Contents:
Managing hundreds of laptops, smartphones, and IoT devices is no easy task – especially with remote work on the rise. The best Unified Endpoint Management (UEM) software turns chaos into control.
By bringing endpoint management into a single platform, UEM simplifies IT operations, boosts security, and keeps devices up to date effortlessly. Whether you’re dealing with device sprawl or striving for compliance, these tools are a lifeline for modern IT teams and MSPs.
In this article, I break down the key features of UEM software and curate a list of the 10 best UEM software options.
Key takeaways
- Best Unified Endpoint Management software helps streamline maintenance and security processes
- Integration, automation, and unification are the most important features a UEM software should have
- Using a UEM tool helps safeguard Bring Your Own Device work environments and supports implementing BYOD policies
- Not all UEM solutions offer the same capabilities. Although it’s not a traditional UEM, Heimdal’s XDR is currently the most extensive security platform on the market. It also offers a modular approach.
Unified Endpoint Management key features & capabilities
UEM is like a superhero tool for IT teams. It helps businesses control and manage all their devices — computers, phones, tablets, smartwatches, and even gadgets like IoT sensors — from a single platform.
Think of it as a single dashboard where IT teams can see everything happening with the company’s devices.
Whether it’s a Windows computer, an iPhone, or a smart fridge in the office, UEM tools help businesses track, secure, update and configure them.
Modern UEM tools do even more:
- Gathering data about the device’s performance and the way they’re used
- Connecting with PAM tools to make sure only the right people access sensitive information.
- Managing devices regardless of them being on-premises or remote, like a rugged tablet for fieldwork or other mobile tech.
In short, UEM is like a control center that makes managing lots of different devices simpler, smarter, and safer.
Here are some of the key UEM features:
Centralized management of all endpoints
Centralized management makes it easier to monitor, update, and fix devices. Switching between different tools takes time and might lead to overlooking a potential issue. Using a single management console to check on all devices and processes increases visibility. It enables IT teams to react quickly and to the point in case of a security incident.
Combines traditional and mobile management
UEM combines two powerful tools:
- Traditional endpoint security management for devices like desktops and printers.
- Mobile device management (MDM) for smartphones, laptops, and tablets.
Thus, best UEM software ensures all devices follow the same security rules and work smoothly together.
Automated patch management
Think of software updates as shields that protect devices from hackers. UEM tools automatically find and install updates and patches on all devices, regardless of their location. A multinational company will be able to solve all endpoint security and maintenance tasks without creating an IT department for each location. All patching can happen remotely.
Automated application control
Not all apps are safe or necessary. UEM makes it easy to allow only trusted apps on devices and block potentially harmful ones. This ensures employees only use the right tools which keeps devices safe.
Here’s a scenario where using automated application control can save the day.
Employee clicks on phishing link.
Identifying phishing emails got even harder after hackers started using AI to write grammatical errors-free phishing messages. Jack from Marketing might have done well at the last cybersecurity awareness test. Yet, an email that looks like a newsletter presenting a free, new background remover tool could catch him off guard. He clicks the link and deploys the malware.
An application allowlisting function in your app control tool should immediately recognize and block the unapproved software.
By offering all these features and capabilities, UEM tools enable you to:
- save time
- improve security
- manage technology with less effort and stress
Top 10 Unified Endpoint Management software
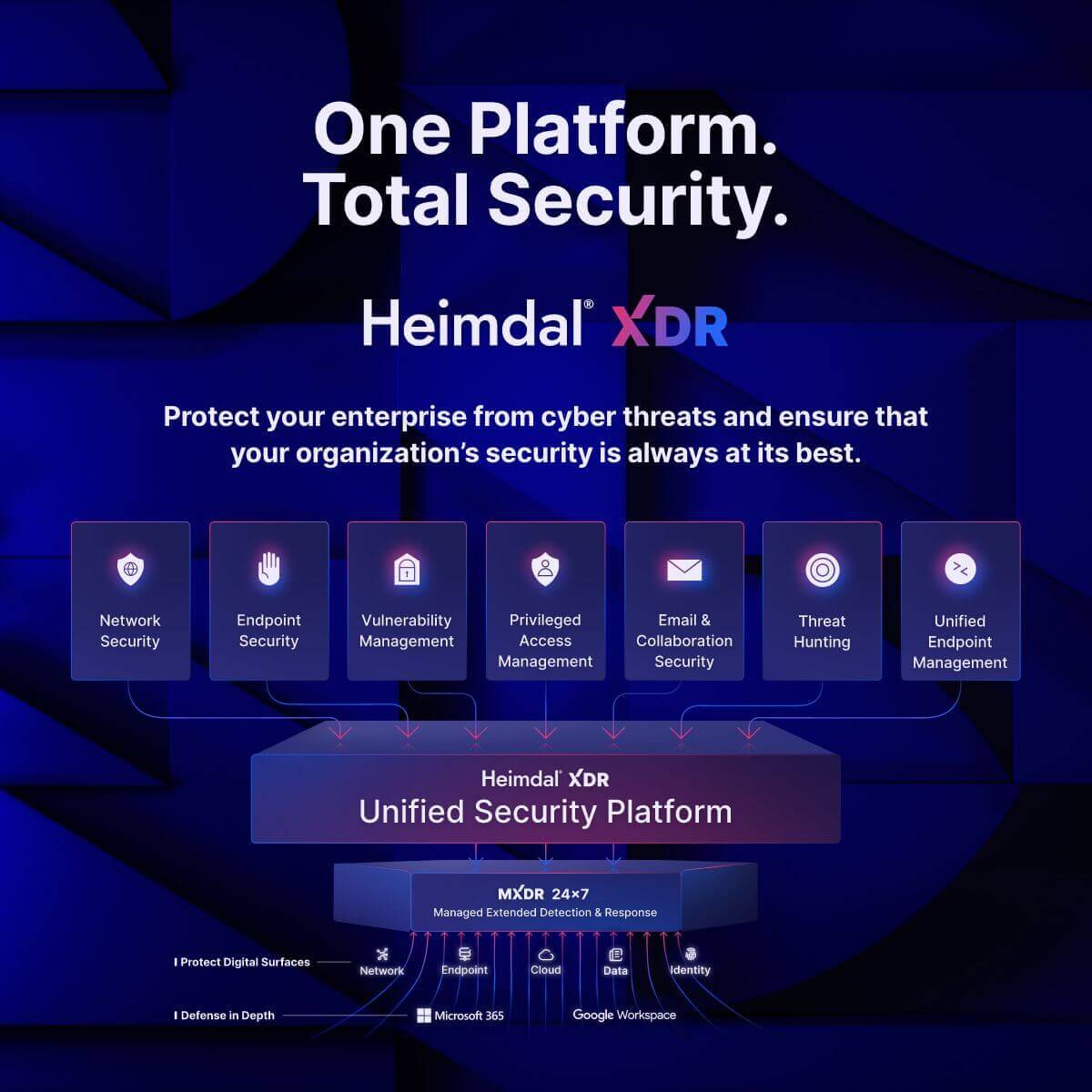
Heimdal’s XDR platform
Heimdal’s XDR is not what most of us call a UEM. Yet it enables you to manage and protect your endpoints with multiple security layers. Having several tools into one kit reduces costs and supports you to stay one step ahead of hackers.
Heimdal’s XDR easy-to-use dashboard helps IT teams and MSPs to focus on the bigger picture.
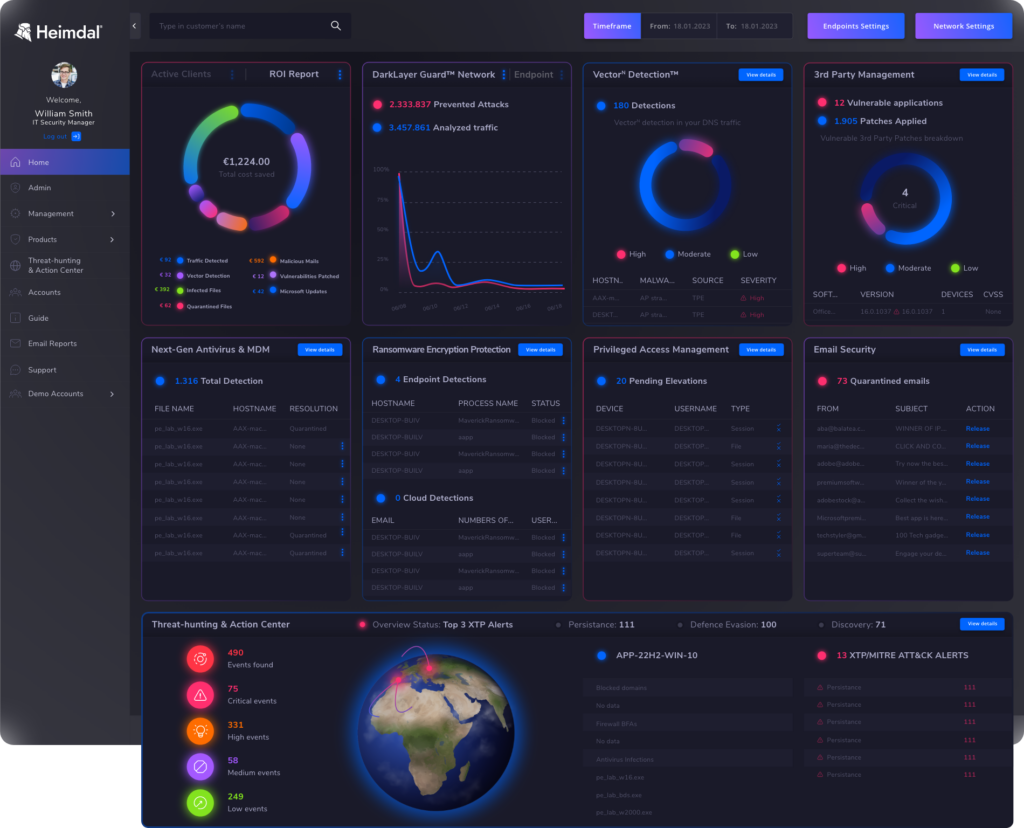
Key features
- Comprehensive approach – The industry’s widest Extended Detection and Response (XDR) suite seamlessly integrates 10 award-winning solutions into a single platform. This eliminates the need for multiple standalone tools, streamlining UEM efforts.
- Unification – Heimdal offers a single, unified console to manage all endpoint activities across multiple attack surfaces. This simplifies endpoint monitoring, patching, and overall security management.
- Leveraging AI/ML – Heimdal integrates advanced threat intelligence powered by MITRE ATT&CK techniques and crowd-sourced data. This ensures proactive endpoint protection through deep analysis and predictive insights.
- Cloud-native – Heimdal’s cloud-native infrastructure offers 99.9% uptime while maintaining exceptional system performance. Its architecture is built for scalability, enabling businesses to manage endpoints effectively without downtime.
- Granular control – More precise control over application access and remote desktop features ensures safer connections. This adds an extra layer of security for remote or hybrid work environments.
- Automation – this tool automates patch and asset management processes over multiple operating systems. It’s an ideal solution for managing diverse devices in enterprise environments.
- Integration – effortlessly works along Remote Monitoring and Management (RMM), Professional Services Automation (PSA), and other vendor tools, extending its capabilities to align with your existing tech stack.
Pricing
Heimdal offers customized Pricing that fits various business requirements and usage patterns. To see Heimdal in action before making any commitments, book a demo.
The integration of various Heimdal modules has resulted in a more cohesive and powerful security solution. Unlike the previous disjointed approach, where separate products might have operated independently, the interconnected modules of Heimdal provide enhanced protection. This synergy between modules ensures a higher level of security, addressing vulnerabilities more effectively and offering greater overall defense.
Source – 4Cambridge case study
Datto RMM
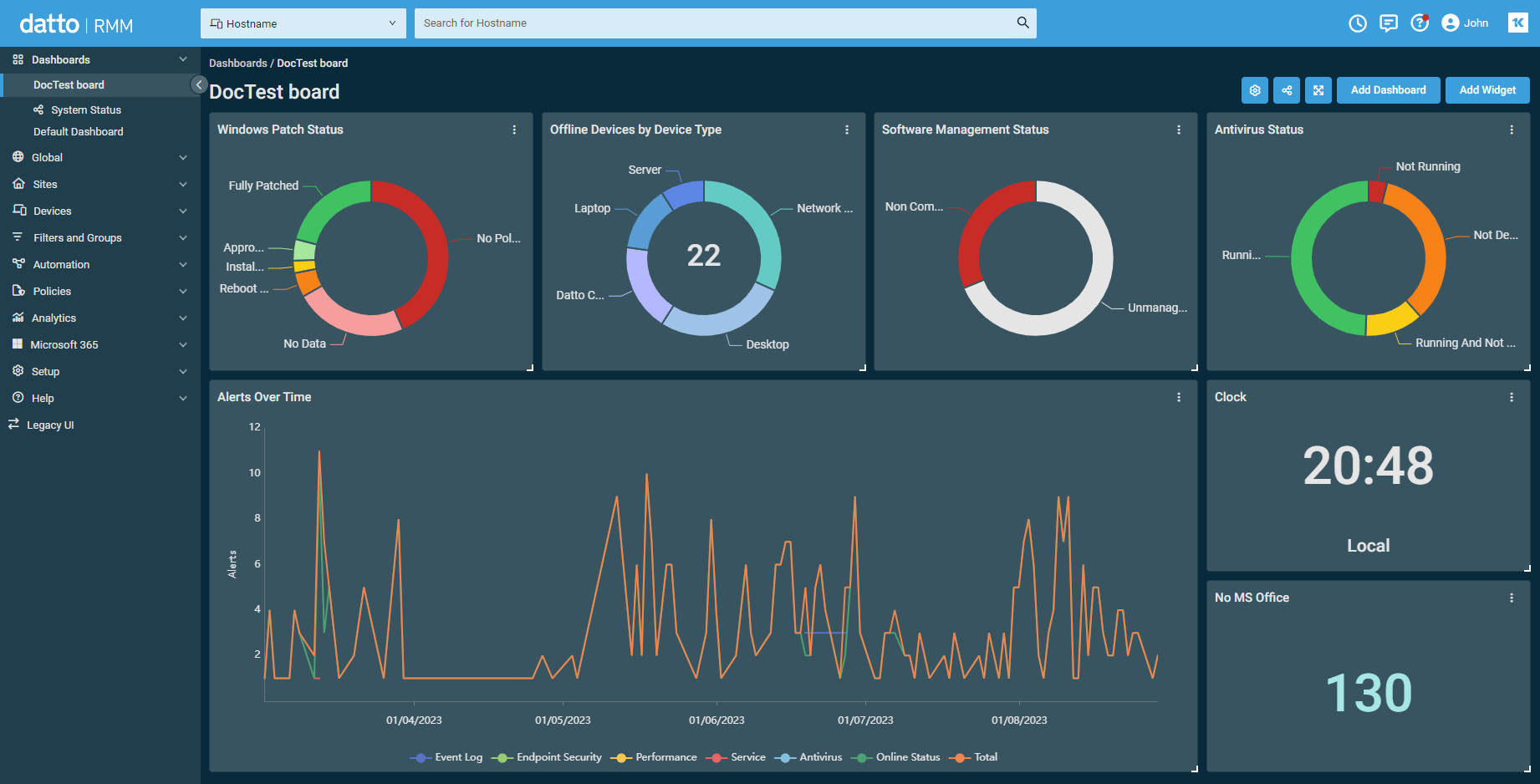
Datto RMM is a cloud-based platform that helps businesses monitor, manage, and secure all their devices.
It offers tools like one-click remote access to fix problems from anywhere, automated updates to keep software secure, and real-time monitoring to spot issues early. It’s popular for its ransomware protection and easy Microsoft 365 management.
Key features
- Ransomware detection and automated remediation.
- Unified Microsoft 365 management for user configuration and monitoring.
- Live chat support and remote troubleshooting.
Pricing
Custom pricing based on the number of endpoints; quotes available upon request.
User review
I find that the software can be slow at times. Especially when establishing the RMM agent on a client device that is a little older. But after the wait (5-30minutes) everything works as it should.
NinjaOne Endpoint Management
NinjaOne simplifies managing devices like laptops, desktops, and servers by providing a single platform for IT teams. It offers automated updates, easy software installation, and security tools to fix issues remotely.
Its real-time tracking ensures devices stay secure and healthy. Many users love its simple setup and helpful reports.
Key Features:
- Remote troubleshooting with full device control.
- Automated OS patching and app deployment.
- Detailed health and security reports with visual insights.
Pricing:
Custom pricing; free trial available.
User review
Unfortunately, I also see significant room for improvement in the Patch Management system. It often results in most of our managed devices showing a red or yellow status because updates are either pending or have failed. This is a major concern that needs to be addressed.
ManageEngine Desktop Central
ManageEngine Desktop Central helps businesses control and secure all their in-office and mobile devices from one place. It automates tasks like updating apps, installing software, and fixing bugs, thus saving IT teams’ time.
Its security features include blocking unauthorized USB devices and protecting corporate data. On the downside, beginners might have a hard time learning how to use it.
Key Features:
- Centralized dashboard for multi-device management.
- Support for multiple operating systems: Windows, Linux, MacOS, Android.
- Automated patch and OS deployment.
- Control over USB device usage.
Pricing:
Free version for SMBs; paid plans (Professional, Enterprise, UEM editions) available on request.
User review
The ManageEngine platform has a very intuitive UI, very helpful support staff, and an extremely competitive price point price.
Ivanti Unified Endpoint Manager
Ivanti UEM is a tool for managing all your work devices through one platform. It automates updates, moves data when employees change devices, and ensures security settings are always correct.
Companies love it for its ability to handle large numbers of devices, though the interface can feel a bit slow at times.
Key Features:
- Automatic OS migration and application patching.
- User profiles for seamless data migration.
- Centralized management console with customizable dashboards.
Pricing:
Quote-based pricing tailored to business needs.
User review
The documentation provided is for the previous versions and not for the updated one. It does not provide efficient solutions for zero-day malware. It requires improvements in IT and inventory reporting methods. It is inconsistent with window size and the user has to adjust and resize every time they use it as windows. Otherwise, we are very satisfied with this software and its capabilities.
Sure MDM
SureMDM by 42Gears is perfect for managing everything from smartphones to IoT gadgets. It provides real-time tracking, lets IT teams control devices remotely, and ensures apps are installed correctly.
Its security features keep business data safe, and it’s known for being budget-friendly. However, some users wish its reports were more detailed.
Key Features:
- Real-time device tracking and remote control.
- Policy enforcement and app distribution.
- Customizable reporting and compliance checks.
Pricing:
Starts at $3.99 per device/month; enterprise plans available.
User review
The slowness of the console, sometimes scripts will not work or deploy on EPS. and need to create new profiles when the scripts go corrupted. remote session sometimes slow.
Workspace One
VMware Workspace One combines managing devices and securing them into one system. It works for laptops, phones, and even rugged equipment used in tough environments.
Features like zero-trust security and automated device setups make it a nice choice for big companies. Smaller businesses might find it a bit expensive, though.
Key Features:
- Conditional access and compliance monitoring.
- AI-driven insights and automations.
- Support for mobile, desktop, and rugged devices.
Pricing:
Multiple subscription plans starting at $4 per device/month.
User review
The UI isn’t clean, it’s confusing to navigate, and installing software gets held up in a “pending queue”. There is no way to access this queue to understand what the errors could be. I contacted VMware Support and after weeks of troubleshooting they determined that every endpoint would have to have the Airwatch/Workspace ONE client re-installed. This is not helpful as there are hundreds of devices in our environment.
Microsoft Intune
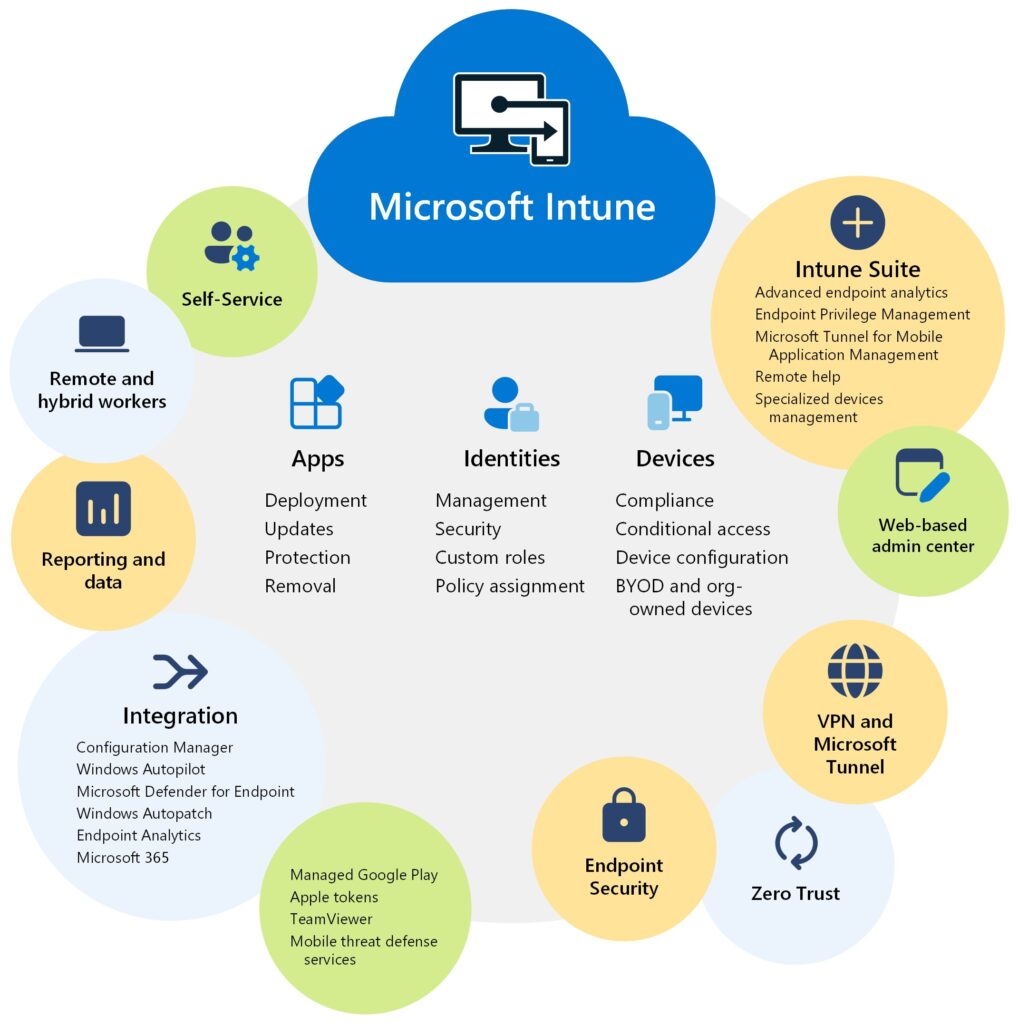
Microsoft Intune helps companies manage both work and personal devices, keeping data safe and apps updated. It connects smoothly with other Microsoft tools like Azure and Office, making it easy for businesses to use.
You can set rules for device use, track compliance, and manage apps across all devices. It’s great for companies already using Microsoft 365.
Key Features:
- Conditional access controls
- Integration with Azure Active Directory for access control.
- Comprehensive app and device lifecycle management.
Pricing:
Starts at $4 per user/month; bundled plans available with Microsoft 365.
User review
Can be expensive to get the full functionality if you are not on the correct licensing levels.
Hexnode UEM
Hexnode UEM is a simple and affordable way to manage phones, tablets, and laptops. It helps set up devices quickly, track them in real-time, and enforce rules like app restrictions or location-based security.
It’s perfect for small businesses or teams with limited budgets, and the customer support is highly appreciated.
Key Features:
- Remote device configuration and app management.
- Compliance monitoring with geofencing.
- Support for BYOD and corporate devices.
Pricing:
Its pricing is based on the number of devices. You pay only for the devices you manage with Hexnode UEM.
User review
This is no slight against Hexnode whatsoever, as it’s really not their fault, but iOS is so much more difficult to use with MDM. We strongly encourage customers to use Android devices, but sometimes they can’t be swayed. iOS works. It’s just so much more cumbersome than Android. Ironic, considering Apple devices supposedly “just work”.
IBM Security MaaS360
IBM MaaS360 uses AI to manage and protect work devices, making it ideal for companies with lots of gadgets or remote workers. It supports everything from laptops to wearables and even IoT devices.
Features like smart threat detection and detailed reports help businesses stay secure. It’s loved for its advanced tech but can sometimes feel slow to use.
Key Features:
- AI-powered threat detection and remediation.
- Support for IoT and wearable devices.
- Cloud-based management with actionable insights.
Pricing:
Starts at $4 per device/month.
User review
The cost of the product,I hope they would improve the UI functionalities and make it more user friendly.
Benefits of Unified Endpoint Management Software
Managing a mix of devices – personal and company-owned – can feel like juggling too many balls at once. In this picture, UEM is the steady hand that keeps everything secure, streamlined, and easy to manage.
Keeps all devices safe
Think of UEM as a smart security guard for all your devices. It makes sure they are safe from hackers by fixing weak spots and updating apps automatically.
For example, in case of a software vulnerability, UEM quickly applies patches to every device. This helps IT departments or Managed Service Providers to keep everything secure without breaking a sweat.
Makes work simple for everyone
Imagine your HR team announces onboarding 10 new colleagues next week. Instead of spending hours manually setting up each device with the right apps, security settings, and configurations, an UEM solution will take care of the whole process.
With UEM, every laptop arrives preloaded and ready to use, automating redundant processes and saving time for both IT and employees.
Helps you use personal devices safely
Some people like using their own phones or tablets for work because it’s convenient. UEM makes this possible – and safe – by keeping personal and work data separate.
For instance, if someone uses their personal phone to access work emails, UEM ensures that only the work data is secured. If that phone is lost or the employee changes jobs, it can wipe just the work data. The personal photos or apps remain untouched. This is especially useful for companies with a bring your own device (BYOD) work environment or for MSPs managing flexible work setups.
Makes sure rules are followed
Companies have to follow strict rules to keep data safe and meet compliance regulations. Using strong passwords and encrypting sensitive information are some of the most common requirements. UEM helps by applying these rules to every device automatically.
For example, a System Administrator shouldn’t have to check every phone or computer one by one for compliance. UEM makes sure all devices follow the same safety rules. This way, the company stays out of trouble and avoids big fines.
Shows what’s working and what’s not
UEM collects helpful information about devices, like which ones are running slow or need replacing.
For example, an MSP managing devices for several businesses can see which laptops are getting too old or which apps aren’t being used much. They can then suggest upgrades or changes to improve performance and save money for their clients.
Simplify your endpoint management and security today
Unified Endpoint Management software makes it easy to manage devices, boost security, and adapt to modern setups like BYOD and hybrid teams.
Most UEM tools focus only on device management, but solutions like Heimdal take it further by adding advanced cybersecurity features.
With a single platform for endpoint management and security, you can cut costs, simplify operations, and stay protected against evolving threats. Whether you’re handling laptops, IoT devices, or mobile phones, choosing the right UEM solution keeps your business secure, efficient, and future-ready.
Frequently Asked Questions (FAQs)
What is UEM software?
UEM is a tool that helps people manage all their devices like phones, computers, and tablets from one place. It replaces older security tools like MDM and Enterprise Mobility Management (EMM), making it easier to control and keep track of devices.
What is the difference between EDR and UEM?
EDR (Endpoint Detection and Response) is mainly focused on finding and fixing security problems. It watches over devices to catch any potential threats. UEM, on the other hand, is more about managing devices, making sure they work properly, and following the right rules.
What is the difference between MDM and UEM?
MDM is cheaper but offers fewer features than UEM or EMM. MDM usually works by installing software on your computer, while UEM and EMM are cloud-based, meaning you can use them from anywhere. Which one you choose depends on what your business needs.
If you liked this article, follow us on LinkedIn, Reddit, X, Facebook, and Youtube.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









