Contents:
Attribute-Based Access Control (ABAC), sometimes referred to as Policy-Based Access Control (PBAC) or Claims-Based Access Control (CBAC), is an identity management-related authentication and authorization system that determines user access based on attributes (or characteristics) rather than roles.
The attributes associated with subjects (requesters), objects to be accessed, and others have a set of related characteristics, such as location, time of creation, access privileges, and so on.
Attribute-based access control (ABAC) has surfaced as the next-generation technology for securing access to sensitive corporate data. The Role-Based Access Control (RBAC) approach’s shortcomings have been exposed by the complexities of today’s digital environment, encompassing cloud services, data repositories, mobile, IoT, and others, leaving enterprises open to data security threats.
You might remember RBAC from my previous article. I bring Role-Based Access Control up because it is strongly related to the topic I will be covering today. Unlike this technology, which determines roles that have a particular set of permissions associated with them and to which subjects are allocated, ABAC can define elaborate rule sets that can evaluate multiple distinctive characteristics.
ABAC’s primary goal is to ensure that objects, including sensitive data, network infrastructure, and IT resources, are protected against unauthorized users and activities, namely, those that don’t meet the criteria for “approved” attributes as set out by a company’s security policies.
How Does Attribute-Based Access Control Work? Key Components
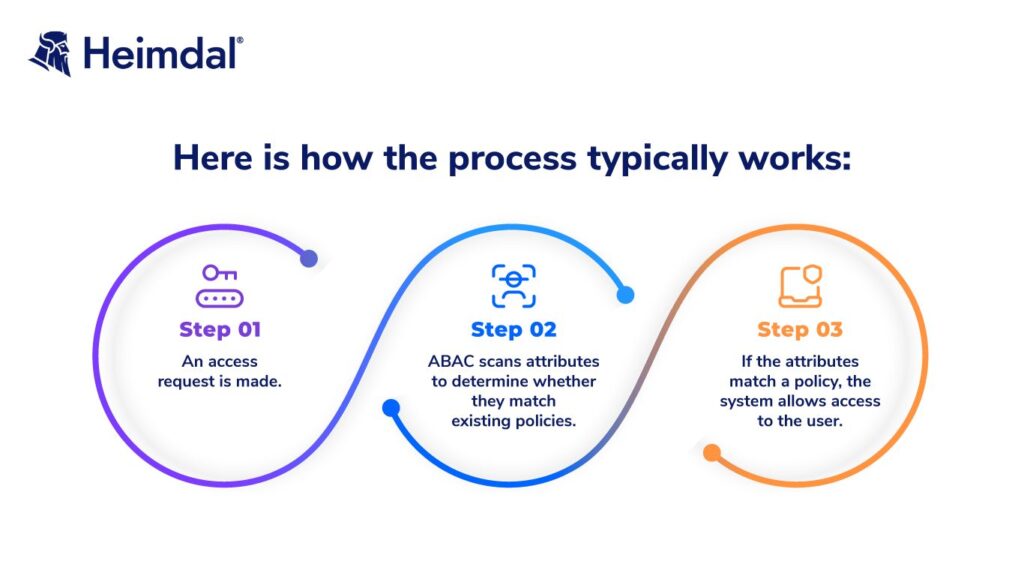
ABAC systems determine access by:
- Intelligently analyzing how attributes interact in an environment.
- Creating a set of rules to determine which attributes are eligible for access based on whether certain requirements are met.
Attributes can refer to anything and anyone. They can be broken up into four major categories: subject attributes, action attributes, object attributes, and contextual (environment) attributes.
Subject/user attributes
Are attributes that describe a user attempting to obtain access to a resource in order to perform an action. Examples can include username, age, job title, user ID, department/company affiliation, security clearance, etc.
Action attributes
Are attributes that indicate the action a user wants to perform regarding a resource. Some common action attributes in authorization requests are:
- read
- transfer
- delete
- view
- approve
In more complex scenarios, the action may be described by a combination of characteristics.
Object/resources attributes
Those attributes that indicate the object (or resource) such as a file, application, or server, requested for access. All identifying characteristics of a file, such as its creation date, ownership, file name and type, and data sensitivity, are considered resource attributes.
Environment attributes
Are attributes that indicate the context in which access is requested. Common environment characteristics include the time and place from where access is required, and the type of communication or device type (PC, smartphone, etc.).
Context (environment) attributes can be of any type that is relevant to consider in order to reduce threats or plan precautionary measures: the number of transactions already made in the past 24 hours, normal user behavior patterns, relations with a third party, and so on.
ABAC Pros
An ABAC authorization model has a lot of advantages that can improve security for your company.
Increased security and privacy
As we learned today, in contrast with RBAC, which allows access in accordance with roles, ABAC permits access based on attributes, allowing for a more targeted approach to information security. The fact that ABAC takes into consideration numerous factors while allowing access offers an additional layer of protection that RBAC cannot.
Granular and flexible policy-making
The main advantage of ABAC is its flexibility. Basically, the limit for policy-making is defined by the attributes that must be considered and the circumstances that the computational language can convey. Attribute-based access control enables the maximum number of subjects to have access to the maximum number of resources without needing administrators to define relationships between each subject and object.
These attributes and access control policies can be adjusted by admins to meet the demands of their company. For example, they can define new access controls for external subjects such as suppliers and contractors without having to manually modify each subject-object relationship. The ABAC model permits multiple access scenarios with minimum administrative supervision.
Compatibility with new users
Using ABAC, administrators can define policies that allow new subjects to access objects. Existing rules or object characteristics don’t need to be changed as long as new subjects are given the necessary attributes to access the resources.
Regulatory compliance
Any company that gathers private information must safeguard it. GDPR, HIPPA, and other legislations make it crucial to protect Personally Identifiable Information (PII). Securing it based on a person’s role will not provide an adequate level of protection. The data must be kept under the tightest security measures while yet being accessible to the users and applications that require it. For instance, doctors require access to patient information, but they can’t use it on their phones while waiting in an airport. It’s important that they are in a safe environment.
ABAC Cons
When it comes to ABAC, the advantages definitely exceed the disadvantages. As with everything, organizations should be aware of the shortcomings before deploying attribute-based access control:
- Recovering from a botched ABAC deployment can be a difficult process that takes a lot of time.
- It can be challenging to control ABAC policies’ updating and visibility.
- ABAC is simple to scale and integrate into your data security program once it has been deployed. Unfortunately, designing and implementing it is quite complicated. Admins have to define attributes manually, allocate them to every component, and establish a central policy engine that decides what characteristics can do based on certain conditions. It can take a lot of time and resources.
However, a successful ABAC deployment may turn out to be a financially sustainable and long-term investment.
ABAC vs RBAC
Authentication and authorization are some of the most important components of online security. Both attribute-based access control (ABAC) and role-based access control (RBAC) can be used to manage the authentication process and user authorization.
As I mentioned before, RBAC and ABAC differ in that RBAC grants access to resources or data based on user roles, whereas ABAC grants access privileges depending on user, environment, actions, or resource characteristics. In essence, when discussing RBAC vs. ABAC, RBAC manages broad access across an enterprise, while ABAC adopts a fine-grain strategy.
Which One Is Best for You?
The choice between RBAC and ABAC is determined by the needs of the company.
RBAC offers a rather straightforward approach to determining authorization. ABAC, which evolved from RBAC, provides a more thorough approach to authorization required to stop unauthorized access. ABAC offers a more sophisticated and comprehensive authorization system that takes into account a considerably larger number of factors, but it also takes more time and resources.
For small and medium-sized businesses, Role-Based Access Control is a less complex alternative to Attribute-Based Access Control. Each user is given a unique role, with corresponding permissions and limitations. When a user changes positions, their permissions are updated to reflect the new role. This means that in hierarchies with clearly defined responsibilities, managing a limited number of both internal and external users is simple.
However, it is inefficient for big enterprises when new roles must be manually defined. Once attributes and rules are established, ABAC’s policies are easier to implement (even if there are numerous users and partners) while also minimizing security threats.
In conclusion, small and medium-sized enterprises with broad access control policies, a few users, and clearly defined organizational roles should opt for the simple solution: Role-Based Access Control.
However, if we’re talking about large companies with lots of users, companies that need to ensure privacy and security compliance and want customized access control features, they ought to choose Attribute-Based Access Control.
It is essential that companies choose suitable authorization solutions that are customized to their needs so that the authorization process is neither overly simple nor too complicated.
Conclusion: Access Control Solutions Are Vital
When it comes to security, it’s critical to thoroughly plan and keep an eye on your access control processes. Use a powerful access management solution to help you set up your access control and review it regularly to ensure it still fits your company’s needs. It’s important that the technology you employ can set up a protocol and procedure to ensure that users only have access to what they need to do their jobs.
How Can Heimdal® Help Businesses?
Heimdal® Privileged Access Management allows administrators to manage user permissions easily. Your system admins will be able to approve or deny user requests from anywhere or set up an automated flow from the centralized dashboard. Furthermore, Heimdal Privileged Access Management is the only PAM solution on the market that automatically de-escalates on threat detection.
Managing user permissions and their access levels is not only a matter of saving the time of your employees but a crucial cybersecurity infrastructure project.
Heimdal® Privileged Access
Management
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









