Contents:
Dubbed FreakOut, Necro, or N3Cr0m0rPh, the malware is an obfuscated Python script designed to evade detection using a polymorphic engine and a user-mode rootkit that hides malicious files dropped on compromised systems.
CheckPoint researchers, who discovered FreakOut in January, noted that the malware spreads itself by exploiting a wide range of OS. The goal behind the attacks was to create an IRC botnet, which can later be used for several purposes, such as DDoS attacks or crypto-mining.
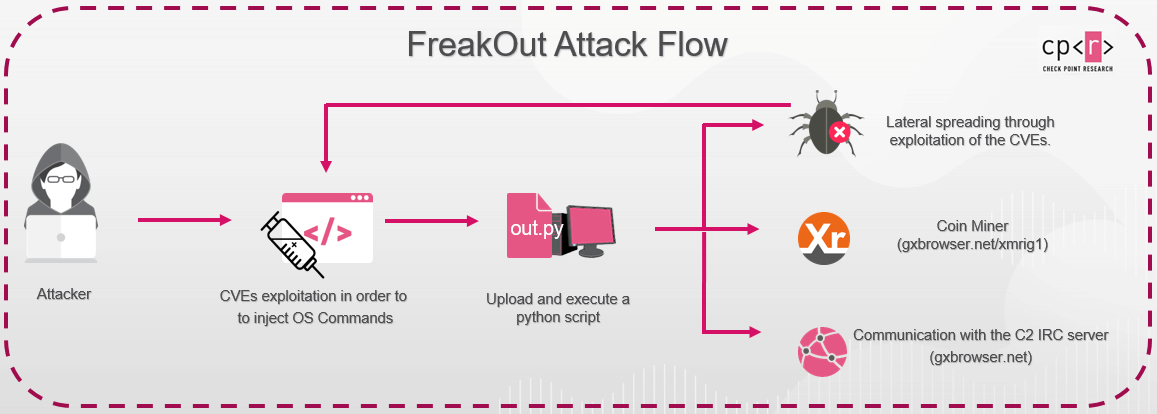
Image Source: CheckPoint
As detailed in a report published by Cisco Talos, FreakOut’s developers have been improving the malware’s spreading capabilities since early May, when the botnet’s activity has suddenly increased.
Although the bot was originally discovered earlier this year, the latest activity shows numerous changes to the bot, ranging from different command and control (C2) communications and the addition of new exploits for spreading, most notably vulnerabilities in VMWare vSphere, SCO OpenServer, Vesta Control Panel and SMB-based exploits that were not present in the earlier iterations of the code.
According to the researchers, FreakOut bots are now scanning for new systems to target by randomly generating network ranges or on its masters’ commands sent over IRC via the command-and-control server.
“For each IP address in the scan list, the bot will try to use one of the built-in exploits or log in using a hardcoded list of SSH credentials”, writes BleepingComputer.
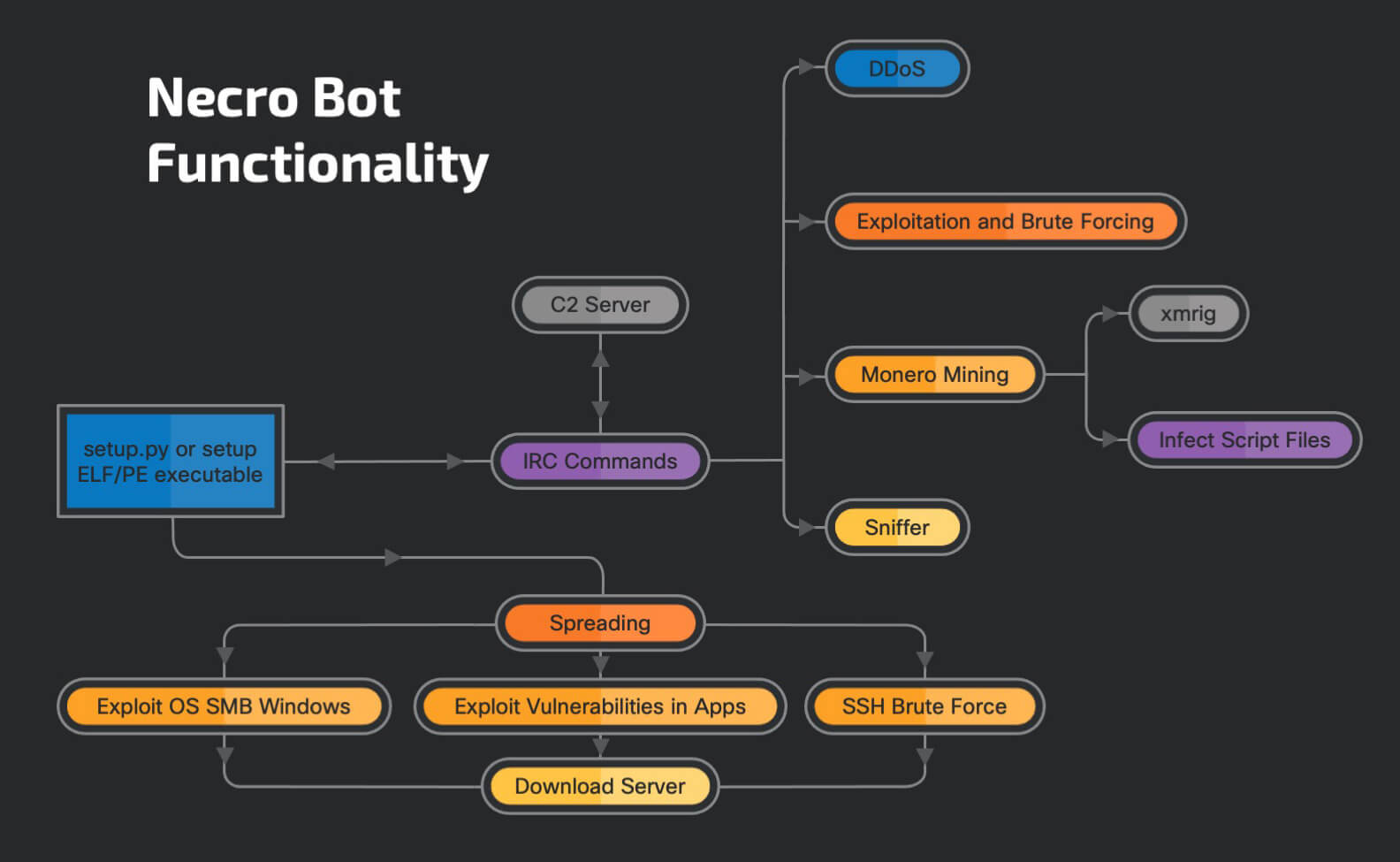
Image Source: Cisco Talos
The latest variants, observed on May 11 and 18 include additional exploits in its arsenal:
- VestaCP— VestaCP 0.9.8 – ‘v_sftp_licence’ Command Injection;
- ZeroShell 3.9.0 — ‘cgi-bin/kerbynet’ Remote Root Command Injection;
- SCO Openserver 5.0.7 — ‘outputform’ Command Injection;
- Genexis PLATINUM 4410 2.1 P4410-V2-1.28 — Remote Command Execution vulnerability;
- OTRS 6.0.1— Remote Command Execution vulnerability;
- VMWare vCenter — Remote Command Execution vulnerability;
- php remote code execution exploit for an unknown app.
VMware flaws have also been exploited in the past in ransomware attacks targeting enterprise networks. FreakOut operators have also been seen deploying a custom ransomware strain, which means that they are constantly testing new malicious payloads.
Multiple ransomware groups, including Darkside, RansomExx, and Babuk Locker have exploited VMWare ESXi pre-auth RCE bugs to encrypt virtual hard disks used as centralized enterprise storage space.
Necro Python bot shows an actor that follows the latest development in remote command execution exploits on various web applications and includes the new exploits into the bot. This increases its chances of spreading and infecting systems. Users need to make sure to regularly apply the latest security updates to all of the applications, not just operating systems.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










