules of a new version of Azure and the access to the database wasn’t protected with a password or two-factor authentication.
The leaked data didn’t contain any personally identifiable information and Microsoft secured the database as soon as they discovered it and notified the affected users, so the company didn’t suffer any fines or penalties.
Marriott
In January 2020, hackers got access to a third-party application that contained 5.2 million records of Marriott guests. The records included contact information, loyalty account details, personal preferences.
How was this possible? Hackers compromised the credentials of two Marriott employees and managed to log into the third-party application. The suspicious activity was not observed for two months.
The incident was more serious than it was in Microsoft’s case because the stolen data included personally identifiable information. Marriott may face (again) severe penalties.
In July 2020, Twitter also suffered a data breach: hackers got access to 130 private and corporate Twitter accounts that had at least a million followers each. 45 of these accounts were used for the promotion of a Bitcoin scam. Among the notable individuals and companies whose accounts were compromised we mention Barack Obama, Bill Gates, Elon Musk, Apple, Uber.
The incident happened due to a series of spear-phishing attacks. Hackers gathered information on some Twitter employees that worked from home, contacted them and introduced themselves as IT administrators asking for user credentials. The compromised accounts allowed them access to administrative tools, which made possible the reset of the famous users’ accounts.
Twitter users that fell for the scam transferred at least $180.000 in Bitcoin. The incident caused Twitter’s stock price to fall by 4%.
Moreover, one of our former colleagues was the victim of a malicious insider before she even knew what insider threats are.
What happened to Cristina?
Over 10 years ago, Cristina Chipurici ran a music blog that had ten thousand daily visitors. The blog was big, the biggest in Romania in fact, and underpinned a successful business with a team of 10 editors and contributors.
On an April night in 2010, someone broke into her Gmail account. He deleted all of the emails saved on the account and then leveraged it to access three more email addresses. The hacker also ordered a $500 phone using the credit card connected to one of the accounts. But he didn’t stop there. He deleted her blog’s entire database, which contained nearly 5000 posts, and hundreds of thousands of comments.
Several years’ worth of work wiped out in a click. Why? Before Cristina could find out, she had to recover her accounts, one by one. One of her Yahoo Mail accounts still had the original security questions in place before the hack. With these, she was able to recover this account and branched out from it to the others.
After the last Gmail account was back in her hands, she found out who was behind this, since Gmail allows you to see the IP address of the last device used to connect to it. The computer belonged to a former employee. He abused Cristina’s trust to plant a keylogger into her computer, and then all he had to do was to wait for her to type in an account and password, after which he could use them at will.
How to Prevent Insider Threats
Insider threat can cause serious damage to any company but, fortunately, there are various ways through which you can mitigate it:
Protect your most important assets
These assets can be physical, like facilities or people, or logical, like systems or technologies and, of course, customer data. You can achieve this by adopting a good defense in-depth strategy and by making sure you prepare an incident response plan.
When it comes to technology and network, we can also help you. Our offer includes solutions for:
- threat prevention through DNS, HTTP and HTTPS filtering
- vulnerability management with a flexible patch and deployment solution
- endpoint detection and response with a next-gen antivirus
- privileged access management and application control
- email protection and fraud prevention
Enforce Policies
Organizational policies prevent misunderstandings. Make sure that everyone reads the documents and knows exactly what are your security procedures, and their rights in relation to intellectual property. Back up these policies with training.
Monitor and Investigate Any Suspicious or Unusual Activity
You should check any abnormal activity, however harmless it may seem. Remember what the FBI said about copying materials, accessing the systems from unknown locations or at odd hours etc.
Don’t Forget About the Post-Employment Process
You might not be interested in what your former employees will do next, but you will surely be affected if they decide to go rogue. As MHA Consulting says, “You should always ensure that your employee separation process is well documented. Be sure to include the notification and removal process for physical, network, and application access. No matter the reason for the termination, remove access as soon as the individual is no longer with the organization. You should do this within the same day.”
A Word from Our CEO
September is National Insider Threat Awareness Month, but business owners must always keep insider threat in mind. Every single business owner risks the smashing consequences of a security incident, and only in 2020 the cost of employee negligence reached more than $300000, while the cost of credential theft incidents soared beyond $870000. I’m sure remote work will drive insider threat risks up further in the following years, so it’s crucial to stick to all the recommended prevention measures and, most importantly, make sure you protect your company by installing a powerful Privileged Access Management solution, with Zero-Trust at its core, that strictly controls who has access to what. The security and progress of your company depend on it.
– Morten Kjaersgaard –

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Wrapping Up
Whether they know it or not, people are the weakest link in your network security. Whether they intend it or not, they might cause serious problems to any company. Stay vigilant and keep in mind that mitigating insider threats is an essential part of any cybersecurity strategy.
Also, don’t forget to drop a line below if you have any comments, questions or suggestions for us – we are all ears and can’t wait to hear your opinion!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








