What Is Vulnerability Prioritization?
Vulnerability prioritization is the process of identifying and ranking vulnerabilities based on the potential impact on the business, ease of exploitability, and other contextual factors.
It represents one of the key steps in the vulnerability management process, as it sets the foundation for the next steps of the process.
Its goal is to address high-risk vulnerabilities first and tackle lower-risk ones later.
The Importance of Vulnerability Prioritization
The Cybersecurity and Infrastructure Security Agency (CISA), states that threat actors can exploit vulnerabilities within 15 days of discovery.
Thus, it is essential to tackle the vulnerabilities as soon as possible for effective protection against cyberattacks.
Having clear guidelines on how to prioritize vulnerabilities is crucial.
Without prioritization, organizations may waste time and resources on low-risk vulnerabilities while neglecting high-risk ones.
Vulnerability prioritization helps your company to:
- Reduce the exploitable attack surface and minimize the risk of data breaches, service disruptions, compliance violations, etc.;
- Align your security strategy to your business goals and objectives;
- Effectively allocate your security budget;
- Build trust with remediation and service owners.
How to Prioritize Vulnerabilities?
Organizations should use a risk-based vulnerability management strategy that ranks vulnerabilities by severity, exploitability, impact, and business context.
Here is how you can prioritize vulnerabilities efficiently in four steps:
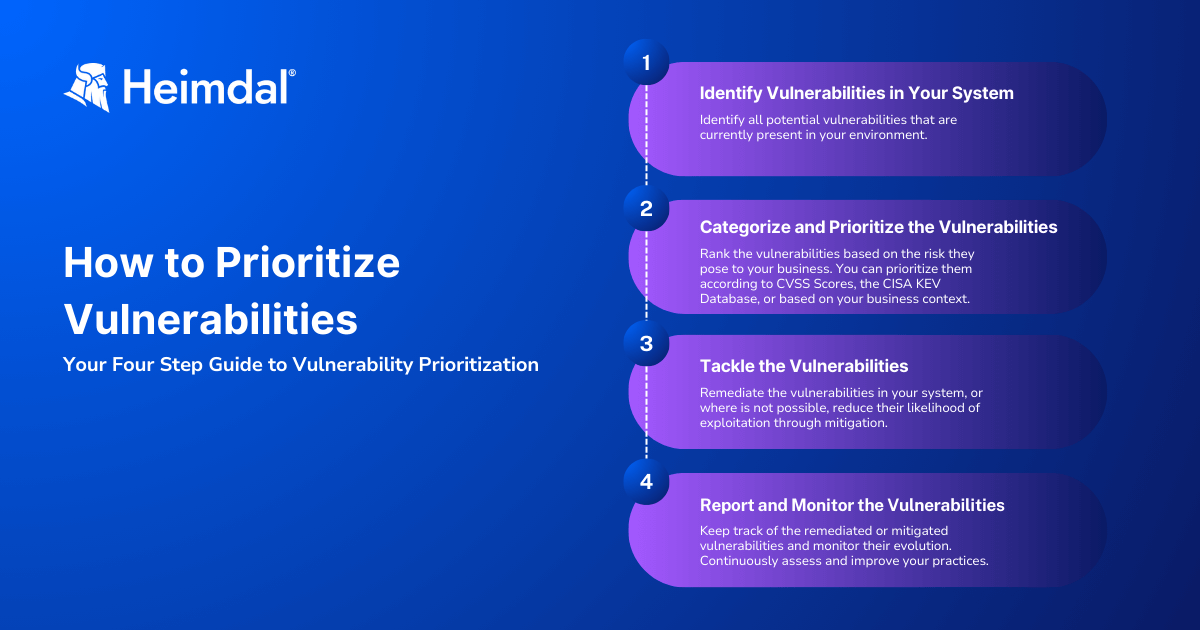
Step 1: Identify Your System’s Vulnerabilities
First, find all potential vulnerabilities in your environment. This step is crucial for understanding the threats you face. We recommend automating this process to simplify it.
Step 2: Categorize and Prioritize Vulnerabilities
After identifying the vulnerabilities, categorize and rank them. Here are a few methods:
- Option 1: Prioritize with CVSS Scores
The Common Vulnerability Scoring System (CVSS) rates the severity of vulnerabilities from 0 to 10. Infosec teams use these scores to prioritize fixes.
Yet, CVSS scores do not account for the specific risks vulnerabilities pose to your environment.
Combine these with EPSS scores, which predict exploitability.
- Option 2: Use the CISA KEV Database
The Cybersecurity and Infrastructure Security Agency (CISA) maintains a catalog of exploited vulnerabilities.
Known as KEV, this database helps organizations focus on vulnerabilities that actively threaten their operations.
- Option 3: Consider Your Business Context
Every organization has unique priorities and risk tolerances. Prioritize vulnerabilities based on your business needs by:
- Identifying your goals and risk tolerance.
- Assessing the importance of your assets.
- Including contextual information.
- Developing a risk-based management program.
Step 3: Address the Vulnerabilities
After evaluating and prioritizing, address the vulnerabilities. You have two options:
Remediation: Fix the vulnerabilities by patching, closing ports, or other methods. Most organizations choose this option when possible.
Mitigation: If immediate remediation isn’t feasible, mitigate the vulnerability to reduce its exploitability until full remediation is possible.
Step 4: Report and Monitor Vulnerabilities
Track the vulnerabilities you’ve addressed and monitor their evolution. Continuously assess the effectiveness of your vulnerability management program to improve risk management.
How Can Heimdal® Help?
Managing vulnerabilities is a full-time task. Relying solely on manual processes can be inefficient and stressful for your IT team. Automating with Heimdal®’s Patch & Asset Management solution can:
- Patch various systems and applications.
- Create inventories of software and assets.
- Ensure compliance with detailed, automatic reports.
- Manage vulnerabilities and risks effectively.
- Deploy updates globally or locally, at any time.
Customize our hyper-automated tool to meet your organization’s specific needs.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








