Contents:
VoIP telephony provider Telnyx recently revealed it had been impacted by a Distributed Denial-of-Service (DDoS) attack that affected its telephony services all over the world.
To carry out DDoS attacks, threat actors overwhelm servers, portals, and gateways with more requests than can be managed by a server or a network, essentially rendering the targeted devices inaccessible to anyone else.
What Is Telnyx?
Telnyx is a Voice over Internet Protocol (VoIP) organization that provides telephony services online across the globe, including in the U.S., APAC, Australia, and EMEA regions.
The DDoS attack occurred on November 9th and since then the company started experiencing issues with its telephony services.
Telnyx is currently experiencing a DDoS attack. Until we reach a resolution, you may be experiencing failed calls, API and portal latency/time outs, and/or delayed or failed messages.
Given the extent of the attack, the VoIP telephony provider started moving its operations to Cloudflare Magic Transit, which provides DDoS protection for service providers, in order to continue fortifying its DDoS mitigation systems.
Magic Transit delivers its connectivity, security, and performance benefits by serving as the “front door” to your IP network. This means it accepts IP packets destined for your network, processes them, and then outputs them to your origin infrastructure.
DDoS Attacks Aimed at VoIP Providers
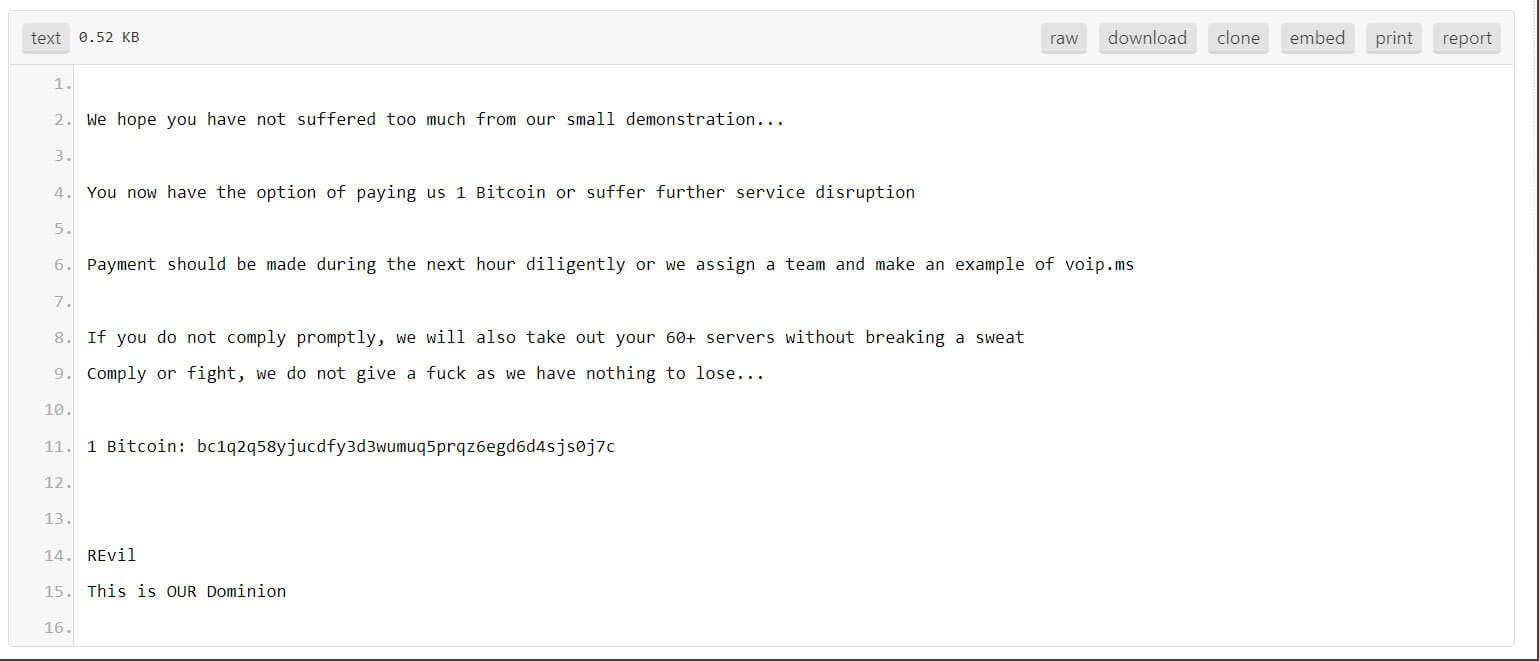
In September 2021, we reported that VoIP.ms suffered a week-long DDoS attack that managed to take down almost all of their services and portals, leaving their customers without voice services.
This attack was an extortion DDoS attack in which the threat actors impersonating the ransomware group ‘REvil‘ initially demanded one bitcoin ($45,000) to halt their attacks but later increased it to 100 bitcoins ($4.5 million).
The attacker’s next victim was VoIP services company Bandwidth that experienced the same issues as VoIP.ms.
The CEO of Bandwidth suggested that the operators behind the attack asked for a ransom, but the company refused to pay it.
We did not pay a ransom and instead relied on innovative solutions and strategies to confront the threat, head-on. To sum up, we believe, Bandwidth is now stronger than ever and we plan to leverage what we’ve learned to help make the ecosystem safer for enterprise communications.
Both Bandwidth and VoIP.ms moved their infrastructure to Cloudflare Magic Transit in an attempt to lessen DDoS attacks. Bandwidth CEO David Morken even declared that these attacks taught Cloudflare how to mitigate attacks against VoIP providers.
We rallied during this attack and used vendors like Cloudflare and taught them how to address this issue for the first time and collaborated with them in a way that they then were able to go to the whole industry and share.
Unfortunately, because VoIP services are frequently routed over the Internet and necessitate public access to servers and endpoints, they become perfect candidates for DDoS extortion attacks.
How Can Heimdal Help?
Protect yourself from DDoS attacks with Heimdal Threat Prevention, the solution that allows you to easily leverage a Host-Based Intrusion Prevention System (HIPS), augmented by a highly intelligent threat detection technology powered by AI.
The innovative AI will detect and block the infected domains, allowing you to enjoy peace of mind when thinking about your business ecosystem.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security